The Importance of User Lifecycle Management in IAM
Identity and Access Management (IAM) plays a crucial role in ensuring the security and efficiency of an organisation’s IT infrastructure. One key aspect of IAM that is often overlooked but is essential for maintaining a secure environment is user lifecycle management.
What is User Lifecycle Management?
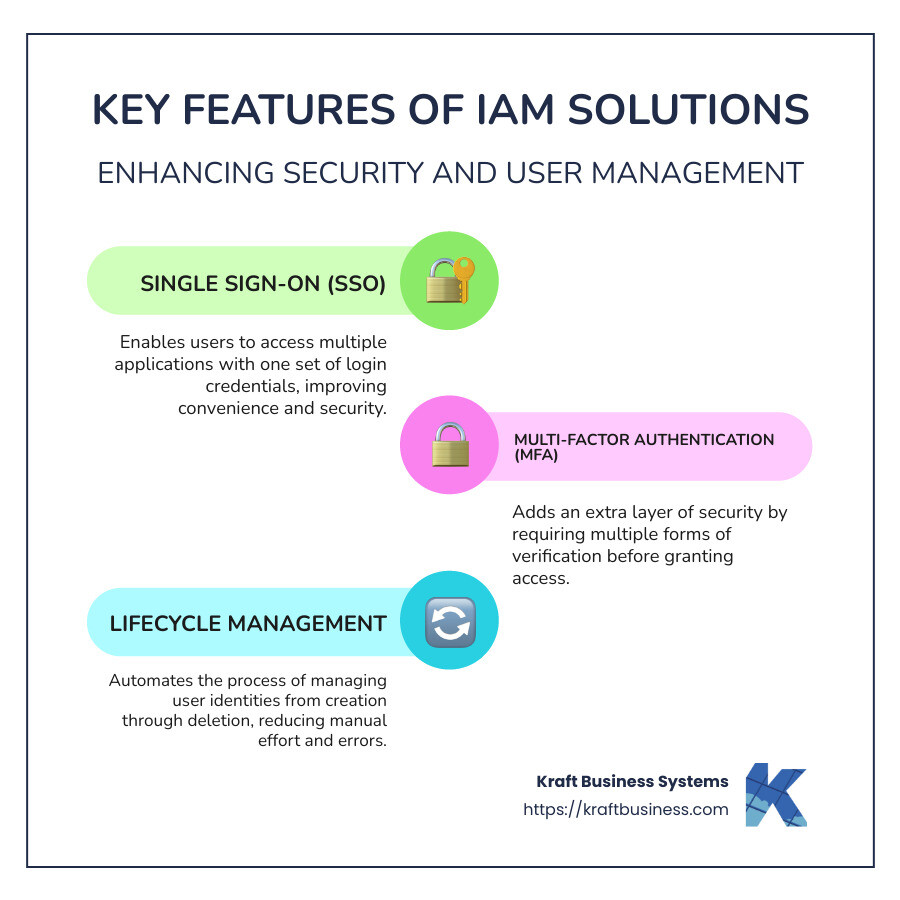
User lifecycle management refers to the process of managing a user’s identity and access rights throughout their entire relationship with an organisation. This includes activities such as onboarding, role changes, access requests, and offboarding. By effectively managing the user lifecycle, organisations can ensure that users have the appropriate level of access to resources at all times, reducing the risk of unauthorised access or data breaches.
The Stages of User Lifecycle Management
Onboarding: The onboarding process involves creating new user accounts, assigning appropriate roles and permissions, and providing necessary training and resources for new users to start their work efficiently.
Role Changes: As users’ responsibilities within an organisation change, their access rights may need to be adjusted accordingly. User lifecycle management ensures that users have the right level of access based on their current roles and responsibilities.
Access Requests: Users may need additional access permissions to perform their tasks effectively. User lifecycle management processes should include mechanisms for users to request access rights in a controlled and auditable manner.
Offboarding: When a user leaves an organisation, it is crucial to revoke their access rights promptly to prevent any potential security risks. Offboarding processes should include deactivating accounts, removing user privileges, and transferring any necessary data or responsibilities to other users.
The Benefits of Effective User Lifecycle Management
– Improved Security: By ensuring that users have only the necessary level of access rights at any given time, organisations can reduce the risk of unauthorised access or insider threats.
– Enhanced Compliance: User lifecycle management helps organisations meet regulatory requirements by maintaining accurate records of user activities and access permissions.
