The Importance of Cloud Cyber Security
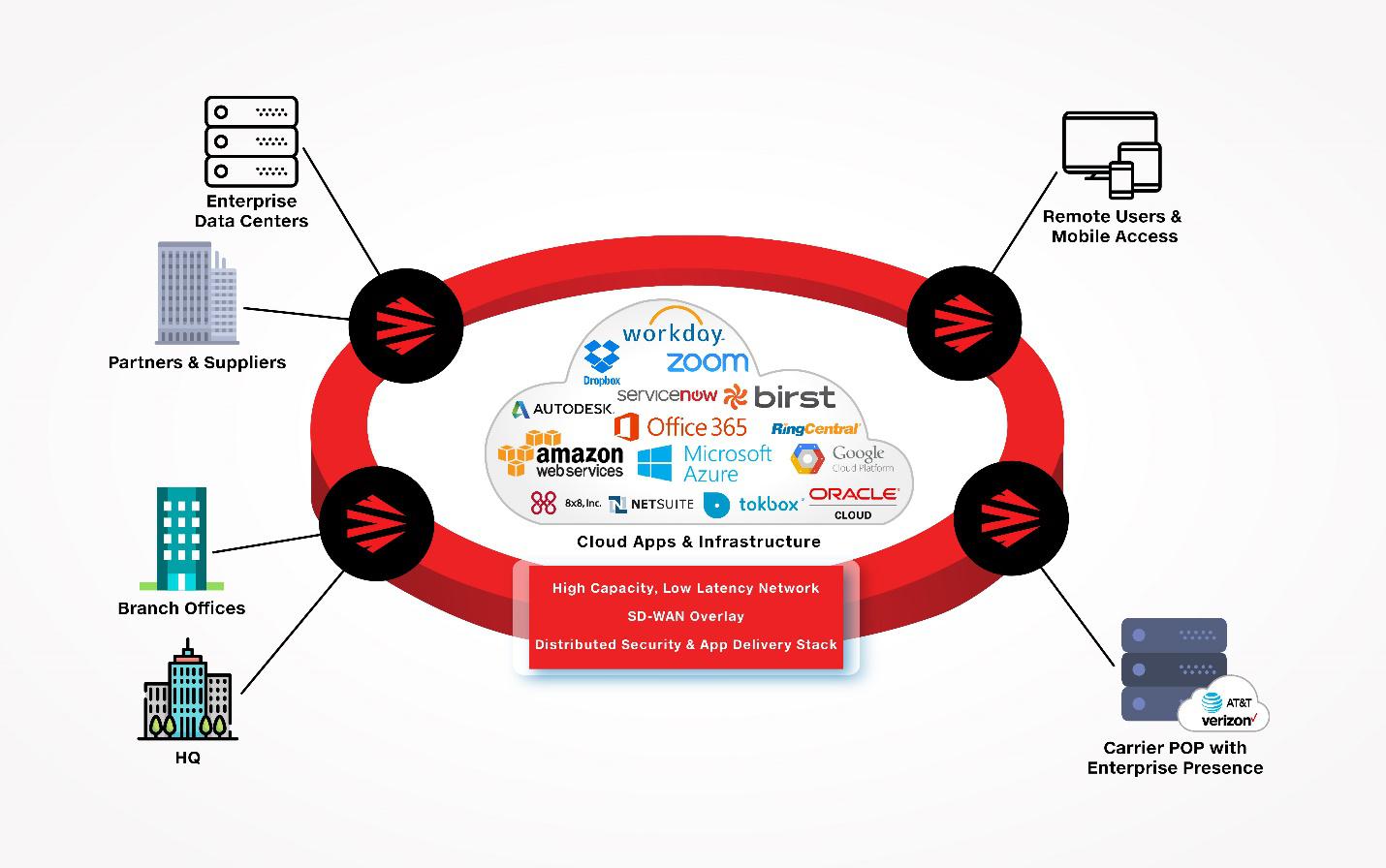
In today’s digital age, the adoption of cloud computing has revolutionised the way businesses operate. The flexibility, scalability, and cost-effectiveness of cloud services have made them indispensable for organisations worldwide. However, alongside these benefits comes the critical need for robust cyber security measures to protect sensitive data stored in the cloud.
Risks in the Cloud Environment
Cloud environments are not immune to cyber threats. In fact, they present unique challenges that traditional on-premises systems may not encounter. Some common risks associated with cloud computing include:
- Data Breaches: Unauthorized access to sensitive information stored in the cloud.
- Misconfigurations: Errors in cloud configurations that can expose data to vulnerabilities.
- Account Hijacking: Unauthorized users gaining access to legitimate cloud accounts.
- Denial of Service (DoS) Attacks: Overloading cloud services to disrupt operations.
The Role of Cloud Cyber Security
To mitigate these risks and safeguard data in the cloud, organisations must implement comprehensive cyber security measures tailored to their specific needs. Cloud cyber security involves a multi-layered approach that includes:
- Data Encryption: Encrypting data both at rest and in transit to protect it from unauthorised access.
- Access Control: Implementing strict access controls and authentication mechanisms to ensure only authorised users can access data.
