The Importance of Access Management Services in Ensuring Data Security
In today’s digital age, where data breaches and cyber threats are becoming increasingly common, the need for robust access management services has never been more critical. Access management is the process of controlling who can access what information within an organisation’s IT infrastructure. It involves managing user identities, enforcing security policies, and monitoring user activities to protect sensitive data from unauthorised access.
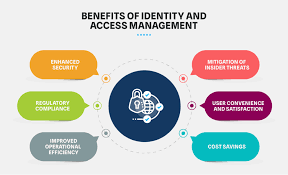
One of the key benefits of access management services is enhanced data security. By implementing strong authentication methods such as multi-factor authentication and role-based access control, organisations can ensure that only authorised users have access to specific resources. This helps prevent insider threats, external attacks, and accidental data leaks that could compromise the confidentiality and integrity of sensitive information.
Access management services also play a crucial role in regulatory compliance. Many industries are subject to strict data protection regulations that require organisations to implement adequate measures to safeguard sensitive data. By using access management solutions to enforce access policies, track user activities, and generate audit reports, businesses can demonstrate compliance with regulations such as GDPR, HIPAA, and PCI DSS.
Moreover, effective access management services improve operational efficiency within an organisation. By automating user provisioning and deprovisioning processes, IT departments can streamline user account management tasks and reduce the risk of human errors. This not only saves time and resources but also ensures that former employees or contractors no longer have access to company systems after they leave.
Another advantage of access management services is improved user experience. By implementing single sign-on solutions and self-service password reset capabilities, organisations can provide users with seamless access to multiple applications without compromising security. This not only enhances productivity but also reduces the burden on IT support teams by empowering users to manage their own accounts.
In conclusion, access management services are essential for protecting sensitive data, ensuring regulatory compliance, enhancing operational efficiency, and improving user experience within an organisation. By investing in robust access management solutions, businesses can mitigate security risks, prevent data breaches, and build a strong foundation for a secure digital environment.
Top 9 Benefits of Access Management Services: Strengthening Security and Efficiency
- Enhances data security by controlling access to sensitive information.
- Mitigates the risk of insider threats and external cyber attacks.
- Facilitates regulatory compliance by enforcing access policies.
- Improves operational efficiency through automated user provisioning processes.
- Reduces the likelihood of human errors in user account management.
- Enhances user experience with single sign-on and self-service capabilities.
- Increases productivity by providing seamless access to multiple applications.
- Empowers users to manage their own accounts, reducing IT support workload.
- Builds a secure foundation for a digital environment in today’s cyber landscape.
Challenges and Concerns in Implementing Access Management Services
- Complex implementation process that may require significant time and resources.
- Potential for user resistance to new access control measures, impacting adoption rates.
- Risk of system downtime or disruptions during the deployment of access management solutions.
- Difficulty in managing access privileges for a large number of users across multiple systems and applications.
- Challenges in integrating access management services with existing IT infrastructure and legacy systems.
- Concerns about data privacy and security breaches if access management tools are not properly configured or maintained.
Access management services play a crucial role in enhancing data security by controlling access to sensitive information. By implementing strict access controls and authentication mechanisms, organisations can ensure that only authorised users have the necessary permissions to view or modify sensitive data. This proactive approach helps prevent unauthorised access, insider threats, and data breaches, safeguarding confidential information from falling into the wrong hands. Effective access management not only strengthens the overall security posture of an organisation but also instils trust among stakeholders that their data is being protected with the highest level of diligence and care.
Mitigates the risk of insider threats and external cyber attacks.
Access management services play a crucial role in mitigating the risk of insider threats and external cyber attacks by implementing robust authentication mechanisms and access controls. By enforcing strict user authentication processes, such as multi-factor authentication and role-based access control, organisations can ensure that only authorised individuals have access to sensitive data and resources. This helps prevent malicious insiders from abusing their privileges and external attackers from infiltrating the network through compromised accounts. Additionally, continuous monitoring of user activities and prompt detection of suspicious behaviour enable proactive responses to potential security breaches, safeguarding the organisation’s digital assets from internal and external threats.
Facilitates regulatory compliance by enforcing access policies.
Access management services play a crucial role in facilitating regulatory compliance by enforcing access policies. By implementing strict access controls and permissions based on roles and responsibilities, organisations can ensure that only authorised individuals have access to sensitive data and systems. This proactive approach not only helps in preventing data breaches and insider threats but also assists in demonstrating compliance with industry regulations such as GDPR, HIPAA, and PCI DSS. By enforcing access policies through access management services, businesses can effectively manage user permissions, track user activities, and generate audit reports to meet regulatory requirements and protect sensitive information from unauthorised access.
Improves operational efficiency through automated user provisioning processes.
Automated user provisioning processes provided by access management services significantly enhance operational efficiency within organisations. By automating the creation, modification, and deletion of user accounts based on predefined rules and policies, IT departments can streamline the onboarding and offboarding processes for employees, contractors, and partners. This automation not only reduces the manual workload on IT staff but also minimises the risk of errors and delays in granting or revoking access to critical systems and resources. As a result, organisations can efficiently manage user access permissions, ensure compliance with security policies, and maintain a secure and agile IT environment that aligns with business needs.
Reduces the likelihood of human errors in user account management.
One significant advantage of access management services is their ability to reduce the likelihood of human errors in user account management. By automating processes such as user provisioning and deprovisioning, organisations can minimise the risk of mistakes that could lead to security vulnerabilities or compliance issues. Automated workflows ensure that user accounts are created, modified, or removed accurately and in a timely manner, eliminating the need for manual intervention and reducing the potential for errors. This not only enhances data security but also improves operational efficiency by streamlining account management tasks and maintaining an accurate record of user access rights.
