The Power of Bomgar Privileged Identity Management
In today’s digital landscape, protecting sensitive information and securing critical systems are top priorities for organisations. With the increasing number of cyber threats and data breaches, managing privileged identities has become essential for maintaining a secure IT environment. This is where Bomgar Privileged Identity Management comes into play.
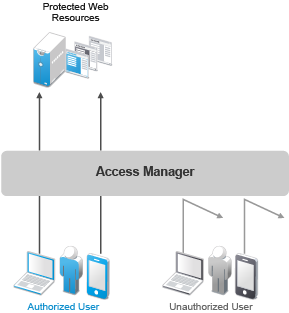
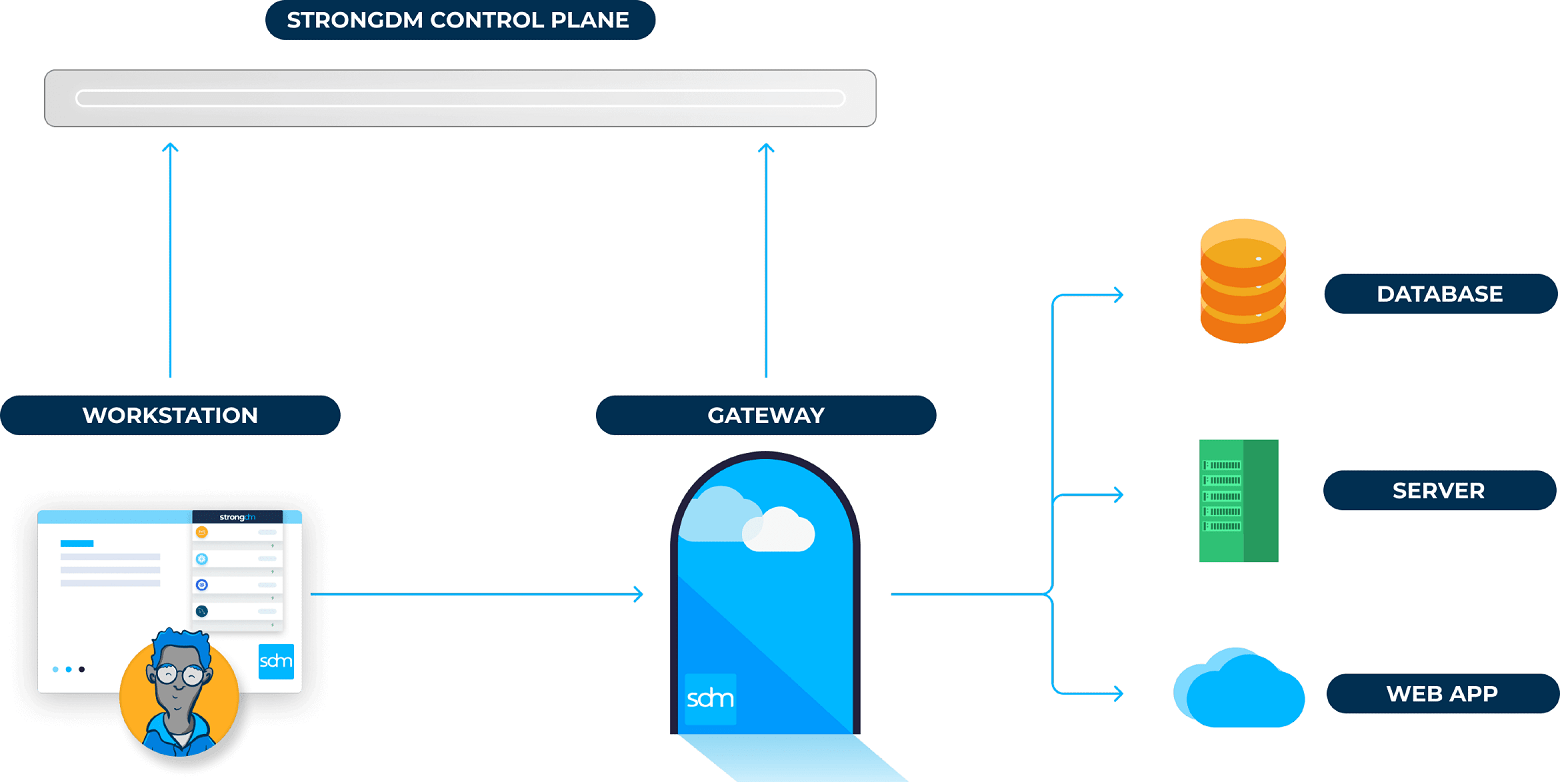
Bomgar Privileged Identity Management offers a comprehensive solution for managing and securing privileged accounts within an organisation. By centralising and controlling access to sensitive systems and data, Bomgar helps prevent unauthorised access and potential security breaches.
Key Features of Bomgar Privileged Identity Management:
- Centralised Access Control: Bomgar provides a centralised platform to manage and monitor all privileged accounts, reducing the risk of credential misuse.
- Session Monitoring: With session monitoring capabilities, Bomgar allows administrators to track and record privileged sessions in real-time for auditing purposes.
- Automated Password Rotation: Bomgar automates the process of regularly rotating passwords for privileged accounts, enhancing security by reducing the risk of password-based attacks.
- Multi-Factor Authentication: By supporting multi-factor authentication, Bomgar adds an extra layer of security to verify the identity of users accessing privileged accounts.
