The Importance of Industrial Network Security
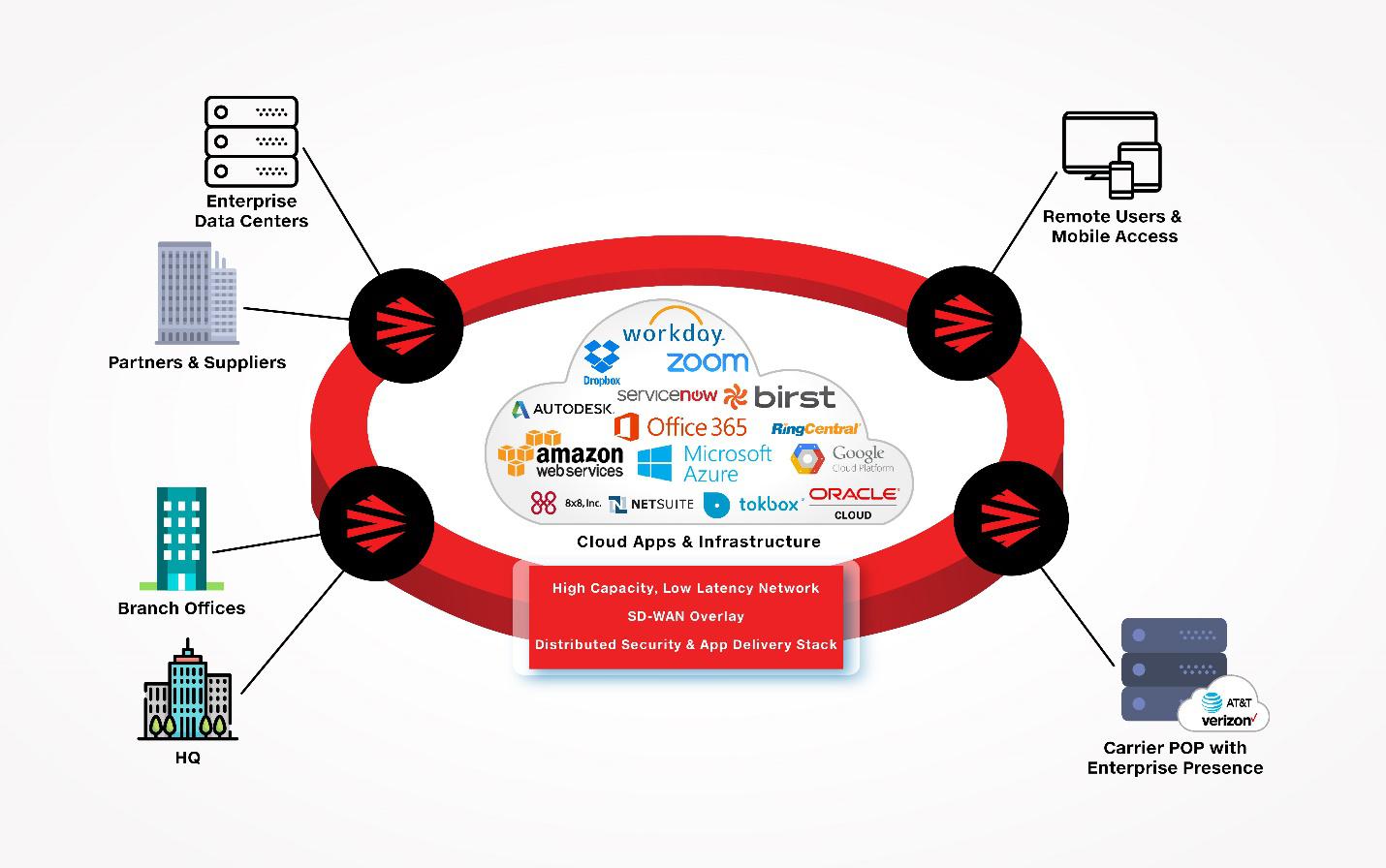
Industrial networks play a crucial role in the operations of various sectors such as manufacturing, energy, transportation, and more. These networks are responsible for controlling critical infrastructure and machinery that keep our society running smoothly. However, with the rise of interconnected systems and the Internet of Things (IoT), industrial network security has become a paramount concern.