Enhances user experience with single sign-on and self-service capabilities.
By implementing access management services that offer features such as single sign-on and self-service capabilities, organisations can greatly enhance the user experience. With single sign-on, users can conveniently access multiple applications with just one set of credentials, eliminating the need to remember and enter different passwords for each system. Additionally, self-service capabilities empower users to reset their passwords or manage account settings independently, reducing reliance on IT support and providing a seamless and efficient user experience. These features not only improve productivity but also contribute to a more positive interaction between users and IT systems within the organisation.
Increases productivity by providing seamless access to multiple applications.
One significant advantage of access management services is their ability to boost productivity by offering seamless access to multiple applications. By implementing single sign-on solutions and centralised user authentication mechanisms, organisations can streamline the login process for employees, eliminating the need to remember and enter multiple sets of credentials. This not only saves time but also enhances user experience, allowing individuals to access the necessary tools and resources swiftly and efficiently. As a result, employees can focus on their tasks without being hindered by cumbersome login procedures, ultimately increasing overall productivity within the workplace.
Empowers users to manage their own accounts, reducing IT support workload.
Empowering users to manage their own accounts through access management services is a significant benefit that can greatly reduce the workload on IT support teams. By providing self-service capabilities such as password resets and account updates, organisations enable users to address common account-related issues independently, without the need for IT intervention. This not only enhances user satisfaction by offering a more seamless experience but also frees up IT resources to focus on more strategic initiatives and critical security tasks, ultimately improving operational efficiency across the board.
Builds a secure foundation for a digital environment in today’s cyber landscape.
In today’s ever-evolving cyber landscape, access management services play a crucial role in building a secure foundation for digital environments. By implementing strong authentication methods, enforcing access policies, and monitoring user activities, organisations can establish a robust security framework that protects sensitive data from cyber threats. This proactive approach not only helps prevent unauthorised access and data breaches but also instils trust among stakeholders that their information is safeguarded within the digital ecosystem. In essence, access management services serve as the cornerstone of cybersecurity efforts in an increasingly interconnected world, ensuring that businesses can operate safely and securely in the face of evolving cyber risks.
Complex implementation process that may require significant time and resources.
One significant drawback of access management services is the complex implementation process that often demands a substantial investment of time and resources. Setting up access management solutions involves configuring user roles, permissions, authentication methods, and integration with existing IT systems, which can be a challenging and time-consuming task. Organisations may need to allocate dedicated personnel, undergo extensive training, and potentially enlist external expertise to ensure the successful deployment of access management services. This complexity in implementation can lead to delays in achieving desired security measures and may pose a barrier for organisations with limited IT capabilities or budget constraints.
Potential for user resistance to new access control measures, impacting adoption rates.
One significant con of access management services is the potential for user resistance to new access control measures, which can impact adoption rates within an organisation. Introducing stringent authentication requirements or restricting access to certain resources may be met with pushback from employees who are accustomed to more lenient access privileges. User resistance can lead to frustration, decreased productivity, and even circumvention of security measures, ultimately undermining the effectiveness of the access management system. Overcoming user resistance requires effective communication, training, and a balance between security needs and user convenience to ensure successful implementation and acceptance of new access control measures.
Risk of system downtime or disruptions during the deployment of access management solutions.
During the deployment of access management solutions, one significant con that organisations may face is the risk of system downtime or disruptions. Implementing new access management tools or making changes to existing systems can sometimes lead to unexpected technical issues that may temporarily impact system availability. This downtime can disrupt normal business operations, causing inconvenience to users and potentially affecting productivity. It is crucial for organisations to carefully plan and test access management deployments to minimise the risk of system disruptions and ensure a smooth transition without compromising the integrity of critical IT services.
Difficulty in managing access privileges for a large number of users across multiple systems and applications.
One significant challenge posed by access management services is the complexity of managing access privileges for a large number of users across multiple systems and applications. As organisations grow and adopt various technologies, the task of ensuring that the right users have appropriate access levels becomes increasingly intricate. With disparate systems and applications requiring different sets of permissions, maintaining consistency and accuracy in user access control can be a daunting task. This complexity not only increases the risk of errors and oversights but also adds to the administrative burden on IT teams, making it challenging to efficiently manage and monitor user access across the entire IT landscape.
Challenges in integrating access management services with existing IT infrastructure and legacy systems.
One significant challenge of access management services is the complexity involved in integrating them with existing IT infrastructure and legacy systems. Many organisations rely on a mix of modern and outdated technologies, making it difficult to implement a seamless access management solution across all platforms. Legacy systems may lack compatibility with newer authentication methods or may not support the level of security required by modern access management services. This integration challenge can lead to increased implementation costs, longer deployment times, and potential disruptions to existing workflows, highlighting the need for careful planning and expertise in navigating the complexities of integrating access management services with diverse IT environments.
Concerns about data privacy and security breaches if access management tools are not properly configured or maintained.
One significant con of access management services is the potential risk of data privacy breaches and security incidents if the access management tools are not correctly configured or adequately maintained. Inadequate configuration could lead to vulnerabilities that malicious actors could exploit to gain unauthorised access to sensitive information. Without proper maintenance, outdated access controls or misconfigurations may go unnoticed, leaving critical data exposed to potential breaches. Organisations must prioritise regular monitoring, updates, and audits of their access management systems to mitigate these risks and uphold data privacy and security standards effectively.