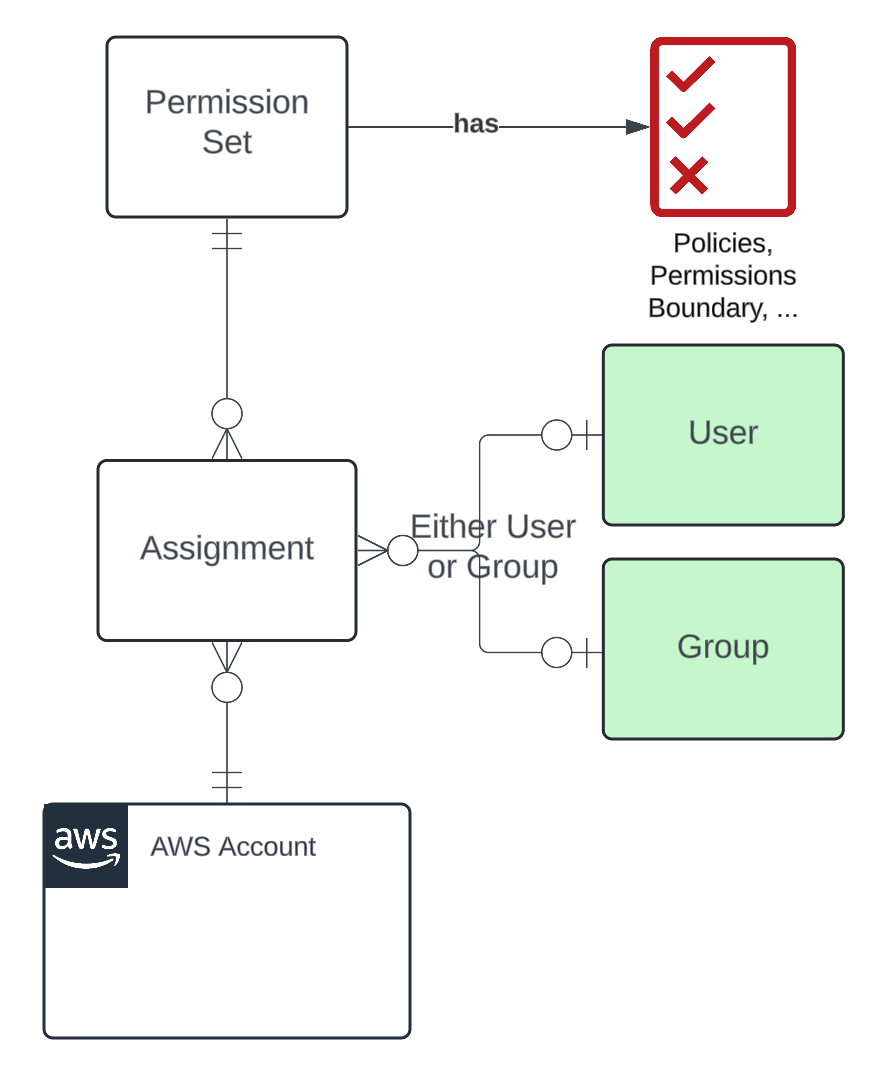
The Rise of Hybrid Web Access Management
In today’s digital landscape, businesses are increasingly adopting hybrid web access management solutions to address the complex challenges of secure user authentication and authorisation. This innovative approach combines the benefits of both on-premises and cloud-based systems to provide a seamless and robust security framework.
Benefits of Hybrid Web Access Management
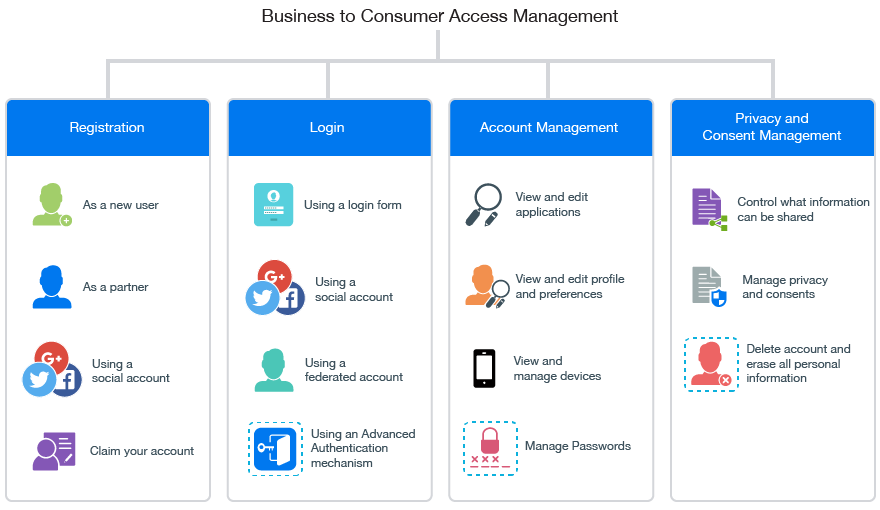
One of the key advantages of hybrid web access management is its flexibility. Organisations can leverage their existing on-premises infrastructure while also taking advantage of the scalability and accessibility offered by cloud solutions. This hybrid model allows for a more tailored approach to security, accommodating diverse user needs and evolving business requirements.
