The Importance of Privileged Account Management
In today’s digital landscape, where cyber threats are constantly evolving, the protection of sensitive data and critical systems is paramount. One crucial aspect of cybersecurity that often gets overlooked is privileged account management.
Privileged accounts refer to user accounts with elevated permissions that allow users to access and control sensitive resources within an organisation’s IT infrastructure. These accounts are highly sought after by cyber attackers because they provide unrestricted access to critical systems and data.
Why is Privileged Account Management Important?
Effective privileged account management is essential for maintaining the security and integrity of an organisation’s IT environment. Here are some key reasons why it is crucial:
- Minimising Security Risks: By implementing strict controls and monitoring mechanisms for privileged accounts, organisations can reduce the risk of insider threats and external attacks that exploit these high-level permissions.
- Preventing Data Breaches: Privileged accounts often have access to sensitive data repositories. Proper management helps prevent unauthorised access to this information, reducing the likelihood of data breaches.
- Ensuring Compliance: Many regulatory standards, such as GDPR and PCI DSS, require organisations to implement robust privileged account management practices to ensure data protection and compliance with industry regulations.
- Mitigating Insider Threats: Insiders with malicious intent or compromised credentials pose a significant threat to an organisation’s security. Effective privileged account management can help detect and prevent insider threats before they cause harm.
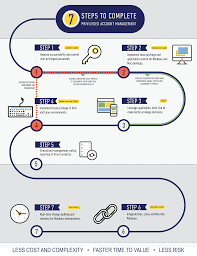
Best Practices for Privileged Account Management
To enhance the security posture of your organisation, consider implementing the following best practices for privileged account management:
- Implement Least Privilege Access: Only grant privileges necessary for users to perform their job functions. Avoid assigning excessive permissions that could be exploited by attackers.
- Regularly Rotate Passwords: Enforce regular password rotations for privileged accounts to reduce the risk of credential theft or misuse.
- Monitor and Audit Account Activity: Implement robust monitoring tools to track privileged account usage and detect any suspicious activities in real-time.
- Use Multi-Factor Authentication (MFA): Enhance security by requiring multiple authentication factors for accessing privileged accounts, adding an extra layer of protection against unauthorised access.
- Educate Employees: Conduct regular training sessions to raise awareness about the importance of secure password practices and the risks associated with mishandling privileged accounts.
In conclusion, prioritising privileged account management is essential for safeguarding your organisation’s most valuable assets from cyber threats. By implementing robust controls, monitoring mechanisms, and best practices, you can significantly reduce the risk of security breaches and protect your critical systems from malicious actors.
Essential Insights: 8 Key Questions on Privileged Account Management and Cybersecurity
- What is privileged account management?
- Why is privileged account management important for cybersecurity?
- What are the risks of not implementing privileged account management?
- How can privileged accounts be compromised?
- What are the best practices for managing privileged accounts?
- What role does privileged account management play in regulatory compliance?
- How can organisations detect and respond to suspicious activities involving privileged accounts?
- What tools and technologies are available for effective privileged account management?
What is privileged account management?
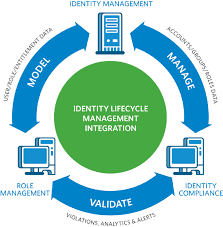
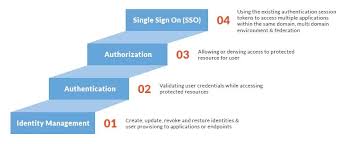
Privileged account management refers to the practice of securely controlling and monitoring user accounts with elevated permissions within an organisation’s IT infrastructure. These accounts, known as privileged accounts, have access to critical systems and sensitive data that could pose significant security risks if mishandled or compromised. Privileged account management involves implementing stringent controls, such as restricting access based on the principle of least privilege, regularly rotating passwords, and monitoring account activity to prevent unauthorised access and potential security breaches. By effectively managing privileged accounts, organisations can enhance their cybersecurity posture, mitigate insider threats, and ensure compliance with industry regulations.
Why is privileged account management important for cybersecurity?
Privileged account management plays a crucial role in cybersecurity due to the elevated access and control that privileged accounts possess within an organisation’s IT infrastructure. These accounts are prime targets for cyber attackers seeking to exploit their high-level permissions to gain unauthorised access to critical systems and sensitive data. By implementing effective privileged account management practices, organisations can minimise security risks, prevent data breaches, ensure compliance with regulations, and mitigate insider threats. Proactive management of privileged accounts is essential for maintaining the security and integrity of an organisation’s IT environment in the face of evolving cyber threats.
