The Importance of IAM Systems in Modern Businesses
In today’s digital age, businesses are faced with increasing security threats and regulatory requirements. Identity and Access Management (IAM) systems have become essential tools for organisations to secure their digital assets and ensure compliance with data protection laws.
Enhanced Security
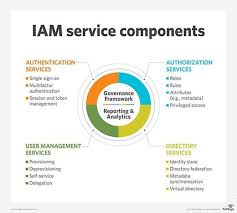
IAM systems provide a centralised platform for managing user identities, access rights, and permissions across an organisation’s IT infrastructure. By implementing IAM solutions, businesses can enforce strong authentication methods, such as multi-factor authentication, to prevent unauthorised access to sensitive data.
Improved Productivity
With IAM systems, employees can securely access the resources they need to perform their roles efficiently. Automated provisioning and deprovisioning processes streamline user account management, reducing the burden on IT teams and minimising the risk of human error.
Compliance Adherence
Regulatory requirements, such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA), mandate strict controls over user access to personal information. IAM systems help businesses demonstrate compliance by maintaining detailed audit logs and enforcing least privilege principles.
Cost Savings
By implementing IAM systems, businesses can reduce the risk of data breaches and insider threats that could result in costly remediation efforts. Additionally, automated identity lifecycle management processes help organisations save time and resources that would otherwise be spent on manual user account administration.
Scalability and Flexibility
IAM systems are designed to scale with the growth of an organisation. Whether expanding operations geographically or introducing new services, businesses can easily adapt their IAM solutions to accommodate changing business requirements without compromising security.
Conclusion
In conclusion, IAM systems play a crucial role in safeguarding sensitive data, enhancing operational efficiency, and ensuring regulatory compliance for modern businesses. By investing in robust IAM solutions, organisations can mitigate security risks, improve productivity, and protect their reputation in an increasingly interconnected digital landscape.
Understanding IAM Systems: Answers to 7 Common Questions
- Is Active Directory an IAM system?
- What is an IAM system?
- What is an example of IAM?
- What is the IAM?
- What is IAM software?
- What does IAM stand for?
- What is IAM short for?
Is Active Directory an IAM system?
The question of whether Active Directory is an IAM system is a common one in the realm of identity and access management. Active Directory, developed by Microsoft, primarily serves as a directory service for managing user accounts, groups, and permissions within a Windows network environment. While Active Directory provides fundamental identity management capabilities, it is not considered a comprehensive IAM system on its own. IAM systems typically offer broader functionalities, including user authentication, access control, identity governance, and compliance management across diverse IT infrastructures. Organisations often integrate Active Directory with dedicated IAM solutions to enhance security and streamline identity lifecycle management processes effectively.
What is an IAM system?
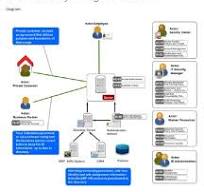
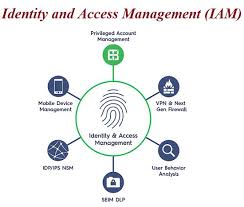
An IAM system, short for Identity and Access Management system, is a comprehensive framework that allows organisations to manage and control user identities and their access to various resources within an IT environment. It serves as a centralised platform for defining user roles, permissions, and authentication methods to ensure secure access to sensitive data and applications. IAM systems play a critical role in enhancing security, streamlining user account management processes, enforcing compliance with regulatory requirements, and supporting the scalability of businesses in today’s digital landscape.
What is an example of IAM?
An example of an Identity and Access Management (IAM) system is Microsoft’s Azure Active Directory (AAD). Azure AD is a cloud-based identity management service that enables organisations to manage user identities and access permissions for various Microsoft and third-party applications. With Azure AD, businesses can enforce security policies, facilitate single sign-on capabilities, and streamline user provisioning processes across their IT infrastructure. This IAM solution offers a comprehensive set of features to help organisations secure their digital assets and ensure efficient identity management practices.
What is the IAM?
Identity and Access Management (IAM) is a comprehensive framework that encompasses policies, technologies, and processes aimed at managing digital identities and controlling access to resources within an organisation’s IT environment. IAM systems enable businesses to authenticate the identities of users, assign appropriate access rights based on their roles, and monitor activities to ensure security and compliance. By centralising identity management functions and implementing robust access controls, IAM empowers organisations to protect sensitive data, streamline user provisioning processes, and mitigate risks associated with unauthorised access or insider threats.
What is IAM software?
IAM software, short for Identity and Access Management software, is a comprehensive solution designed to manage user identities, control access rights, and enforce security policies within an organisation’s IT environment. IAM software plays a crucial role in ensuring that only authorised individuals have access to specific resources and applications, thereby reducing the risk of data breaches and insider threats. By centralising identity management processes and providing automated tools for user provisioning, deprovisioning, and authentication, IAM software enhances security, streamlines administrative tasks, and helps businesses achieve compliance with regulatory requirements.
What does IAM stand for?
IAM stands for Identity and Access Management. It refers to a comprehensive framework of policies, technologies, and processes that organisations use to manage digital identities and control access to their systems and data. IAM systems play a crucial role in ensuring the security of sensitive information by verifying the identities of users, granting appropriate levels of access based on their roles, and monitoring user activities to detect and prevent unauthorised actions. By implementing IAM solutions, businesses can strengthen their cybersecurity posture, streamline user management processes, and demonstrate compliance with regulatory requirements.
What is IAM short for?
IAM stands for Identity and Access Management. It refers to a comprehensive framework of policies, technologies, and processes that organisations use to manage digital identities and control access to their resources. IAM systems play a crucial role in ensuring the security of sensitive data by verifying the identities of users and regulating their permissions within an IT environment. By implementing IAM solutions, businesses can enforce strict access controls, streamline user provisioning processes, and maintain compliance with regulatory requirements.