Moreover, hybrid web access management enhances user experience by providing a unified login process across various applications and platforms. Users can enjoy streamlined access without compromising security, thanks to advanced authentication mechanisms and adaptive policies that adapt to different risk levels.
Challenges and Considerations
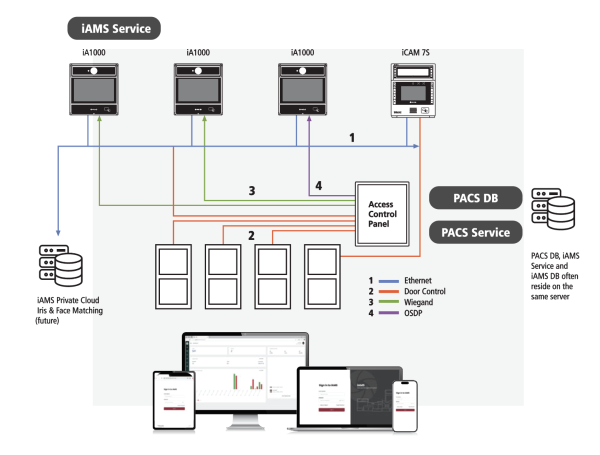
Despite its numerous benefits, implementing a hybrid web access management solution comes with its own set of challenges. Ensuring seamless integration between on-premises and cloud components requires careful planning and expertise. Additionally, maintaining consistent security standards across hybrid environments demands continuous monitoring and updates.
Organisations considering a hybrid approach must carefully evaluate their specific needs, compliance requirements, and budget constraints. Collaboration between IT teams, security experts, and stakeholders is essential to develop a comprehensive strategy that aligns with business goals while mitigating potential risks.
The Future of Hybrid Web Access Management
As cyber threats continue to evolve, the role of hybrid web access management in safeguarding sensitive data and resources will become increasingly crucial. By combining the strengths of on-premises and cloud technologies, organisations can establish a resilient security framework that adapts to changing threat landscapes.
Looking ahead, advancements in artificial intelligence and machine learning are expected to further enhance the capabilities of hybrid web access management systems. These technologies will enable proactive threat detection, behavioural analytics, and dynamic policy enforcement for improved security posture.
Understanding Hybrid Web Access Management: Key Questions and Insights
- What is hybrid web access management?
- How does hybrid web access management differ from traditional access management?
- What are the benefits of implementing a hybrid web access management solution?
- What challenges may arise when integrating on-premises and cloud components in hybrid web access management?
- How can organisations ensure the security of their data and resources in a hybrid web access management environment?
- What are the future trends and advancements expected in the field of hybrid web access management?
What is hybrid web access management?
