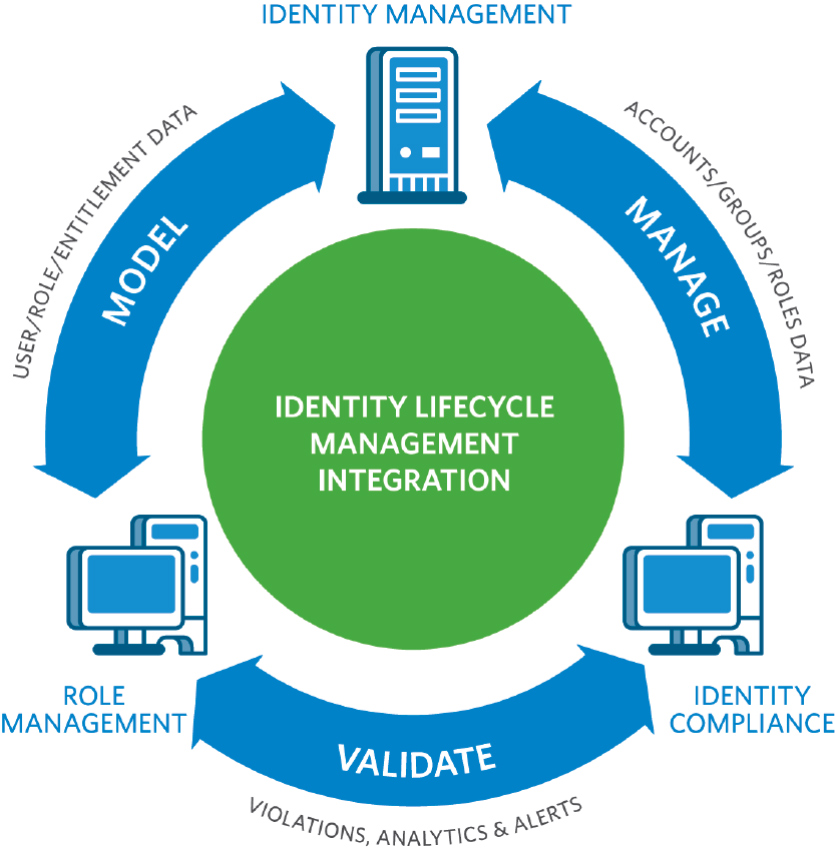
The Importance of Identity Access Solutions in Modern Cybersecurity
In today’s digital landscape, where data breaches and cyber threats are on the rise, the need for robust identity access solutions has never been more critical. An identity access solution is a framework that manages and controls user identities and their access to various resources within an organisation’s IT infrastructure.
One of the key benefits of implementing an identity access solution is enhanced security. By enforcing strict access controls based on user roles and permissions, organisations can significantly reduce the risk of unauthorised access to sensitive data and systems. This helps prevent data breaches and insider threats, safeguarding valuable information from falling into the wrong hands.
Moreover, identity access solutions promote compliance with regulations such as GDPR, HIPAA, and PCI DSS by ensuring that only authorised users have access to confidential data. This not only helps avoid costly fines but also builds trust with customers who entrust their personal information to the organisation.
Another advantage of identity access solutions is improved productivity and efficiency. By streamlining the process of granting and revoking access rights, organisations can reduce administrative overheads associated with managing user accounts manually. This allows IT teams to focus on more strategic tasks while ensuring that employees have timely access to the resources they need to perform their roles effectively.
Furthermore, as businesses increasingly adopt cloud services and mobile technologies, identity access solutions play a crucial role in enabling secure remote access for employees working from anywhere. By implementing multi-factor authentication and single sign-on capabilities, organisations can provide a seamless yet secure user experience across various devices and platforms.
In conclusion, investing in an effective identity access solution is essential for protecting sensitive data, maintaining regulatory compliance, enhancing operational efficiency, and enabling secure remote work practices. As cyber threats continue to evolve, organisations must prioritise identity management as a cornerstone of their cybersecurity strategy to mitigate risks effectively.
9 Essential Tips for Enhancing Your Identity Access Solution
- Implement multi-factor authentication for added security.
- Regularly review and update user access permissions.
- Utilise role-based access control to manage user privileges effectively.
- Monitor user activity and set up alerts for suspicious behaviour.
- Ensure strong password policies are in place for all users.
- Encrypt sensitive data to protect it from unauthorised access.
- Train employees on best practices for maintaining secure identities.
- Integrate identity access solutions with other security tools for comprehensive protection.
- Conduct regular audits to assess the effectiveness of your identity access solution.
Implement multi-factor authentication for added security.