By implementing Bomgar Privileged Identity Management, organisations can strengthen their security posture, improve compliance with regulatory requirements, and mitigate the risk of insider threats. With its robust features and user-friendly interface, Bomgar empowers IT teams to proactively manage privileged identities and safeguard critical assets from potential security risks.
As cyber threats continue to evolve, investing in solutions like Bomgar Privileged Identity Management is crucial for maintaining a secure and resilient IT infrastructure. By leveraging the power of Bomgar, organisations can effectively protect their most valuable assets and ensure business continuity in an increasingly interconnected world.
Understanding Bomgar Privileged Identity: Answers to 7 Key Questions
- What is the difference between BeyondTrust privileged identity and Password Safe?
- What are the privileged identities?
- What is the difference between IAM and privileged identity management?
- How to enable privileged identity management?
- What feature of privileged identity management allows you?
- What is a privileged identity?
- What is privileged IDS?
What is the difference between BeyondTrust privileged identity and Password Safe?
When comparing BeyondTrust Privileged Identity and Password Safe, it’s essential to understand the distinct functionalities each solution offers. BeyondTrust Privileged Identity focuses on managing and securing privileged accounts within an organisation, providing centralised access control, session monitoring, automated password rotation, and multi-factor authentication capabilities. On the other hand, Password Safe specifically addresses the secure storage and management of passwords across various systems and applications. While both solutions contribute to enhancing security and compliance measures, BeyondTrust Privileged Identity offers a broader range of features tailored towards managing privileged identities, while Password Safe excels in securely storing and retrieving passwords for improved access management. Organizations can choose the solution that best aligns with their specific security needs and operational requirements to bolster their overall cybersecurity posture effectively.
What are the privileged identities?
Privileged identities refer to user accounts or credentials that have elevated permissions within an organisation’s IT infrastructure. These privileged accounts typically have access to sensitive systems, data, and resources that are critical for the operation of the business. Examples of privileged identities include system administrators, IT managers, and other personnel with high-level access rights. Managing and securing privileged identities is essential for preventing unauthorised access, reducing the risk of insider threats, and maintaining compliance with security regulations. Bomgar Privileged Identity Management offers a robust solution to centralise control over these critical accounts, monitor their activities, and strengthen overall security posture within an organisation.
What is the difference between IAM and privileged identity management?
When considering the difference between Identity and Access Management (IAM) and Privileged Identity Management (PIM), it’s essential to understand their distinct roles in securing an organisation’s digital assets. IAM focuses on managing user identities, controlling access to resources based on individual roles and permissions, and ensuring authentication and authorisation processes are in place. On the other hand, PIM specifically targets privileged accounts with elevated access rights, such as system administrators or IT personnel. PIM solutions like Bomgar Privileged Identity Management provide additional layers of security for these high-risk accounts, including session monitoring, automated password rotation, and enhanced access controls to mitigate the risk of insider threats and data breaches. By integrating both IAM and PIM strategies, organisations can establish a comprehensive security framework that safeguards all levels of access within their IT infrastructure effectively.
How to enable privileged identity management?
To enable privileged identity management using Bomgar, organisations can follow a straightforward process to enhance security and control over privileged accounts. Firstly, administrators need to access the Bomgar Privileged Identity Management platform and configure the settings according to their specific requirements. This includes defining access levels, setting up session monitoring parameters, and implementing automated password rotation policies. Once the configuration is complete, administrators can start assigning privileged access rights to users based on their roles and responsibilities within the organisation. By enabling multi-factor authentication and regularly monitoring privileged sessions, organisations can effectively strengthen their security posture and mitigate potential risks associated with privileged identities.
What feature of privileged identity management allows you?
One of the key features of Bomgar Privileged Identity Management that frequently garners attention is its centralised access control capability. This feature empowers organisations to efficiently manage and monitor all privileged accounts from a single, consolidated platform. By providing a unified view of access rights and permissions, Bomgar enables administrators to exercise granular control over who can access sensitive systems and data, reducing the risk of unauthorised access and potential security breaches. The centralised access control feature not only enhances security but also streamlines the management of privileged identities, ensuring compliance with regulatory requirements and bolstering overall cybersecurity posture.
What is a privileged identity?
A privileged identity refers to an account with elevated access rights within an organisation’s IT infrastructure, granting users the authority to perform critical tasks and access sensitive information. These accounts typically have higher levels of permissions compared to standard user accounts, allowing individuals to configure systems, install software, modify settings, and access confidential data. Managing privileged identities is crucial for maintaining security and preventing unauthorised access to critical systems. Solutions like Bomgar Privileged Identity Management help organisations centralise control over these accounts, monitor their usage, and enforce security measures to protect against potential breaches and insider threats.
What is privileged IDS?
Privileged Identity Management (PIM) is a crucial component of cybersecurity that focuses on managing and securing privileged accounts within an organisation. Privileged IDs refer to accounts with elevated access rights that allow users to perform critical functions and access sensitive data. PIM solutions, such as Bomgar Privileged Identity Management, help organisations centralise control over these privileged accounts, monitor and record user sessions, automate password rotation, and implement multi-factor authentication to enhance security and reduce the risk of unauthorised access or misuse of privileged credentials. By effectively managing privileged identities, organisations can strengthen their security posture and ensure the integrity of their IT infrastructure against potential threats.