The Importance of Entitlement Management in Azure Active Directory
Managing user access and permissions within an organisation’s IT infrastructure is crucial for maintaining security and compliance. In the context of Azure Active Directory (Azure AD), entitlement management plays a key role in ensuring that users have the appropriate level of access to resources while preventing unauthorised activities.
What is Entitlement Management?
Entitlement management in Azure AD involves defining and controlling the specific permissions and privileges that users have within the directory. This includes regulating access to applications, data, and other resources based on roles, responsibilities, and business needs.
The Benefits of Entitlement Management
Effective entitlement management offers several benefits to organisations:
- Enhanced Security: By assigning access rights based on predefined roles and responsibilities, organisations can reduce the risk of data breaches and insider threats.
- Compliance: Entitlement management helps organisations meet regulatory requirements by ensuring that only authorised individuals have access to sensitive information.
- Operational Efficiency: Streamlining access control processes through automated workflows can improve efficiency and reduce administrative burden.
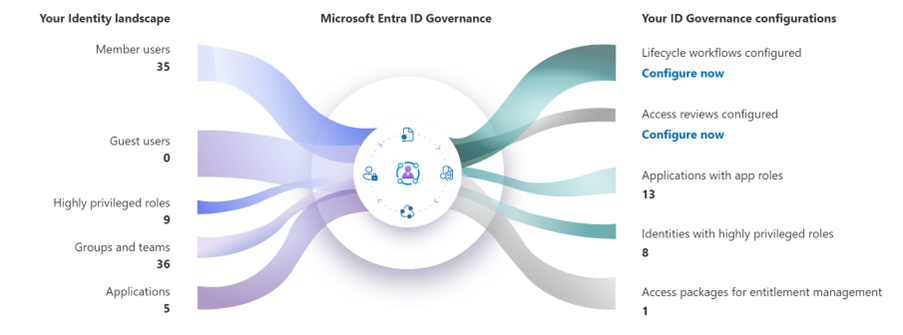
- Auditability: Tracking user entitlements allows organisations to monitor access patterns, detect anomalies, and maintain a comprehensive audit trail for compliance purposes.
Implementing Entitlement Management in Azure AD
Azure AD provides robust capabilities for managing entitlements, including role-based access control (RBAC), privileged identity management (PIM), and conditional access policies. Organisations can leverage these features to define roles, assign permissions dynamically, enforce multi-factor authentication, and more.
Best Practices for Entitlement Management
To maximise the effectiveness of entitlement management in Azure AD, organisations should consider the following best practices:
- Regular Access Reviews: Conduct periodic reviews of user entitlements to ensure that permissions are up-to-date and aligned with business requirements.
- Segregation of Duties: Implement controls to prevent conflicts of interest by separating duties among different users or roles.
- Auditing and Monitoring: Monitor user activity, generate reports on access rights changes, and proactively address any suspicious behaviour.
- User Training: Educate employees on security best practices, data handling policies, and the importance of safeguarding their credentials.
In conclusion, effective entitlement management is essential for maintaining a secure and compliant IT environment in Azure Active Directory. By implementing proper controls, leveraging automation tools, and following best practices, organisations can mitigate risks associated with unauthorised access while enabling seamless collaboration across their digital ecosystem.
Understanding Entitlement Management in Azure AD: Key FAQs and Insights
- What is cloud entitlement management?
- What is an entitlement in Active Directory?
- What is entitlement management in Azure AD?
- What is entitlements management?
- What is entitlement management Azure AD?
- What problem does the entitlement management feature help address?
- What is an IAM entitlement?
What is cloud entitlement management?
Cloud entitlement management refers to the process of controlling and regulating user access to cloud-based resources and services within an organisation’s digital ecosystem. In the context of Azure Active Directory (Azure AD), cloud entitlement management involves defining and managing permissions, roles, and privileges for users accessing cloud applications and data. By implementing robust entitlement management practices in the cloud, organisations can enhance security, enforce compliance with data protection regulations, streamline access control processes, and ensure that users have the appropriate level of access to resources based on their roles and responsibilities.
What is an entitlement in Active Directory?
In the context of Active Directory, an entitlement refers to the specific privileges or permissions granted to users or groups within the directory. These entitlements dictate what actions a user can perform, what resources they can access, and under what conditions. By defining entitlements accurately based on roles and responsibilities, organisations can ensure that users have the appropriate level of access to resources while maintaining security and compliance. Managing entitlements effectively in Active Directory is crucial for safeguarding sensitive data, preventing unauthorised activities, and maintaining a robust security posture across the IT infrastructure.
What is entitlement management in Azure AD?
Entitlement management in Azure Active Directory refers to the process of defining and controlling user access rights to resources within the Azure AD environment. It involves assigning specific permissions and privileges based on roles, responsibilities, and business needs to ensure that users have appropriate levels of access while maintaining security and compliance. By implementing entitlement management in Azure AD, organisations can effectively manage user permissions, reduce the risk of data breaches, meet regulatory requirements, improve operational efficiency, and maintain a comprehensive audit trail for monitoring access patterns.
What is entitlements management?
Entitlement management, in the context of Azure Active Directory, refers to the process of defining and controlling the specific permissions and privileges that users have within the directory. It involves assigning access rights based on predefined roles and responsibilities, ensuring that individuals have appropriate levels of access to applications, data, and other resources based on their job functions. By implementing entitlement management practices, organisations can enhance security by reducing the risk of unauthorised access, improve compliance with regulatory requirements, streamline access control processes for operational efficiency, and maintain auditability through monitoring user entitlements.
What is entitlement management Azure AD?
Entitlement management in Azure Active Directory (Azure AD) refers to the process of defining and regulating user access to resources within the directory based on predefined roles and permissions. It allows organisations to effectively manage who has access to what, ensuring that users only have the necessary privileges to perform their job functions while safeguarding sensitive data and applications. By implementing entitlement management in Azure AD, organisations can enhance security, streamline access control processes, maintain compliance with regulations, and improve overall operational efficiency.
What problem does the entitlement management feature help address?
The entitlement management feature in Azure Active Directory helps address the critical issue of managing user access and permissions effectively within an organisation’s IT infrastructure. One common problem that this feature resolves is the challenge of ensuring that users have the appropriate level of access to resources while maintaining security and compliance. By defining and controlling specific permissions based on roles and responsibilities, entitlement management helps prevent unauthorised access to sensitive data, reduces the risk of insider threats, and streamlines access control processes. This feature also aids in meeting regulatory requirements by providing a structured approach to assigning and monitoring user entitlements, thus enhancing overall security posture and operational efficiency.
What is an IAM entitlement?
An IAM entitlement, in the context of Azure Active Directory (Azure AD) and Identity and Access Management (IAM), refers to the specific permissions or access rights granted to a user or group within an organisation’s IT environment. These entitlements dictate what resources, applications, or data a user can interact with based on their role, responsibilities, and business needs. By defining IAM entitlements accurately, organisations can ensure that users have the appropriate level of access to perform their job functions effectively while maintaining security and compliance standards. Regularly reviewing and managing IAM entitlements is essential to prevent unauthorised access and reduce the risk of security breaches.