Enhancing security measures within an organisation’s IT infrastructure, implementing multi-factor authentication is a crucial step in bolstering identity access solutions. By requiring users to provide multiple forms of verification before granting access, such as a password combined with a unique code sent to their mobile device, organisations significantly reduce the risk of unauthorised access. This additional layer of security adds an extra barrier against cyber threats and helps safeguard sensitive data from potential breaches, reinforcing the overall integrity of the identity access solution.
Regularly review and update user access permissions.
Regularly reviewing and updating user access permissions is a crucial practice in maintaining a secure identity access solution. By conducting periodic audits of user permissions, organisations can ensure that employees have the appropriate level of access needed to perform their roles effectively while also preventing unauthorised entry to sensitive data or systems. This proactive approach helps in identifying and rectifying any inconsistencies or vulnerabilities in access controls, ultimately strengthening the overall security posture of the organisation. Regular reviews also support compliance efforts by aligning user access permissions with regulatory requirements and best practices in cybersecurity.
Utilise role-based access control to manage user privileges effectively.
Utilising role-based access control is a fundamental tip in implementing an effective identity access solution. By assigning access rights based on predefined roles within an organisation, businesses can manage user privileges more efficiently and securely. This approach ensures that users only have access to the resources necessary for their specific job functions, reducing the risk of unauthorised access to sensitive data. Role-based access control not only simplifies the process of granting and revoking permissions but also enhances overall security posture by enforcing least privilege principles. Organizations can tailor access levels to align with job responsibilities, thereby minimising potential security vulnerabilities and maintaining a robust defence against cyber threats.
Monitor user activity and set up alerts for suspicious behaviour.
To enhance the security of your identity access solution, it is crucial to monitor user activity closely and establish alerts for any suspicious behaviour. By actively tracking user actions within the system, such as login attempts, file access, or configuration changes, organisations can quickly identify anomalous activities that may indicate a potential security threat. Setting up alerts for unusual patterns or deviations from normal user behaviour enables prompt detection and response to suspicious incidents, helping to prevent security breaches and protect sensitive data from unauthorised access.
Ensure strong password policies are in place for all users.
It is crucial to enforce robust password policies for all users as a fundamental aspect of an effective identity access solution. Strong passwords act as the first line of defence against unauthorised access to sensitive data and systems. By requiring users to create complex passwords that include a mix of letters, numbers, and special characters, organisations can significantly enhance security posture and reduce the risk of password-related breaches. Regularly updating passwords and implementing measures such as password expiry and account lockout policies further strengthen the overall security framework, ensuring that only authorised individuals have access to critical resources.
Encrypt sensitive data to protect it from unauthorised access.
To enhance the security of your identity access solution, it is crucial to encrypt sensitive data. Encryption acts as a powerful safeguard by transforming data into a secure format that can only be accessed with the appropriate decryption key. This measure ensures that even if unauthorised users gain access to the data, they cannot decipher its contents, thereby protecting sensitive information from falling into the wrong hands. Encrypting sensitive data is a fundamental practice in maintaining the integrity and confidentiality of your organisation’s assets within the identity access framework.
Train employees on best practices for maintaining secure identities.
It is crucial to train employees on best practices for maintaining secure identities within an organisation’s identity access solution. By educating staff on the importance of creating strong, unique passwords, avoiding sharing login credentials, and recognising phishing attempts, businesses can significantly enhance their overall security posture. Employee training plays a vital role in mitigating insider threats and ensuring that individuals understand their role in safeguarding sensitive data and systems. Regular training sessions and awareness campaigns can empower employees to be proactive in protecting their identities and contribute to a culture of cybersecurity awareness across the organisation.
Integrate identity access solutions with other security tools for comprehensive protection.
To maximise the effectiveness of identity access solutions, it is advisable to integrate them with other security tools to achieve comprehensive protection. By combining identity access solutions with technologies such as intrusion detection systems, security information and event management (SIEM) platforms, and endpoint protection tools, organisations can create a layered defence strategy that enhances visibility and control over their IT environment. This integration enables proactive threat detection, rapid incident response, and a holistic approach to cybersecurity that strengthens overall resilience against evolving cyber threats.
Conduct regular audits to assess the effectiveness of your identity access solution.
Regular audits are essential to evaluate the efficacy of your identity access solution. By conducting routine assessments, organisations can identify any gaps or vulnerabilities in their access controls and address them promptly. Audits help ensure that user permissions align with business requirements and security policies, reducing the risk of unauthorised access and potential data breaches. Additionally, regular evaluations provide insights into user activity patterns, helping to detect anomalies or suspicious behaviour that may indicate a security threat. Overall, consistent audits play a crucial role in maintaining the integrity and robustness of an organisation’s identity access solution.