– Increased Efficiency: By automating user lifecycle management processes, organisations can streamline operations and reduce manual errors associated with managing user identities.
– Cost Savings: Effective user lifecycle management can help reduce IT support costs by minimising the time spent on managing user accounts and permissions manually.
In Conclusion
User lifecycle management is a critical component of IAM that should not be overlooked. By implementing effective processes for managing the entire lifecycle of a user’s identity within an organisation, businesses can enhance security, improve compliance, increase efficiency, and reduce costs associated with managing user identities. Investing in robust user lifecycle management practices is essential for maintaining a secure and well-managed IT environment.
6 Essential Tips for Effective User Lifecycle Management in IAM
- Clearly define user roles and permissions based on job responsibilities.
- Regularly review and update user access rights to ensure least privilege principle.
- Implement multi-factor authentication for enhanced security.
- Provide adequate training to users on security best practices and IAM policies.
- Monitor user activity and set up alerts for suspicious behaviour.
- Have a streamlined process for onboarding and offboarding users efficiently.
Clearly define user roles and permissions based on job responsibilities.
In Identity and Access Management (IAM), a crucial tip for effective user lifecycle management is to clearly define user roles and permissions based on job responsibilities. By aligning access rights with specific job functions, organisations can ensure that users have the appropriate level of access to resources needed to perform their tasks efficiently. This practice not only enhances security by reducing the risk of unauthorised access but also streamlines user management processes, improves compliance with regulatory requirements, and enhances overall operational efficiency within an organisation.
Regularly review and update user access rights to ensure least privilege principle.
To maintain a secure and efficient IT environment, it is essential to adhere to the principle of least privilege when managing user access rights in IAM. Regularly reviewing and updating user access permissions is crucial to ensure that users have only the minimum level of access necessary to perform their job functions. By following this practice, organisations can reduce the risk of unauthorised access and potential security breaches, as well as enhance overall data protection and compliance with regulatory requirements. Regularly evaluating and adjusting user access rights based on business needs and roles helps uphold the principle of least privilege, promoting a more secure and controlled environment for user interactions within the IT infrastructure.
Implement multi-factor authentication for enhanced security.
Implementing multi-factor authentication is a crucial tip for enhancing security in user lifecycle management within IAM. By requiring users to provide multiple forms of verification before accessing sensitive data or resources, organisations can significantly reduce the risk of unauthorised access, even if a user’s credentials are compromised. Multi-factor authentication adds an extra layer of security to the authentication process, making it more challenging for malicious actors to gain access to critical systems. This proactive measure not only strengthens overall security but also aligns with best practices in safeguarding user identities and maintaining a secure IT environment.
Provide adequate training to users on security best practices and IAM policies.
To ensure effective user lifecycle management in IAM, it is essential to provide adequate training to users on security best practices and IAM policies. By educating users on how to securely manage their access rights, follow authentication protocols, and adhere to IAM policies, organisations can empower their employees to play an active role in maintaining a secure IT environment. Training sessions can help users understand the importance of cybersecurity, recognise potential threats, and take proactive measures to safeguard sensitive data. Ultimately, well-informed users contribute significantly to the overall security posture of an organisation and help mitigate risks associated with user identities within the IAM framework.
Monitor user activity and set up alerts for suspicious behaviour.
To enhance security and proactively mitigate risks in Identity and Access Management (IAM), it is crucial to monitor user activity closely and establish alerts for any suspicious behaviour. By monitoring user actions within the system, organisations can swiftly detect unusual patterns or unauthorised access attempts. Setting up alerts for suspicious activities enables prompt responses to potential security threats, helping to safeguard sensitive data and prevent security breaches. Continuous monitoring and alerting mechanisms play a vital role in maintaining a secure IAM environment and ensuring the integrity of user lifecycle management processes.
Have a streamlined process for onboarding and offboarding users efficiently.
Having a streamlined process for onboarding and offboarding users efficiently is essential for effective user lifecycle management in IAM. By establishing clear and well-defined procedures for bringing new users on board and removing departing users, organisations can ensure that access rights are granted and revoked promptly and accurately. A streamlined process not only enhances security by reducing the risk of unauthorised access but also improves operational efficiency by minimising delays in granting necessary permissions to new users and promptly revoking access from departing employees. By prioritising the efficiency of onboarding and offboarding processes, organisations can maintain a secure and well-managed IAM environment.