The Importance of Directory Services Security Solutions
In today’s digital age, organisations rely heavily on directory services to manage user identities, access permissions, and other critical information. However, with the increasing frequency and sophistication of cyber threats, ensuring the security of directory services has become paramount.
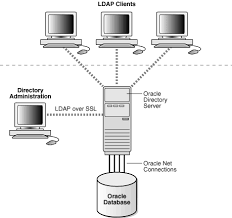
Directory services security solutions play a crucial role in safeguarding sensitive data stored within directories such as Active Directory or LDAP. These solutions are designed to detect and prevent unauthorised access, mitigate insider threats, and ensure compliance with regulatory requirements.
Key Components of Directory Services Security Solutions:
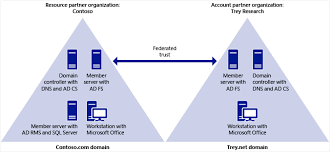
- Authentication Controls: Implementing multi-factor authentication, password policies, and biometric authentication to verify user identities and prevent unauthorised access.
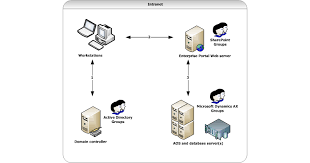
- Access Management: Enforcing least privilege access controls to restrict users’ permissions based on their roles and responsibilities within the organisation.
- Audit Trail Monitoring: Tracking and logging all changes made to directory services to detect suspicious activities and facilitate forensic investigations.
- Encryption: Encrypting data at rest and in transit to protect it from interception or theft by malicious actors.
- Vulnerability Management: Regularly scanning for vulnerabilities in directory services infrastructure and applying patches to address security gaps.
The Benefits of Implementing Directory Services Security Solutions:
By investing in robust directory services security solutions, organisations can enjoy the following benefits:
- Enhanced Data Protection: Safeguarding sensitive information stored in directories from unauthorised access or data breaches.
- Improved Compliance: Meeting regulatory requirements such as GDPR, HIPAA, or PCI DSS by implementing security controls and audit mechanisms.
- Risk Mitigation: Minimising the risk of data loss, financial damage, or reputational harm resulting from security incidents.
- What is the importance of directory services security solutions?
- How do directory services security solutions help in safeguarding sensitive data?
- What are the key components of directory services security solutions?
- How can authentication controls enhance the security of directory services?
- What role does access management play in ensuring secure directory services?
- Why is audit trail monitoring essential for maintaining the integrity of directory services?
- In what ways does encryption contribute to securing data within directory services?
- Why is vulnerability management critical for the overall security posture of directory services?
…
Securing Core Information Assets: A Guide to Directory Services Security Solutions
What is the importance of directory services security solutions?
The importance of directory services security solutions lies in their fundamental role in safeguarding sensitive data and ensuring the integrity of organisational IT infrastructures. By implementing robust security measures within directory services such as Active Directory or LDAP, businesses can effectively control access permissions, authenticate user identities, and monitor activities to prevent unauthorised access and data breaches. These solutions not only protect valuable information from external threats but also help organisations comply with regulatory requirements and maintain a secure environment for their digital assets. Overall, directory services security solutions are essential for mitigating risks, enhancing data protection, and upholding the trust of stakeholders in the security posture of an organisation.
How do directory services security solutions help in safeguarding sensitive data?
Directory services security solutions play a vital role in safeguarding sensitive data by implementing a range of protective measures. These solutions help in ensuring the confidentiality, integrity, and availability of critical information stored within directory services such as Active Directory or LDAP. By enforcing strong authentication controls, access management policies, and encryption protocols, directory services security solutions prevent unauthorised access to sensitive data. Additionally, audit trail monitoring features enable organisations to track and investigate any suspicious activities that may compromise data security. By proactively identifying vulnerabilities and implementing robust security measures, directory services security solutions effectively mitigate risks and enhance the overall protection of sensitive data from potential cyber threats.
