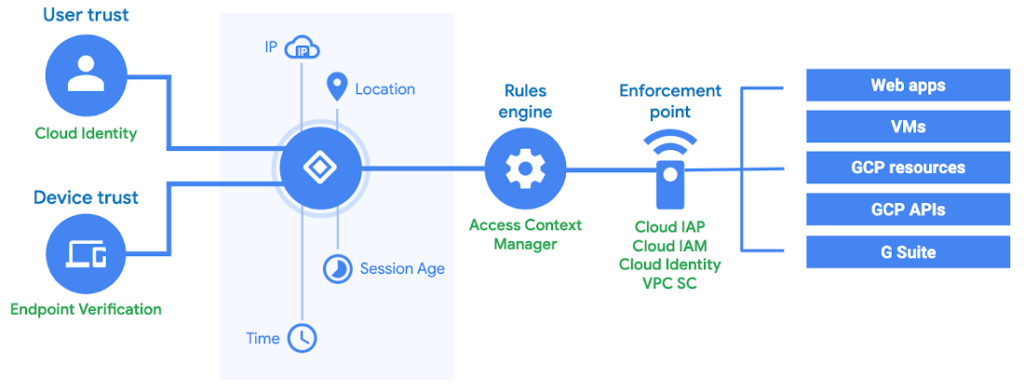
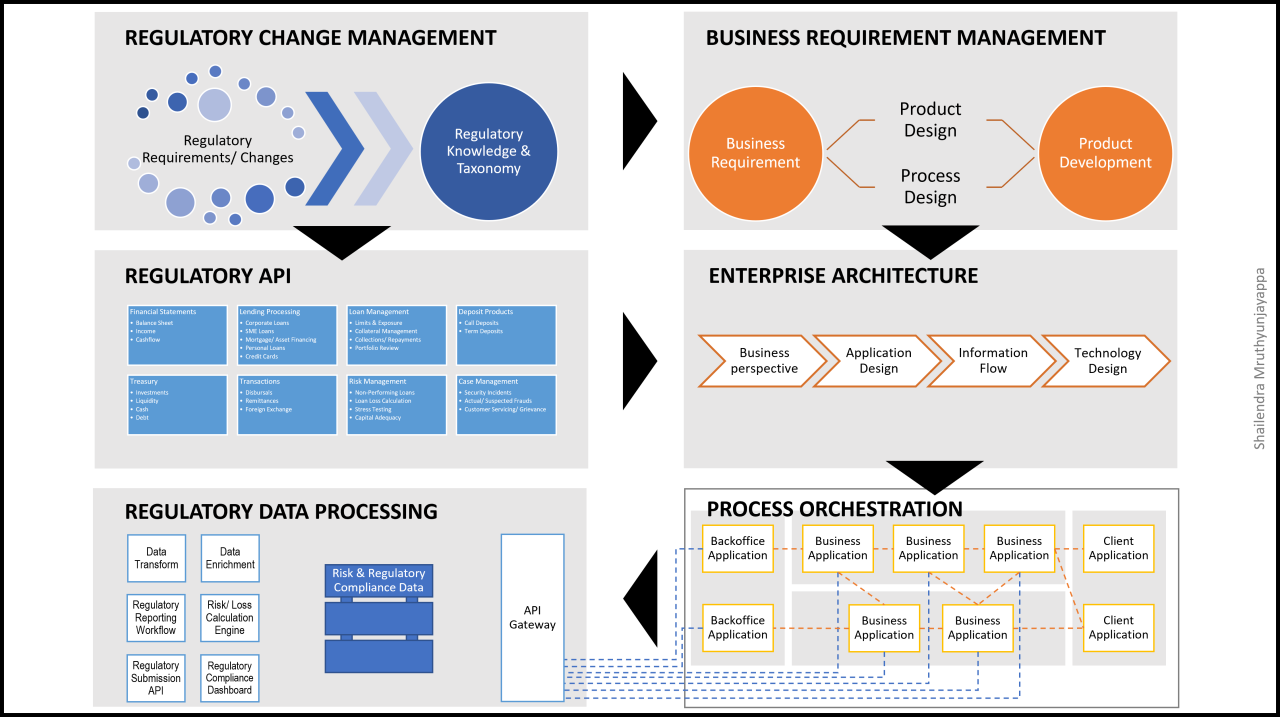
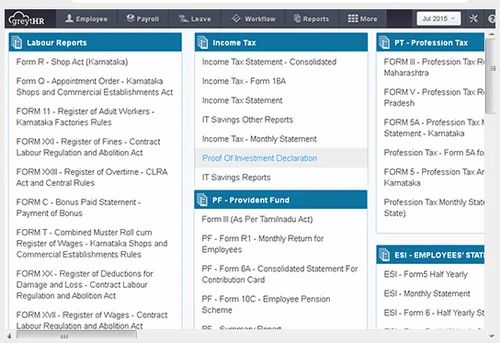
The Top Access Management Software Solutions for Enhanced Security
Access management software plays a crucial role in safeguarding sensitive data and ensuring that only authorised users have the right level of access within an organisation. With the increasing complexity of IT environments and the rise in cyber threats, choosing the right access management solution is paramount to maintaining a secure infrastructure.
Microsoft Azure Active Directory
Microsoft Azure Active Directory is a cloud-based identity and access management solution that offers seamless integration with Microsoft products and services. It provides robust authentication mechanisms, single sign-on capabilities, and multi-factor authentication to enhance security across various applications and devices.