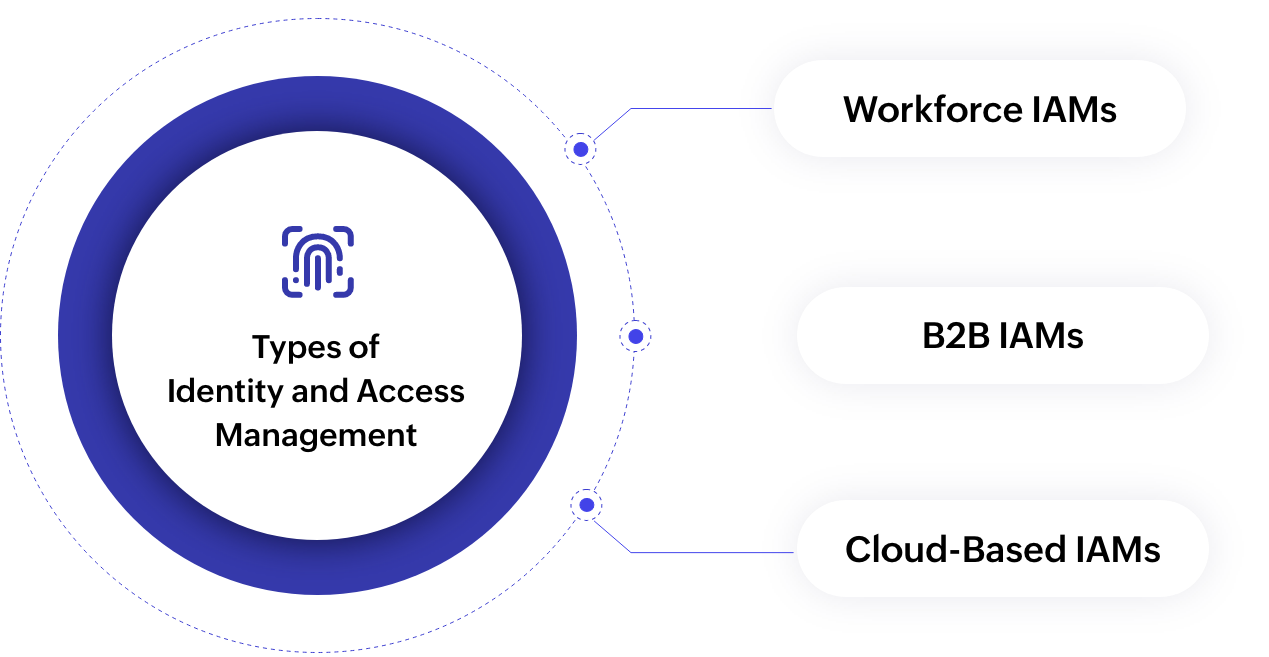
Hybrid web access management refers to a comprehensive security approach that combines elements of both on-premises and cloud-based systems to ensure secure user authentication and authorisation across various applications and platforms. This innovative model allows organisations to leverage the strengths of their existing infrastructure while taking advantage of the scalability and flexibility offered by cloud solutions. By integrating on-premises and cloud components, hybrid web access management provides a seamless user experience, robust security measures, and adaptive policies that cater to diverse user needs and evolving business requirements.
How does hybrid web access management differ from traditional access management?
Hybrid web access management differs from traditional access management by combining the strengths of both on-premises and cloud-based solutions to create a more versatile and comprehensive security framework. While traditional access management systems are typically limited to on-premises environments, hybrid solutions offer the flexibility to leverage cloud services for enhanced scalability and accessibility. This approach allows organisations to adapt to evolving business needs and user requirements more effectively. Additionally, hybrid web access management often incorporates advanced authentication mechanisms and adaptive policies that provide a seamless user experience while maintaining robust security measures across diverse platforms and applications.
What are the benefits of implementing a hybrid web access management solution?
Implementing a hybrid web access management solution offers a range of benefits for organisations seeking to enhance their security posture and user experience. By combining on-premises and cloud-based systems, businesses can leverage the scalability and flexibility of cloud technologies while utilising existing infrastructure investments. This hybrid approach allows for seamless integration across various applications and platforms, providing users with a unified login experience. Enhanced security features, such as advanced authentication methods and adaptive policies, ensure robust protection against evolving cyber threats while accommodating diverse user needs. Overall, a hybrid web access management solution delivers improved security, efficiency, and user satisfaction, making it a valuable investment for modern businesses.
What challenges may arise when integrating on-premises and cloud components in hybrid web access management?
When integrating on-premises and cloud components in hybrid web access management, several challenges may arise. One common challenge is ensuring seamless interoperability between different systems and platforms, as on-premises and cloud environments may have distinct architectures and security protocols. Maintaining consistent security standards across hybrid infrastructures is another critical issue, requiring robust authentication mechanisms, encryption protocols, and access control policies to protect sensitive data. Additionally, managing user identities and access rights across diverse environments can be complex, necessitating careful planning and coordination to prevent security gaps or compliance violations. Effective communication between IT teams, security experts, and stakeholders is essential to address these challenges proactively and ensure a smooth integration process that enhances both security and user experience.
How can organisations ensure the security of their data and resources in a hybrid web access management environment?