What are the key components of directory services security solutions?
Directory services security solutions encompass several key components essential for ensuring the protection and integrity of sensitive data stored within directories. These components include robust authentication controls, such as multi-factor authentication and password policies, to verify user identities and prevent unauthorised access. Access management features enforce least privilege access controls, limiting users’ permissions based on their roles within the organisation. Audit trail monitoring capabilities track and log all changes made to directory services, enabling the detection of suspicious activities and facilitating forensic investigations. Encryption measures protect data at rest and in transit from interception or theft, while vulnerability management involves regular scanning for security gaps and applying patches to mitigate risks effectively. These components collectively form a comprehensive security framework that helps organisations mitigate threats and maintain the confidentiality of their directory services.
How can authentication controls enhance the security of directory services?
Authentication controls play a pivotal role in enhancing the security of directory services by verifying the identities of users accessing the system. Implementing robust authentication measures such as multi-factor authentication, password policies, and biometric verification adds layers of security that make it significantly harder for unauthorised users to gain access. By requiring users to provide multiple forms of identification before granting access, authentication controls help prevent credential theft and unauthorised access attempts. This proactive approach not only strengthens the overall security posture of directory services but also ensures that only legitimate users with valid credentials can interact with sensitive data stored within the directory.
What role does access management play in ensuring secure directory services?
Access management plays a pivotal role in ensuring secure directory services by controlling and monitoring user permissions within the system. By implementing access management policies, organisations can enforce the principle of least privilege, granting users only the permissions necessary to perform their specific tasks. This helps prevent unauthorised access to sensitive data and reduces the risk of insider threats. Access management also allows for real-time monitoring of user activities, enabling administrators to quickly detect and respond to any suspicious behaviour. Overall, effective access management is essential for maintaining the integrity and security of directory services, safeguarding critical information from potential security breaches.
Why is audit trail monitoring essential for maintaining the integrity of directory services?
Audit trail monitoring is essential for maintaining the integrity of directory services due to its critical role in detecting and investigating security incidents. By tracking and logging all changes made to directory services, audit trail monitoring provides a detailed record of user activities, configuration modifications, and access attempts. This visibility allows organisations to identify unauthorized or suspicious actions, such as privilege escalation or data tampering, in real-time. Moreover, audit trail monitoring facilitates compliance with regulatory requirements by providing a comprehensive audit trail that can be used for forensic analysis and reporting. Ultimately, by implementing robust audit trail monitoring practices, organisations can enhance the security posture of their directory services infrastructure and proactively mitigate potential threats to data integrity and confidentiality.
In what ways does encryption contribute to securing data within directory services?
Encryption plays a vital role in enhancing the security of data within directory services by ensuring that sensitive information is protected from unauthorised access. By encrypting data at rest and in transit, organisations can prevent malicious actors from intercepting or stealing confidential data stored in directories such as Active Directory or LDAP. Encryption transforms the plaintext data into ciphertext using complex algorithms, making it unreadable without the corresponding decryption key. This means that even if an attacker gains access to the encrypted data, they cannot decipher it without the proper authentication credentials. As a result, encryption helps to maintain the confidentiality and integrity of data within directory services, providing an additional layer of defence against potential security breaches and data leaks.
Why is vulnerability management critical for the overall security posture of directory services?
Vulnerability management is a critical aspect of maintaining the overall security posture of directory services due to its proactive approach in identifying and addressing potential security weaknesses. By regularly scanning for vulnerabilities within directory services infrastructure, organisations can stay ahead of cyber threats and prevent exploitation by malicious actors. Timely patching of identified vulnerabilities helps to minimise the risk of unauthorised access, data breaches, and other security incidents that could compromise the integrity and confidentiality of sensitive information stored in directories. Effective vulnerability management not only enhances the resilience of directory services but also ensures compliance with regulatory requirements, ultimately bolstering the organisation’s overall security defences against evolving cyber threats.