What are the risks of not implementing privileged account management?
Failing to implement privileged account management poses significant risks to an organisation’s cybersecurity posture. Without proper controls in place, the unchecked use of privileged accounts can lead to heightened security vulnerabilities, making it easier for malicious actors to gain unauthorised access to critical systems and sensitive data. The lack of oversight and accountability increases the likelihood of insider threats, data breaches, and compliance violations. Moreover, without effective privileged account management, organisations may struggle to detect and respond to security incidents in a timely manner, leaving them exposed to potentially devastating cyber attacks that could result in financial losses and reputational damage. It is crucial for businesses to recognise the risks associated with neglecting privileged account management and take proactive measures to mitigate these threats.
How can privileged accounts be compromised?
Privileged accounts can be compromised through various methods, posing a significant security risk to organisations. One common way is through phishing attacks, where malicious actors trick users into revealing their credentials or installing malware that captures login information. Additionally, weak passwords, improper access controls, and lack of regular monitoring can make privileged accounts vulnerable to exploitation. Insider threats, such as disgruntled employees or negligent insiders, also pose a threat by abusing their elevated permissions for malicious purposes. It is crucial for organisations to implement robust security measures, such as regular password rotations, multi-factor authentication, and continuous monitoring, to mitigate the risk of privileged account compromise and safeguard critical systems and data.
What are the best practices for managing privileged accounts?
When it comes to managing privileged accounts, implementing best practices is crucial for maintaining the security and integrity of an organisation’s IT infrastructure. Some key best practices for managing privileged accounts include implementing the principle of least privilege access to restrict permissions, regularly rotating passwords to mitigate the risk of credential theft, monitoring and auditing account activity to detect any suspicious behaviour, utilising multi-factor authentication for enhanced security, and conducting employee training to raise awareness about secure password practices. By adhering to these best practices, organisations can effectively safeguard their critical systems and data from potential cyber threats.
What role does privileged account management play in regulatory compliance?
Privileged account management plays a crucial role in regulatory compliance by ensuring that organisations adhere to industry standards and regulations regarding data security and access control. Regulatory frameworks such as GDPR, PCI DSS, and HIPAA require businesses to implement robust controls over privileged accounts to protect sensitive information from unauthorised access or misuse. By effectively managing privileged accounts, organisations can demonstrate accountability, transparency, and adherence to regulatory requirements, thereby mitigating the risk of non-compliance penalties and safeguarding the integrity of their data assets.
How can organisations detect and respond to suspicious activities involving privileged accounts?
Organisations can detect and respond to suspicious activities involving privileged accounts by implementing robust monitoring and alerting systems specifically designed for privileged account management. By continuously monitoring the usage patterns and access behaviours of privileged accounts, organisations can establish baseline activity profiles and set up alerts for any deviations from normal behaviour. Additionally, employing advanced analytics and machine learning technologies can help in identifying anomalous activities that may indicate a potential security threat. In the event of detecting suspicious behaviour, organisations should have predefined response procedures in place, such as immediately revoking access privileges, conducting forensic investigations, and implementing corrective actions to mitigate any potential risks posed by the compromised privileged accounts.
What tools and technologies are available for effective privileged account management?
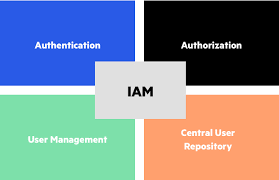
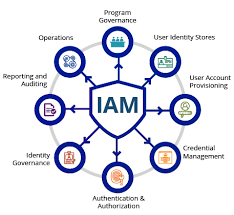
When it comes to effective privileged account management, a variety of tools and technologies are available to help organisations enhance their security posture. Privileged Access Management (PAM) solutions, such as password vaults, session monitoring tools, and privilege elevation controls, are commonly used to secure and manage privileged accounts. Additionally, Identity and Access Management (IAM) platforms offer features for role-based access control, automated provisioning/deprovisioning, and identity governance to streamline privileged account management processes. Security Information and Event Management (SIEM) systems play a crucial role in monitoring and analysing privileged account activities for threat detection and compliance purposes. Overall, leveraging a combination of these tools and technologies can strengthen an organisation’s defence against cyber threats targeting privileged accounts.