Okta
Okta is a leading identity management platform that offers comprehensive access control features, including user provisioning, single sign-on, and adaptive authentication. With its user-friendly interface and extensive integration options, Okta is favoured by many organisations looking to streamline their access management processes.
OneLogin
OneLogin is a cloud-based identity and access management solution that simplifies user authentication and authorisation processes. It offers features such as role-based access control, password management, and directory integration to help organisations manage their users’ access rights efficiently.
IBM Security Verify
IBM Security Verify is a comprehensive identity-as-a-service platform that combines identity governance, access management, and threat detection capabilities. With its advanced analytics and risk-based authentication features, IBM Security Verify helps organisations detect and respond to security threats effectively.
Ping Identity
Ping Identity is a trusted provider of identity security solutions that offer secure access to applications and APIs. Its intelligent access management features enable organisations to implement fine-grained access controls based on user attributes and contextual information for enhanced security.
When selecting an access management software solution for your organisation, consider factors such as scalability, ease of integration, compliance requirements, and user experience. By choosing one of the top solutions mentioned above or exploring other reputable providers in the market, you can strengthen your security posture and protect your valuable assets from unauthorised access.
Top 6 Benefits of Leading Access Management Software: Security, Compliance, and More
- Enhanced security
- Improved compliance
- Simplified user experience
- Efficient access control
- Scalability
- Cost-effectiveness
Navigating the Drawbacks of Top Access Management Software: Complexity, Cost, and Integration Challenges
Enhanced security
Access management software offers a significant advantage in enhancing security within an organisation by effectively controlling user access to critical data and resources. By implementing robust access management solutions, businesses can ensure that only authorised individuals have the necessary permissions to interact with sensitive information, thereby reducing the risk of data breaches and insider threats. This proactive approach to security not only safeguards valuable assets but also promotes a culture of accountability and compliance, ultimately contributing to a more secure and resilient IT environment.
Improved compliance
Access management software solutions offer a significant advantage in terms of improved compliance for organisations. By enforcing access policies and tracking user activities, these tools play a crucial role in helping businesses meet regulatory requirements effectively. With features such as role-based access control and detailed activity monitoring, access management software ensures that organisations can demonstrate adherence to industry regulations and standards, thereby reducing the risk of non-compliance penalties and enhancing overall data security.
Simplified user experience
Access management software provides a simplified user experience by offering single sign-on capabilities, allowing users to access multiple applications with just one set of credentials. This feature streamlines the login process and eliminates the need for users to remember and enter different login details for each application they use. By centralising authentication through a single sign-on system, access management software enhances user convenience and productivity while maintaining security standards across various platforms and services.
Efficient access control
Organisations benefit from efficient access control when utilising top access management software. These solutions offer intuitive interfaces that enable seamless management of user privileges, roles, and permissions. By providing a user-friendly platform for administrators to oversee and adjust access rights, access management software streamlines the process of ensuring that users have appropriate levels of access to resources. This efficiency not only enhances security by reducing the risk of unauthorised access but also simplifies compliance with regulatory requirements regarding data protection and privacy.
Scalability
Scalability is a key advantage of the best access management software solutions, as they have the flexibility to grow alongside an organisation and accommodate evolving requirements. These scalable solutions can easily adjust to changes in user numbers, access levels, and system complexity without compromising security or performance. By offering scalability, access management software ensures that organisations can effectively manage access controls and permissions as their operations expand, providing a seamless and secure user experience while maintaining compliance with regulatory standards.
Cost-effectiveness
Cost-effectiveness is a key advantage of the best access management software solutions. By automating access control processes and mitigating the risk of unauthorised access, these tools enable organisations to operate more efficiently and securely. This automation not only saves valuable time but also optimises resource allocation, leading to long-term cost savings. Investing in top-tier access management software can result in improved productivity, streamlined operations, and ultimately, a stronger return on investment for businesses of all sizes.
Complexity
Some access management software solutions may present a significant drawback in terms of complexity. Configuring and maintaining these systems can be challenging, often demanding specialised knowledge and training from IT professionals. The intricate setup processes and ongoing maintenance requirements can pose obstacles for organisations looking to implement access management solutions efficiently. This complexity may lead to delays in deployment, increased operational costs, and potential errors if not managed effectively. Therefore, it is essential for businesses to carefully assess the level of expertise and resources needed before investing in access management software to mitigate the impact of this con.
Cost
Implementing top-tier access management software may present a significant con in terms of cost. The upfront investment required for licensing, integration, and ongoing support can be substantial, especially for organisations with budget constraints. While the benefits of enhanced security and streamlined access control are undeniable, the financial implications of acquiring and maintaining such software need to be carefully considered. Balancing the cost factor with the long-term advantages of robust access management solutions is essential for making informed decisions that align with both security needs and budgetary constraints.
Integration Challenges
Integrating access management software with existing IT systems and applications can present a significant challenge due to compatibility issues that may arise. This process often demands additional resources in terms of time, effort, and potentially financial investment to ensure seamless integration. Compatibility concerns between different platforms and the need for custom configurations can lead to delays in implementation and potential disruptions to daily operations. Organisations must carefully assess the integration requirements of access management software to mitigate these challenges effectively and optimise the overall security posture of their IT infrastructure.