Ensuring the security of industrial networks is essential to prevent cyber threats that can have devastating consequences. A breach in industrial network security can lead to production downtime, equipment damage, safety hazards, financial losses, and even potential harm to human lives.
Challenges in Industrial Network Security
Industrial networks face unique challenges compared to traditional IT networks. These challenges include:
- Legacy Systems: Many industrial facilities still operate using legacy systems that may not have built-in security features or are difficult to update.
- Interconnected Devices: The proliferation of IoT devices in industrial environments increases the attack surface and introduces new vulnerabilities.
- Downtime Impact: Unlike IT systems where downtime can be costly, in industrial settings, downtime can lead to significant production losses and safety risks.
- Regulatory Compliance: Industries such as energy and healthcare are subject to strict regulatory requirements for data protection and network security.
Best Practices for Industrial Network Security
To enhance industrial network security and mitigate risks, organisations should implement the following best practices:
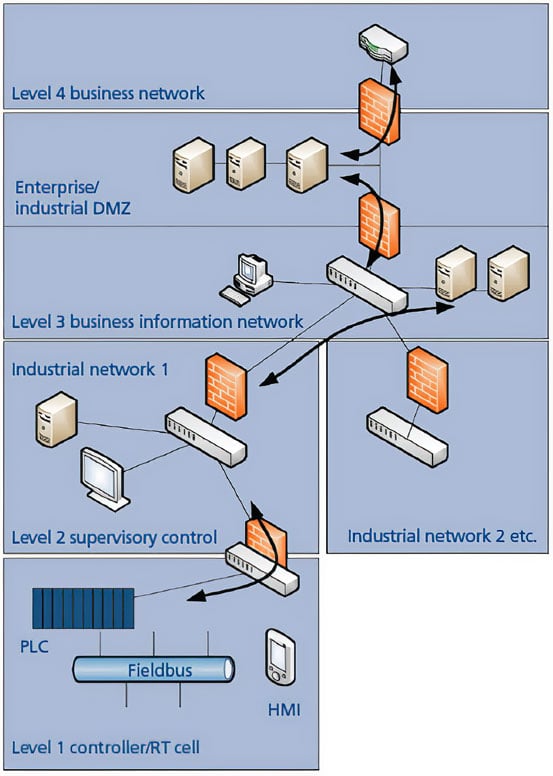
- Segmentation: Divide the network into separate zones to contain potential breaches and limit their impact.
- Access Control: Enforce strict access controls based on roles and responsibilities to prevent unauthorised access.
- Patch Management: Regularly update software and firmware to address known vulnerabilities and improve system resilience.
- Monitoring & Detection: Implement real-time monitoring tools to detect anomalies or suspicious activities on the network.
- Employee Training: Educate employees about cybersecurity best practices and raise awareness about social engineering tactics used by cybercriminals.
The Future of Industrial Network Security
As technology continues to advance, so do the threats targeting industrial networks. It is crucial for organisations to stay proactive in their approach to security by investing in robust defences, conducting regular risk assessments, and staying informed about emerging cyber threats.
In conclusion, safeguarding industrial network security is not just a matter of protecting data; it is about safeguarding critical infrastructure and ensuring operational continuity. By prioritising cybersecurity measures tailored to industrial environments, organisations can mitigate risks and build a resilient defence against evolving cyber threats.
Essential FAQs on Enhancing Industrial Network Security: Understanding Threats, Safeguarding Legacy Systems, and Ensuring Compliance
- What is industrial network security and why is it important?
- What are the common threats to industrial networks?
- How can I secure legacy systems in industrial environments?
- What role does employee training play in enhancing industrial network security?
- How can segmentation help improve the security of industrial networks?
- What are the best practices for monitoring and detecting anomalies in industrial networks?
- How do regulatory compliance requirements impact industrial network security?
What is industrial network security and why is it important?
