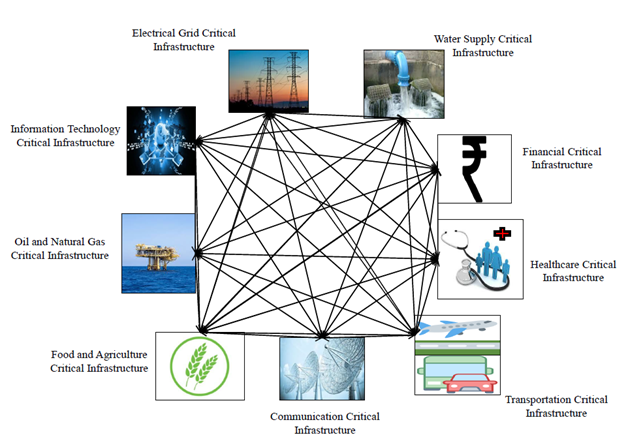
The Importance of Infrastructure Protection in Today’s Digital Landscape
In today’s interconnected world, where businesses rely heavily on digital infrastructure to operate efficiently, the need for robust infrastructure protection has never been greater. Infrastructure protection encompasses a range of measures and practices designed to safeguard critical systems, networks, and data from cyber threats and other risks. Let’s delve into why prioritising infrastructure protection is essential for organisations of all sizes.
Mitigating Cyber Threats
Cyber threats such as malware, ransomware, phishing attacks, and DDoS attacks pose a significant risk to organisations’ infrastructure. By implementing strong security measures, including firewalls, intrusion detection systems, and encryption protocols, businesses can mitigate the risk of falling victim to these malicious activities. Regular security assessments and audits are also crucial for identifying vulnerabilities and addressing them proactively.
Ensuring Business Continuity
An attack on critical infrastructure can disrupt operations, leading to downtime, financial losses, and reputational damage. By investing in infrastructure protection measures such as data backups, disaster recovery plans, and redundant systems, businesses can ensure continuity in the face of unexpected events. This resilience is vital for maintaining productivity and customer trust even in challenging circumstances.
Safeguarding Sensitive Data
Organisations store vast amounts of sensitive data, including customer information, intellectual property, and financial records. Protecting this data from unauthorised access or theft is paramount to maintaining regulatory compliance and preserving trust with stakeholders. Encryption, access controls, data masking techniques, and regular security training for employees are essential components of a comprehensive data protection strategy.
Compliance with Regulations
Many industries are subject to stringent regulations regarding data privacy and security. Failing to comply with these regulations can result in hefty fines, legal consequences, and damage to an organisation’s reputation. Implementing infrastructure protection measures that align with industry standards and regulatory requirements not only helps avoid penalties but also demonstrates a commitment to responsible data management practices.
Proactive Risk Management
Effective infrastructure protection involves proactive risk management strategies that anticipate potential threats before they materialise. This includes conducting regular risk assessments, monitoring system activity for anomalies or suspicious behaviour, and staying informed about emerging cybersecurity trends. By staying ahead of evolving threats through continuous monitoring and adjustment of security protocols, organisations can reduce their exposure to risks significantly.
In Conclusion
Infrastructure protection is a fundamental aspect of modern business operations that cannot be overlooked. By investing in robust security measures, businesses can safeguard their critical assets against cyber threats while ensuring operational continuity and regulatory compliance. Prioritising infrastructure protection is not just a matter of mitigating risks; it is an essential strategic imperative for any organisation seeking long-term success in today’s digital landscape.
