Ensuring HIPAA Compliant Document Management
Healthcare organisations handle a vast amount of sensitive patient information on a daily basis. To safeguard this data and comply with regulations, such as the Health Insurance Portability and Accountability Act (HIPAA), it is crucial to implement robust document management practices.
Understanding HIPAA Compliance
HIPAA sets the standard for protecting sensitive patient data. Compliance with HIPAA regulations is not optional – it is a legal requirement for healthcare providers, insurers, and their business associates. Failure to comply can result in severe penalties and reputational damage.
The Importance of Document Management
Document management plays a key role in maintaining HIPAA compliance. It involves the creation, storage, retrieval, and disposal of documents in a secure and organised manner. By implementing effective document management practices, healthcare organisations can ensure the confidentiality, integrity, and availability of patient information.
Key Considerations for HIPAA Compliant Document Management
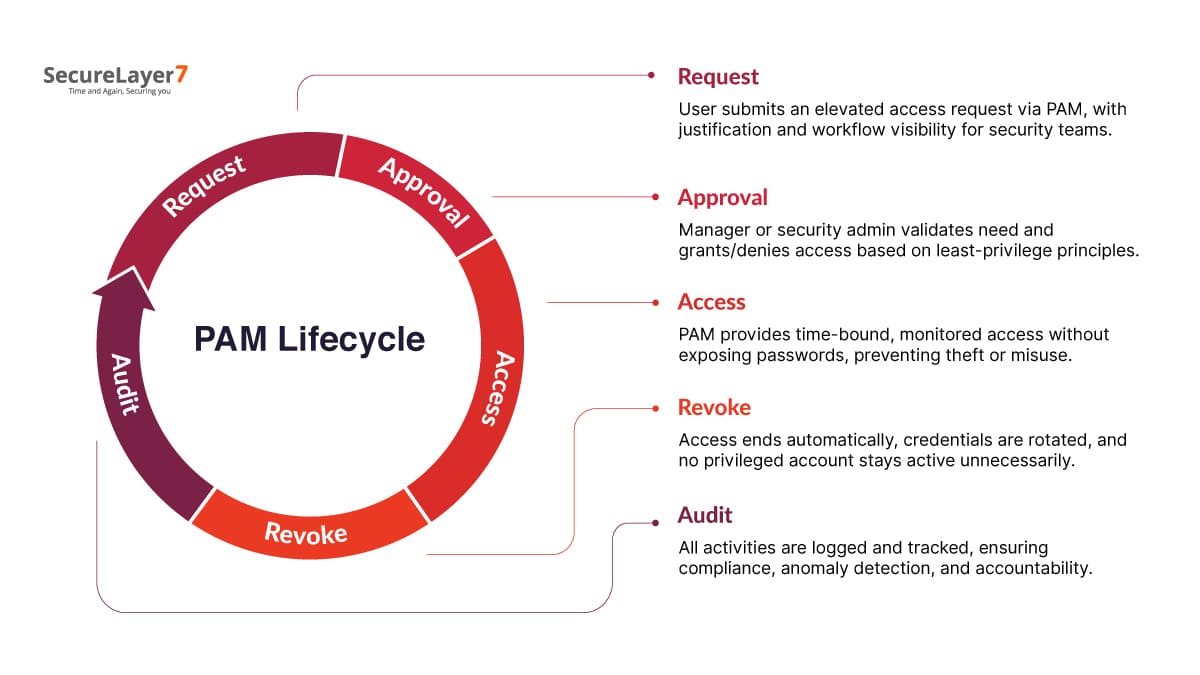
- Access Control: Limit access to patient records to authorised personnel only. Implement role-based access controls to ensure that employees can only view or modify documents relevant to their job responsibilities.
- Audit Trails: Maintain detailed audit trails that track who accessed patient records, when they were accessed, and any modifications made. This helps in monitoring document activity and detecting any unauthorised access.
- Data Encryption: Encrypt sensitive patient data both at rest and in transit to protect it from unauthorised disclosure. Encryption helps safeguard information from cyber threats and ensures compliance with HIPAA’s security requirements.
- Document Retention Policies: Establish clear guidelines for how long patient records should be retained and when they should be securely disposed of. Adhering to document retention policies helps prevent unnecessary data storage and minimises the risk of data breaches.