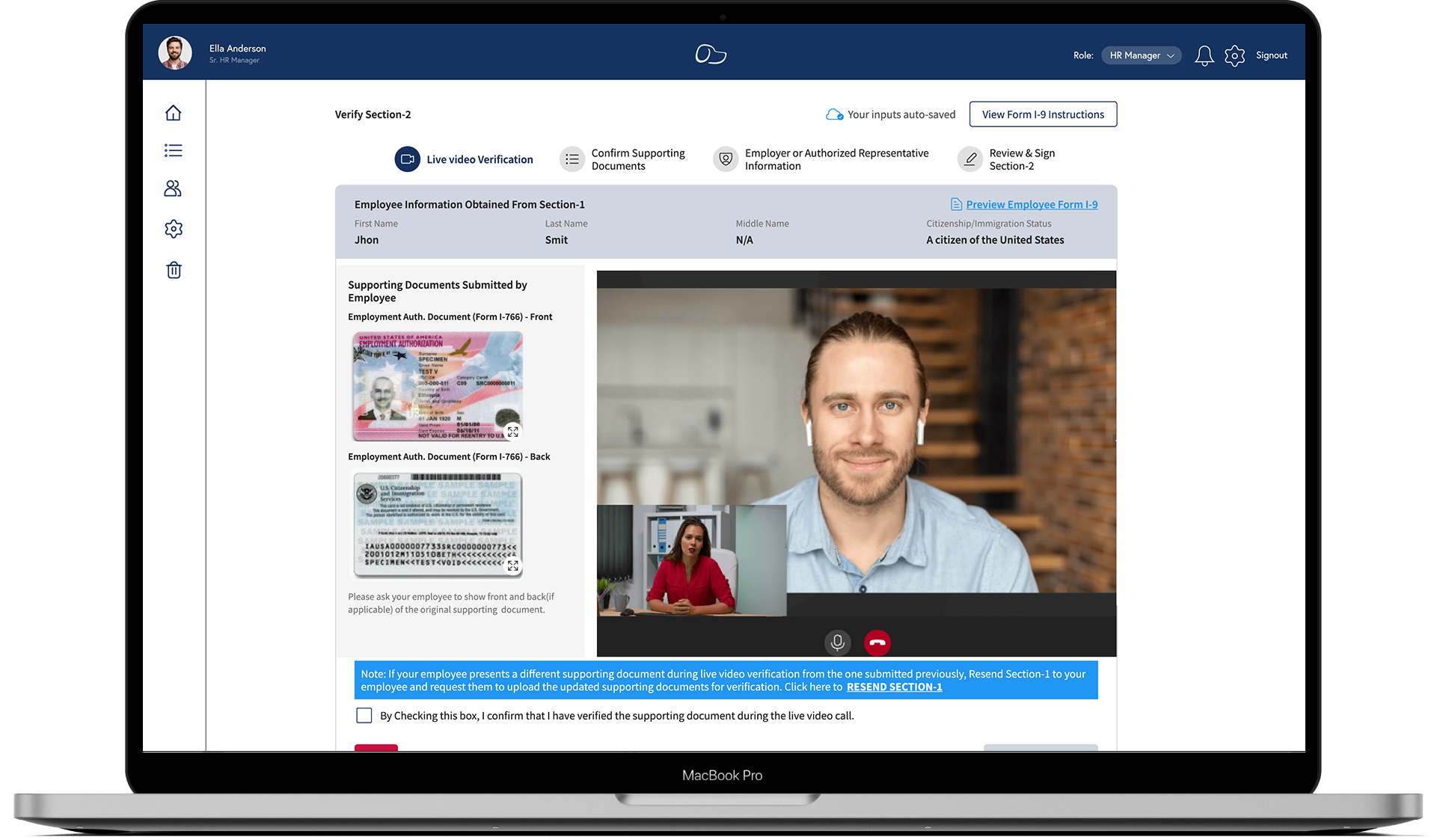
In a hybrid web access management environment, organisations can ensure the security of their data and resources by implementing a comprehensive security strategy that combines best practices from both on-premises and cloud-based systems. Utilising strong authentication methods such as multi-factor authentication and single sign-on, organisations can verify user identities and control access to sensitive information. Encryption protocols should be employed to protect data both in transit and at rest, while regular security audits and monitoring help detect and mitigate potential threats. Establishing clear access controls, enforcing least privilege principles, and educating users on cybersecurity best practices are also essential steps in safeguarding data integrity and resource confidentiality in a hybrid web access management setting.
What are the future trends and advancements expected in the field of hybrid web access management?
In the realm of hybrid web access management, future trends and advancements are poised to revolutionise the way organisations approach security and user authentication. Anticipated developments include a greater emphasis on interoperability between on-premises and cloud-based systems, enabling seamless access across diverse environments. Enhanced user-centric authentication methods, such as biometrics and adaptive authentication, are expected to become more prevalent to bolster security while improving user experience. Moreover, the integration of artificial intelligence and machine learning algorithms will play a pivotal role in detecting anomalies, predicting threats, and automating response mechanisms within hybrid web access management frameworks. These advancements signify a shift towards proactive, intelligent security solutions that adapt to evolving cyber threats and business requirements.