Secure Online Connections with ESET VPN: Protecting Your Privacy and Data
The Benefits of ESET VPN: Ensuring Secure and Private Online Connections
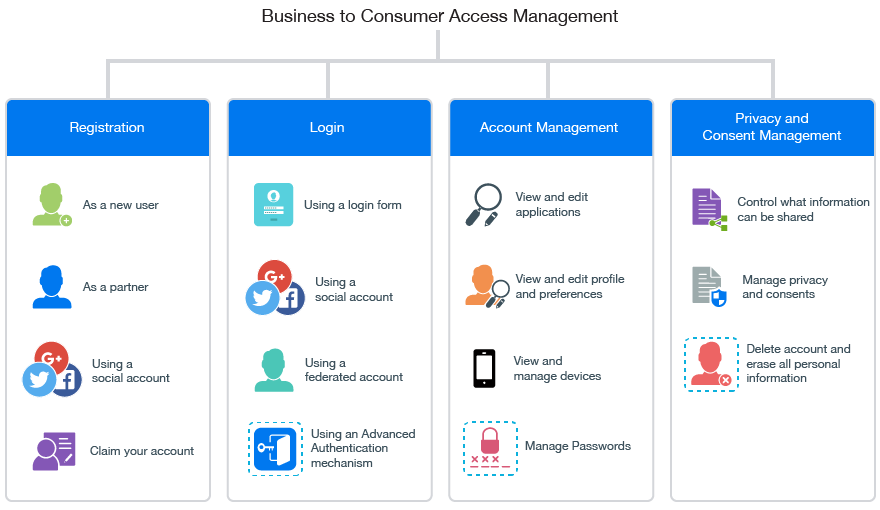
In today’s digital age, where online privacy and security are paramount concerns, using a Virtual Private Network (VPN) has become essential. ESET VPN is a trusted solution that offers a range of benefits for individuals and businesses looking to safeguard their online activities.
Enhanced Security
ESET VPN encrypts your internet connection, ensuring that your data remains secure and protected from cyber threats such as hacking, surveillance, and identity theft. By routing your online traffic through a secure server, ESET VPN shields your sensitive information from prying eyes, providing you with peace of mind while browsing the web.
Privacy Protection
With ESET VPN, you can browse the internet anonymously without revealing your IP address or location. This anonymity prevents advertisers, ISPs, or other third parties from tracking your online activities and collecting data about you. By masking your digital footprint, ESET VPN helps preserve your privacy online.
Bypassing Geographical Restrictions
ESET VPN allows you to access geo-blocked content by connecting to servers in different locations around the world. Whether you want to stream region-locked videos, access restricted websites, or use services not available in your country, ESET VPN enables you to bypass these limitations and enjoy unrestricted internet access.
Secure Remote Access
For businesses with remote employees or multiple office locations, ESET VPN provides a secure way to connect to corporate networks over the internet. By establishing encrypted tunnels between devices and company servers, ESET VPN ensures that sensitive business data remains protected during remote work scenarios.
User-Friendly Interface
ESET VPN offers an intuitive interface that makes it easy for users to set up and use the service. With simple configuration options and one-click connectivity features, even those new to VPNs can quickly start enjoying the benefits of enhanced security and privacy provided by ESET VPN.
Conclusion
In conclusion, ESET VPN is a reliable solution for individuals and businesses seeking to fortify their online security and privacy. With its robust encryption protocols, anonymous browsing capabilities, geo-spoofing features, secure remote access functionality, and user-friendly interface, ESET VPN stands out as a top choice for safeguarding online connections in an increasingly digital world.
7 Essential Tips for Optimising Your ESET VPN Experience
- Ensure your ESET VPN is always up to date for the latest security features.
- Choose a server location closest to you for faster connection speeds.
- Enable the kill switch feature to ensure your internet traffic is secure even if the VPN connection drops.
- Avoid using public Wi-Fi networks without connecting to your ESET VPN for added security.
- Customize your VPN settings to suit your specific privacy and security needs.
- Regularly monitor your VPN usage and settings for any unusual activity or changes.
- Consider using a dedicated IP address with your ESET VPN for more consistent access.
Ensure your ESET VPN is always up to date for the latest security features.
To maximise the security benefits of ESET VPN, it is crucial to ensure that your software is always up to date. By regularly updating your ESET VPN, you can access the latest security features and enhancements that help protect your online activities from evolving cyber threats. Keeping your VPN software current not only strengthens your defences but also ensures that you are equipped with the most effective tools to safeguard your privacy and data while browsing the internet.
Choose a server location closest to you for faster connection speeds.
To optimise your connection speeds while using ESET VPN, it is advisable to select a server location that is geographically closest to your current location. By choosing a server in proximity to you, you can reduce latency and ensure faster data transmission, enhancing your overall browsing experience. This strategic selection helps minimise network congestion and improves the efficiency of your online activities, allowing you to enjoy seamless and swift VPN connections with ESET VPN.
Enable the kill switch feature to ensure your internet traffic is secure even if the VPN connection drops.
By enabling the kill switch feature on ESET VPN, you can safeguard your internet traffic even in the event of a VPN connection drop. This essential feature acts as a fail-safe mechanism, instantly cutting off internet access if the VPN connection is interrupted, preventing any data leakage or exposure to potential security risks. With the kill switch activated, you can rest assured that your online activities remain protected and confidential at all times, maintaining a secure digital environment for your browsing and communication needs.
Avoid using public Wi-Fi networks without connecting to your ESET VPN for added security.
When using public Wi-Fi networks, it is crucial to prioritise your online security by avoiding connecting without the protection of your ESET VPN. Public Wi-Fi hotspots are notorious for their vulnerabilities, making users susceptible to cyber threats such as hacking and data interception. By ensuring that you always connect to your ESET VPN before accessing public Wi-Fi networks, you can significantly enhance the security of your internet connection and safeguard your sensitive information from potential risks.
Customize your VPN settings to suit your specific privacy and security needs.
Customising your ESET VPN settings allows you to tailor the level of privacy and security to meet your individual requirements. By adjusting parameters such as encryption protocols, server locations, and connection preferences, you can enhance the protection of your online activities according to your specific needs. Whether you prioritise anonymity, speed, or accessing geo-restricted content, customising your VPN settings ensures that your online experience is optimised for both security and convenience. Take advantage of the flexibility offered by ESET VPN to create a personalised and secure browsing environment that aligns with your privacy preferences.
Regularly monitor your VPN usage and settings for any unusual activity or changes.
Regularly monitoring your ESET VPN usage and settings is a crucial tip to ensure the ongoing security and effectiveness of your online activities. By staying vigilant and checking for any unusual activity or unexpected changes, you can promptly identify and address potential security threats or breaches. Monitoring allows you to maintain control over your VPN connections, ensuring that your data remains protected and that your privacy is upheld. By incorporating this practice into your routine, you can proactively safeguard your online experience and maintain peace of mind while browsing the web.
Consider using a dedicated IP address with your ESET VPN for more consistent access.
When using ESET VPN, it is advisable to consider utilising a dedicated IP address to enhance the consistency of your access. By opting for a dedicated IP, you ensure that your online activities are associated with a specific, unchanging address, which can be beneficial for maintaining stable and reliable connections. This approach can be particularly useful for tasks that require uninterrupted access, such as online gaming, video streaming, or accessing secure networks. With a dedicated IP address through ESET VPN, you can enjoy a more consistent and seamless online experience while maximising the security and privacy benefits of the service.