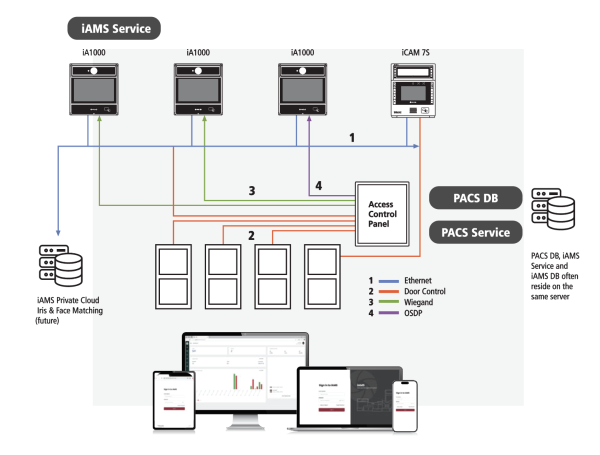
The Importance of Identity and Access Management (I&A) Systems
Identity and Access Management (I&A) systems play a crucial role in today’s digital landscape, where data security and privacy are paramount concerns for organisations of all sizes. These systems are designed to manage user identities, control access to sensitive information, and ensure compliance with regulatory requirements.
Enhanced Security
One of the primary benefits of an I&A management system is enhanced security. By implementing robust authentication mechanisms, such as multi-factor authentication and biometric verification, organisations can significantly reduce the risk of unauthorised access to critical systems and data. These systems also enable administrators to set granular access controls based on roles and responsibilities, further strengthening the overall security posture.
Improved Productivity
Effective I&A management systems streamline user provisioning and deprovisioning processes, ensuring that employees have the right level of access to perform their job functions efficiently. By automating these tasks, organisations can reduce administrative overheads and minimise the risk of human errors that could lead to security breaches or compliance violations.
Regulatory Compliance
In today’s regulatory environment, compliance with data protection laws such as GDPR, HIPAA, and PCI DSS is non-negotiable. I&A management systems help organisations meet these requirements by maintaining audit trails of user activities, enforcing segregation of duties, and facilitating regular access reviews. This not only helps avoid costly fines but also builds trust with customers who expect their data to be handled securely.
Scalability and Flexibility
As organisations grow and evolve, their IT environments become more complex. I&A management systems offer scalability and flexibility to adapt to changing business needs without compromising security. Whether it’s integrating new applications or onboarding a large number of users quickly, these systems provide the agility required to support organisational growth while maintaining control over access rights.
Conclusion
In conclusion, Identity and Access Management (I&A) systems are indispensable tools for modern businesses looking to safeguard their digital assets, enhance operational efficiency, and comply with regulatory mandates. By investing in a robust I&A management system, organisations can establish a strong foundation for secure identity governance that aligns with their strategic objectives.
Optimising Your I&A Management System: 8 Essential Tips for Enhanced Efficiency and Security
- Ensure data accuracy by regularly updating and validating information.
- Implement strict access controls to protect sensitive information.
- Train employees on how to use the system effectively to maximise its benefits.
- Regularly audit the system to identify any issues or areas for improvement.
- Integrate the system with other relevant tools and software for seamless operations.
- Establish clear guidelines and procedures for data input and retrieval within the system.
- Backup data regularly to prevent loss in case of system failures or errors.
- Seek feedback from users to continuously improve the system’s functionality and user experience.
Ensure data accuracy by regularly updating and validating information.
To maintain the integrity and effectiveness of an Identity and Access Management (I&A) system, it is crucial to ensure data accuracy by regularly updating and validating information. By keeping user profiles, access permissions, and other identity-related data up to date, organisations can minimise the risk of security gaps or compliance issues arising from outdated or incorrect information. Regular validation processes help identify discrepancies or inconsistencies in the system, allowing administrators to rectify errors promptly and maintain a reliable foundation for secure access control. By prioritising data accuracy through consistent updates and validation checks, organisations can enhance the overall security posture of their I&A management system.
Implement strict access controls to protect sensitive information.
Implementing strict access controls is a fundamental aspect of safeguarding sensitive information within an Identity and Access Management (I&A) system. By setting up granular permissions and authentication mechanisms, organisations can ensure that only authorised users have access to critical data. This proactive approach not only minimises the risk of data breaches but also helps maintain compliance with regulatory requirements. Strict access controls provide an additional layer of security, reinforcing the overall integrity of the I&A management system and enhancing protection against potential threats.
Train employees on how to use the system effectively to maximise its benefits.
To maximise the benefits of an Identity and Access Management (I&A) system, it is essential to train employees on how to use the system effectively. Providing comprehensive training ensures that users understand the importance of maintaining secure access practices, such as using strong passwords, enabling multi-factor authentication, and following access control policies. By empowering employees with the knowledge and skills to navigate the I&A system efficiently, organisations can enhance data security, improve productivity, and foster a culture of compliance across the workforce.
Regularly audit the system to identify any issues or areas for improvement.
Regularly auditing an Identity and Access Management (I&A) system is essential to maintaining its effectiveness and security. By conducting routine audits, organisations can identify any potential issues, vulnerabilities, or areas for improvement within the system. This proactive approach allows for timely remediation of security gaps, optimisation of access controls, and alignment with evolving business requirements. Regular audits also help ensure compliance with regulations and industry standards, ultimately contributing to a robust and resilient I&A management framework that safeguards critical data and resources.
Integrate the system with other relevant tools and software for seamless operations.
Integrating your Identity and Access Management (I&A) system with other relevant tools and software is a crucial tip for ensuring seamless operations within your organisation. By connecting your I&A system with complementary technologies such as Single Sign-On (SSO), privileged access management, and security information and event management (SIEM) solutions, you can create a unified ecosystem that enhances security, improves user experience, and simplifies administrative tasks. This integration allows for better visibility into user activities, facilitates automated provisioning processes, and enables quick response to security incidents. Overall, integrating your I&A system with other tools paves the way for a more efficient and effective approach to managing identities and access rights across your IT infrastructure.
Establish clear guidelines and procedures for data input and retrieval within the system.
To ensure effective Identity and Access Management (I&A) system operation, it is crucial to establish clear guidelines and procedures for data input and retrieval within the system. By defining specific protocols for how user data is entered into the system and how it can be accessed, organisations can maintain data integrity, prevent unauthorised modifications, and enhance overall security. Clear guidelines also help streamline processes, improve efficiency, and ensure compliance with regulatory requirements. Additionally, having well-defined procedures for data input and retrieval promotes consistency across the organisation and reduces the likelihood of errors or misuse of sensitive information.
Backup data regularly to prevent loss in case of system failures or errors.
Regularly backing up data is a crucial tip in Identity and Access Management (I&A) systems to prevent loss in the event of system failures or errors. By creating routine backups of user identities, access permissions, and audit logs, organisations can ensure that critical information is safeguarded against unexpected incidents. In the event of a system failure or data corruption, having up-to-date backups enables quick restoration of services and minimises downtime, thus maintaining business continuity and preserving the integrity of the I&A management system.
Seek feedback from users to continuously improve the system’s functionality and user experience.
Seeking feedback from users is a valuable practice in Identity and Access Management (I&A) systems as it allows organisations to gather insights directly from those who interact with the system on a daily basis. By soliciting feedback, organisations can identify pain points, usability issues, and areas for improvement, ultimately enhancing the system’s functionality and user experience. This user-centric approach not only fosters a culture of continuous improvement but also ensures that the I&A management system evolves in alignment with user needs and preferences, leading to higher adoption rates and overall satisfaction among stakeholders.