- Training and Awareness: Provide regular training sessions to employees on HIPAA regulations, document management best practices, and cybersecurity awareness. Educating staff members on their responsibilities helps mitigate risks associated with non-compliance.
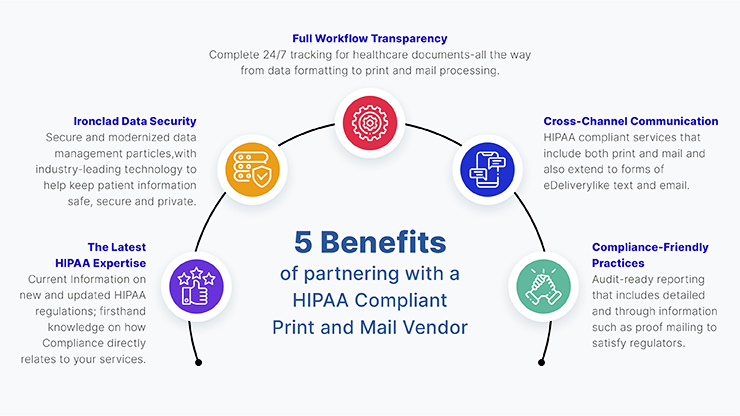
The Benefits of HIPAA Compliant Document Management
By prioritising HIPAA compliant document management practices, healthcare organisations can benefit in various ways:
- Data Security: Protect sensitive patient information from unauthorised access or disclosure.
- Lega…
Understanding HIPAA Compliant Document Management: Answers to 7 Key Questions
- What is the alternative to DocuSign for HIPAA?
- Is there a HIPAA compliant ChatGP?
- What is a HIPAA compliant system?
- What is a HIPAA compliant software?
- What is HIPAA compliant?
- How do you make data HIPAA compliant?
- What are the top 5 document management systems?
What is the alternative to DocuSign for HIPAA?
When seeking an alternative to DocuSign for HIPAA compliant document management, organisations can explore solutions such as Adobe Sign or HelloSign. These platforms offer robust security features and encryption protocols to ensure the confidentiality of sensitive patient information in accordance with HIPAA regulations. By evaluating the specific requirements of their document management processes and comparing the features of different providers, healthcare entities can choose a suitable alternative that meets their compliance needs while streamlining document workflows effectively.
Is there a HIPAA compliant ChatGP?
When considering HIPAA compliant document management, a common question that arises is whether there is a HIPAA compliant ChatGP available. Ensuring the confidentiality and security of patient information during electronic communications, such as chat platforms, is crucial for maintaining HIPAA compliance. Healthcare providers seeking to use a chat platform for patient interactions must carefully assess its security features, encryption protocols, access controls, and data storage practices to determine if it meets HIPAA requirements. Choosing a ChatGP that adheres to HIPAA standards can help healthcare organisations facilitate secure and compliant communication with patients while safeguarding sensitive health data.
What is a HIPAA compliant system?
A HIPAA compliant system refers to an information technology infrastructure or software solution that adheres to the regulations outlined in the Health Insurance Portability and Accountability Act (HIPAA). Such a system ensures the secure handling of sensitive patient data within healthcare organisations. To be considered HIPAA compliant, a system must implement robust security measures, access controls, encryption protocols, audit trails, and other safeguards to protect patient information from unauthorised access or disclosure. By using a HIPAA compliant system, healthcare providers can maintain the confidentiality, integrity, and availability of patient data while meeting the legal requirements set forth by HIPAA to safeguard patient privacy and security.
What is a HIPAA compliant software?
A HIPAA compliant software refers to a digital solution or platform that adheres to the regulations outlined in the Health Insurance Portability and Accountability Act (HIPAA). Such software ensures that sensitive patient data is handled securely and in accordance with HIPAA’s privacy and security rules. A HIPAA compliant software typically incorporates features such as encryption, access controls, audit trails, and regular security updates to safeguard patient information from unauthorised access or disclosure. By using HIPAA compliant software, healthcare organisations can enhance their document management practices, maintain compliance with regulatory requirements, and protect the confidentiality of patient records.
What is HIPAA compliant?