Industrial network security refers to the protection of interconnected systems and devices within industrial environments, such as manufacturing plants, power stations, and transportation systems, from cyber threats and unauthorised access. It is crucial for maintaining the integrity, confidentiality, and availability of critical infrastructure components that rely on these networks to function efficiently. Industrial network security plays a vital role in safeguarding against potential cyber attacks that could disrupt operations, compromise sensitive data, or pose safety risks to employees and the public. By implementing robust security measures tailored to industrial settings, organisations can mitigate vulnerabilities and ensure the continuous operation of essential services while upholding regulatory compliance standards.
What are the common threats to industrial networks?
Common threats to industrial networks encompass a range of cybersecurity risks that pose significant challenges to the operational integrity of critical infrastructure. Some prevalent threats include malware attacks, such as ransomware and viruses, which can disrupt industrial processes and compromise sensitive data. Additionally, targeted cyber-attacks aimed at exploiting vulnerabilities in industrial control systems (ICS) can lead to system manipulation or sabotage. Other common threats include insider threats, where authorised personnel misuse their access privileges, and phishing scams that trick employees into divulging confidential information. Understanding and mitigating these common threats is essential for safeguarding the security and resilience of industrial networks in the face of evolving cyber risks.
How can I secure legacy systems in industrial environments?
Securing legacy systems in industrial environments presents a significant challenge due to their outdated technology and limited security features. To enhance the security of these critical systems, organisations can implement strategies such as network segmentation, where legacy systems are isolated from newer infrastructure to prevent potential vulnerabilities from spreading. Additionally, regular security assessments and updates to software and firmware can help address known vulnerabilities and strengthen the overall resilience of legacy systems. Training employees on cybersecurity best practices specific to legacy technology is also essential in creating a culture of awareness and proactive defence against potential threats in industrial environments.
What role does employee training play in enhancing industrial network security?
Employee training plays a pivotal role in enhancing industrial network security by equipping staff with the knowledge and skills necessary to identify and respond to cybersecurity threats effectively. In industrial environments, where human error can have serious consequences, well-trained employees act as the first line of defence against potential breaches. Training programmes educate workers on best practices for data protection, safe handling of sensitive information, and recognising social engineering tactics used by cyber attackers. By fostering a culture of cybersecurity awareness and responsibility among employees, organisations can significantly reduce the likelihood of security incidents and strengthen the overall resilience of their industrial networks.
How can segmentation help improve the security of industrial networks?
Segmentation plays a crucial role in enhancing the security of industrial networks by creating isolated zones within the network infrastructure. By segmenting the network, organisations can limit the spread of potential cyber threats and contain any breaches that may occur. This approach helps to prevent attackers from moving laterally across the network and gaining access to critical systems or data. Additionally, segmentation allows for more granular control over access permissions, ensuring that only authorised users and devices can interact with specific parts of the network. Ultimately, segmentation helps to increase overall network resilience and reduce the impact of security incidents on industrial operations.
What are the best practices for monitoring and detecting anomalies in industrial networks?
When it comes to monitoring and detecting anomalies in industrial networks, implementing best practices is crucial to maintaining a secure environment. One key practice is to utilise real-time monitoring tools that can continuously track network traffic and system activities for any deviations from normal behaviour. Setting up alerts and notifications for unusual patterns or suspicious activities can help in identifying potential threats promptly. Additionally, implementing intrusion detection systems (IDS) and intrusion prevention systems (IPS) can provide an added layer of security by actively monitoring network traffic and blocking malicious activities. Regularly analysing logs and conducting network audits are also essential practices to ensure the integrity of industrial networks and swiftly address any anomalies that may arise.
How do regulatory compliance requirements impact industrial network security?
Regulatory compliance requirements have a significant impact on industrial network security by setting standards and guidelines that organisations must adhere to in order to protect sensitive data and maintain the integrity of their networks. Industries such as manufacturing, energy, and healthcare are subject to stringent regulations that mandate specific security measures to safeguard critical infrastructure. Failure to comply with these regulations can result in severe penalties and reputational damage. Therefore, organisations operating in these sectors must invest in robust security practices, regular audits, and compliance assessments to ensure that their industrial networks meet the necessary regulatory standards and remain secure against potential cyber threats.