- Regular Auditing and Monitoring: Monitoring cloud environments for suspicious activities and conducting regular audits to identify potential vulnerabilities.
- Incident Response Planning: Developing a robust incident response plan to address security breaches promptly and effectively.
The Future of Cloud Cyber Security
As technology continues to evolve, so do cyber threats. The future of cloud cyber security lies in proactive risk management, artificial intelligence-driven threat detection, and increased collaboration between organisations and cloud service providers. By staying vigilant and investing in cutting-edge security solutions, businesses can confidently harness the power of the cloud while keeping their data secure.
Essential FAQs on Cloud Cyber Security: Understanding Threats, Protection, and Compliance
- What is cloud cyber security?
- How secure is data in the cloud?
- What are the common threats to cloud security?
- How can encryption protect data in the cloud?
- What is multi-factor authentication and why is it important for cloud security?
- How do you ensure compliance with regulations when using cloud services?
- What measures can organisations take to prevent data breaches in the cloud?
What is cloud cyber security?
Cloud cyber security refers to the set of measures and protocols designed to protect data, applications, and infrastructure stored in cloud environments from cyber threats and attacks. It encompasses a range of strategies, including encryption, access control, monitoring, and incident response planning, aimed at ensuring the confidentiality, integrity, and availability of data in the cloud. Cloud cyber security is essential for organisations leveraging cloud services to safeguard sensitive information and maintain compliance with regulatory requirements. By implementing robust security practices tailored to the unique challenges of cloud computing, businesses can mitigate risks and confidently embrace the benefits of cloud technology.
How secure is data in the cloud?
When it comes to the frequently asked question, “How secure is data in the cloud?”, the security of data stored in the cloud depends on various factors. Cloud service providers invest heavily in implementing robust security measures, such as data encryption, access controls, and regular monitoring, to protect sensitive information. However, the ultimate security of data in the cloud also relies on how well organisations configure and manage their cloud environments. By following best practices in cloud security, including strong authentication methods and regular audits, businesses can enhance the security of their data in the cloud and mitigate potential risks effectively.
What are the common threats to cloud security?
When it comes to cloud security, understanding the common threats is crucial for safeguarding sensitive data stored in cloud environments. Some of the most prevalent threats to cloud security include data breaches, caused by unauthorised access to confidential information; misconfigurations, which can expose vulnerabilities in cloud settings; account hijacking, where malicious actors gain control of legitimate cloud accounts; and denial of service (DoS) attacks, aimed at disrupting cloud services by overwhelming them with traffic. By being aware of these common threats and implementing robust security measures, organisations can better protect their data and mitigate the risks associated with cloud computing.
How can encryption protect data in the cloud?
Encryption plays a crucial role in safeguarding data stored in the cloud by rendering it unreadable to unauthorised users. When data is encrypted before being uploaded to the cloud, it is transformed into a scrambled format that can only be decrypted with the corresponding encryption key. This means that even if a malicious actor gains access to the encrypted data, they would not be able to make sense of it without the decryption key. By implementing robust encryption protocols, organisations can ensure that their sensitive information remains secure and confidential, providing an additional layer of protection against potential data breaches in the cloud environment.
What is multi-factor authentication and why is it important for cloud security?
Multi-factor authentication (MFA) is a security process that requires users to provide two or more forms of verification before gaining access to a system or application. This typically involves something the user knows (such as a password), something they have (like a mobile device for receiving codes), or something they are (biometric data). MFA plays a crucial role in cloud security by adding an extra layer of protection against unauthorised access. By requiring multiple factors for authentication, MFA reduces the risk of compromised credentials and enhances overall security posture in cloud environments. Implementing MFA helps to safeguard sensitive data stored in the cloud and strengthens defences against cyber threats like phishing attacks and credential theft.
How do you ensure compliance with regulations when using cloud services?
Ensuring compliance with regulations when using cloud services is a crucial aspect of maintaining data security and integrity. Organisations must adopt a proactive approach to address this concern by carefully selecting cloud service providers that adhere to relevant regulatory requirements. Conducting thorough due diligence on the provider’s compliance certifications, data protection policies, and security measures is essential. Additionally, implementing strong contractual agreements that outline data handling practices, audit rights, and breach notification procedures can help enforce compliance standards. Regular monitoring, audits, and assessments of the cloud environment are also necessary to verify ongoing adherence to regulations and mitigate potential risks. By prioritising compliance as a fundamental component of their cloud strategy, businesses can confidently navigate the complex landscape of cloud cyber security while meeting regulatory obligations.
What measures can organisations take to prevent data breaches in the cloud?
Organisations can implement several measures to prevent data breaches in the cloud. Firstly, employing strong encryption techniques to safeguard data both at rest and in transit is crucial. Access control mechanisms should be implemented to ensure that only authorised personnel can access sensitive information stored in the cloud. Regular auditing and monitoring of cloud environments can help detect any unusual activities or potential vulnerabilities promptly. Additionally, conducting comprehensive security training for employees to raise awareness about best practices and potential threats can significantly enhance data protection in the cloud. By adopting a multi-layered approach that combines technical safeguards with employee education, organisations can strengthen their cyber security posture and reduce the risk of data breaches in the cloud.