Eight Essential Tips for Safeguarding Infrastructure Security
- Regularly assess vulnerabilities in infrastructure
- Implement strong access control measures
- Utilise encryption for sensitive data transmission
- Backup critical data regularly and store securely
- Train employees on cybersecurity best practices
- Monitor network traffic for unusual activity
- Update software and systems to patch security flaws
- Establish a response plan for security incidents
Regularly assess vulnerabilities in infrastructure
Regularly assessing vulnerabilities in infrastructure is a crucial aspect of effective infrastructure protection. By conducting routine vulnerability assessments, organisations can identify potential weaknesses in their systems and networks before they are exploited by malicious actors. This proactive approach allows businesses to address security gaps promptly, implement necessary patches or updates, and strengthen their overall cybersecurity posture. Regular assessments not only help mitigate the risk of cyber threats but also demonstrate a commitment to maintaining a secure and resilient infrastructure that can adapt to evolving security challenges.
Implement strong access control measures
To enhance infrastructure protection, it is crucial to implement robust access control measures. By defining and enforcing strict access policies, organisations can limit the exposure of sensitive data and critical systems to unauthorised users. Strong access controls involve authentication mechanisms such as multi-factor authentication, role-based permissions, and regular access reviews to ensure that only authorised individuals have appropriate levels of access. By restricting access to only those who need it for their roles, organisations can minimise the risk of insider threats and external breaches, thereby strengthening overall security posture.
Utilise encryption for sensitive data transmission
To enhance infrastructure protection, it is crucial to utilise encryption when transmitting sensitive data. Encryption provides a secure method of encoding information, making it unreadable to unauthorised parties during transmission. By implementing encryption protocols, organisations can safeguard sensitive data from interception and ensure that only intended recipients can access and decipher the information. This proactive measure strengthens data security and minimises the risk of potential breaches or data leaks, reinforcing the overall integrity of the infrastructure.
Backup critical data regularly and store securely
One crucial tip for effective infrastructure protection is to regularly back up critical data and store it securely. By implementing a routine backup schedule, organisations can ensure that in the event of data loss due to cyber attacks, hardware failures, or human error, they have a recent copy of their essential information readily available for recovery. Storing backups securely, whether offline or encrypted in the cloud, adds an extra layer of protection against potential threats and ensures that vital data remains safe and accessible when needed most.
Train employees on cybersecurity best practices
Training employees on cybersecurity best practices is a crucial step in enhancing infrastructure protection within an organisation. By educating staff members on how to identify phishing attempts, create strong passwords, and recognise potential security risks, businesses can empower their workforce to become the first line of defence against cyber threats. Regular training sessions not only raise awareness about the importance of cybersecurity but also instil a culture of vigilance and accountability across all levels of the organisation. Ultimately, well-informed employees play a vital role in strengthening the overall security posture of the company and mitigating potential risks effectively.
Monitor network traffic for unusual activity
Monitoring network traffic for unusual activity is a crucial tip in ensuring effective infrastructure protection. By actively monitoring the flow of data within a network, organisations can detect potential security breaches, unauthorised access attempts, or abnormal patterns that may indicate a cyber threat. Identifying and responding to unusual activity promptly can help mitigate risks and prevent potential data breaches or system compromises. Continuous monitoring of network traffic not only enhances security posture but also enables proactive risk management, ultimately strengthening the overall resilience of an organisation’s infrastructure against evolving cyber threats.
Update software and systems to patch security flaws
To enhance infrastructure protection, it is crucial to regularly update software and systems to patch security flaws. Software updates often include patches that address known vulnerabilities, strengthening the overall security posture of the infrastructure. By staying current with updates, organisations can mitigate the risk of exploitation by cyber threats and maintain a more resilient defence against potential attacks. Prioritising timely updates is a proactive measure that reinforces the security foundation of an organisation’s digital infrastructure.
Establish a response plan for security incidents
Establishing a response plan for security incidents is a critical component of infrastructure protection. By having a well-defined and rehearsed plan in place, organisations can respond swiftly and effectively to security breaches, minimising the impact on operations and data integrity. A response plan should outline clear roles and responsibilities, escalation procedures, communication protocols, and steps for containment, investigation, and recovery. Being prepared to handle security incidents proactively not only enhances an organisation’s resilience but also demonstrates a commitment to protecting sensitive information and maintaining trust with stakeholders.