HIPAA compliance refers to adhering to the regulations outlined in the Health Insurance Portability and Accountability Act (HIPAA) to ensure the protection of sensitive patient information within the healthcare industry. Being HIPAA compliant means that healthcare organisations, insurers, and their business associates have implemented stringent security measures and privacy practices to safeguard patient data from unauthorised access, disclosure, or misuse. It involves establishing strict protocols for handling patient records, maintaining confidentiality, securing electronic communications, and ensuring that individuals have control over their personal health information. Compliance with HIPAA regulations is essential for maintaining trust with patients, avoiding costly penalties, and upholding the integrity of healthcare operations.
How do you make data HIPAA compliant?
Ensuring data HIPAA compliance involves implementing a comprehensive set of measures to safeguard sensitive patient information. To make data HIPAA compliant, healthcare organisations must start by conducting a thorough risk assessment to identify vulnerabilities and risks to data security. Implementing robust access controls, encryption protocols, and audit trails are essential steps in protecting data integrity and confidentiality. Establishing clear data retention policies and providing regular training to staff on HIPAA regulations are also crucial in maintaining compliance. Regular monitoring and auditing of data handling practices help ensure ongoing adherence to HIPAA requirements and mitigate the risk of potential breaches.
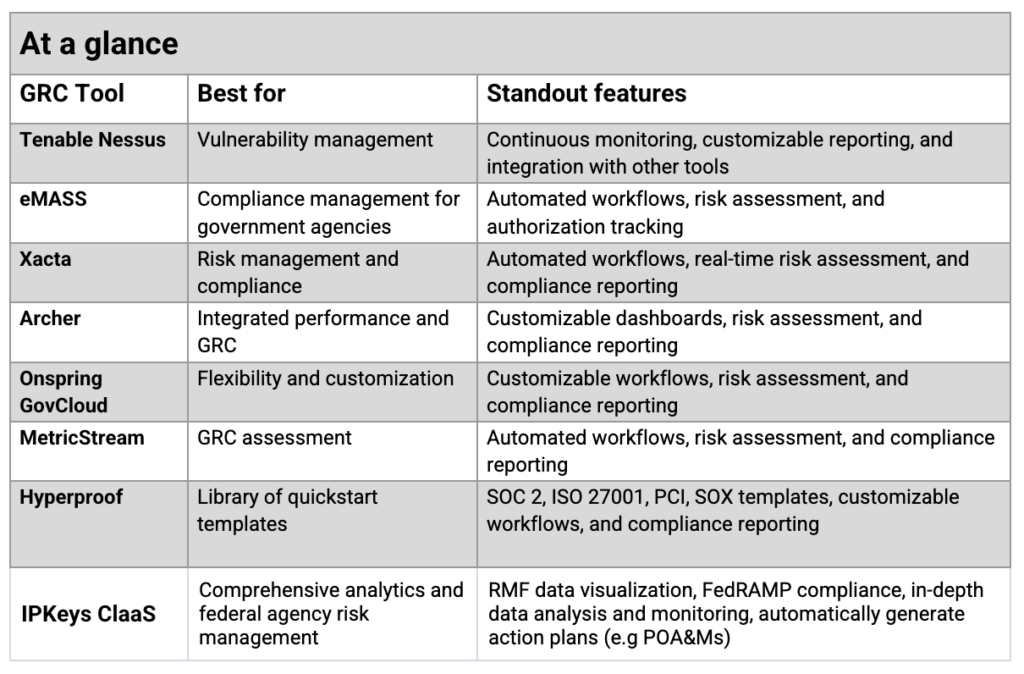
What are the top 5 document management systems?
When it comes to HIPAA compliant document management systems, there are several top options that healthcare organisations can consider. Some of the leading document management systems known for their robust features and compliance capabilities include Microsoft SharePoint, M-Files, Laserfiche, DocuWare, and OpenText Documentum. These systems offer secure storage, access controls, audit trails, encryption features, and integration capabilities to help healthcare providers effectively manage and protect sensitive patient information while ensuring compliance with HIPAA regulations. Choosing the right document management system tailored to the specific needs of the organisation is essential for maintaining data security and regulatory compliance in the healthcare industry.