Securing Your Digital Assets: The Power of Cloud Identity Management
The Importance of Cloud Identity Management
In today’s digital age, where businesses are increasingly moving towards cloud-based solutions, the need for robust cloud identity management has never been more critical. Cloud identity management refers to the processes and technologies used to manage and secure digital identities across cloud applications and services.
One of the key benefits of cloud identity management is enhanced security. With employees accessing company resources from various devices and locations, traditional on-premises identity management systems are no longer sufficient. Cloud identity management provides a centralised way to control access to applications and data, ensuring that only authorised users can log in and perform actions.
Scalability is another advantage of cloud identity management. As businesses grow and adopt more cloud services, managing user identities manually becomes increasingly complex. Cloud identity management platforms can scale effortlessly to accommodate new users, applications, and devices without compromising security or efficiency.
Furthermore, cloud identity management promotes productivity by simplifying user access to resources. Single sign-on (SSO) capabilities allow users to log in once and access multiple applications seamlessly, reducing the need to remember multiple passwords. This not only enhances user experience but also minimises the risk of password-related security incidents.
Compliance requirements are also easier to meet with cloud identity management solutions. By enforcing access controls, monitoring user activities, and generating audit reports, businesses can demonstrate compliance with regulations such as GDPR or HIPAA more effectively.
In conclusion, investing in robust cloud identity management is essential for modern businesses looking to secure their digital assets, streamline access control processes, and ensure compliance with regulatory standards. By leveraging the benefits of cloud-based identity solutions, organisations can enhance security posture, improve operational efficiency, and empower their workforce in an increasingly digital world.
Understanding Cloud Identity Management: Key Concepts and FAQs
- How to identity management is done in cloud computing?
- What is Cloud Identity access management why it is important?
- What is IdM vs IAM?
- What is a cloud identity platform?
- What is cloud identity management?
How to identity management is done in cloud computing?
In cloud computing, identity management is typically achieved through the use of specialised cloud identity management services or platforms. These services allow organisations to centralise user authentication, authorisation, and access control for their cloud-based resources. Users are assigned unique digital identities that grant them specific permissions based on predefined policies. Multi-factor authentication, single sign-on, and role-based access control are common features used to enhance security and streamline user access in cloud environments. By leveraging cloud identity management solutions, businesses can effectively manage user identities across various cloud services while ensuring data security and regulatory compliance.
What is Cloud Identity access management why it is important?
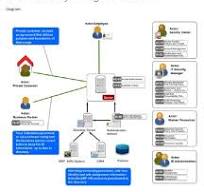
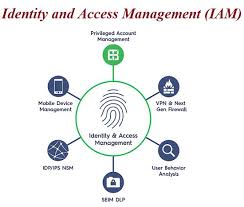
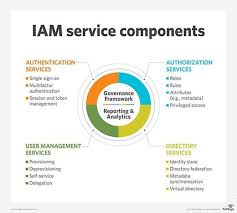
Cloud Identity Access Management (IAM) is a crucial aspect of cloud security that focuses on controlling and managing user access to cloud resources. It involves defining and enforcing policies that determine who has access to what within a cloud environment. Cloud IAM plays a vital role in ensuring that only authorised individuals can log in, access data, and perform actions within cloud applications and services. This is important because it helps prevent unauthorised access, data breaches, and misuse of sensitive information. By implementing robust Cloud IAM practices, organisations can enhance their overall security posture, maintain compliance with regulations, and safeguard their digital assets from potential threats.
What is IdM vs IAM?
In the realm of cloud identity management, a common query revolves around distinguishing between IdM (Identity Management) and IAM (Identity and Access Management). IdM primarily focuses on managing digital identities, encompassing tasks such as user authentication, provisioning, and deprovisioning. On the other hand, IAM extends beyond identity management to include controlling user access to resources based on predefined policies and permissions. While IdM lays the foundation by establishing and maintaining user identities, IAM builds upon this foundation to govern access rights and privileges within an organisation’s IT ecosystem. Understanding the nuances between IdM and IAM is crucial for implementing a comprehensive cloud identity strategy that effectively safeguards data integrity and enhances operational efficiency.
What is a cloud identity platform?
A cloud identity platform is a comprehensive solution designed to manage and secure digital identities across cloud applications and services. It serves as a centralised system for controlling user access to resources in the cloud, offering functionalities such as user authentication, authorisation, and identity governance. By leveraging a cloud identity platform, organisations can streamline their identity management processes, enhance security measures, and ensure compliance with regulatory standards. These platforms often include features like single sign-on (SSO), multi-factor authentication (MFA), and user provisioning to provide a seamless and secure user experience while maintaining control over access privileges.
What is cloud identity management?
Cloud identity management, in the context of cloud computing, refers to the practices and technologies used to securely manage and control user identities within cloud-based applications and services. It involves authenticating users, authorising access to resources, and enforcing security policies across a distributed network of cloud environments. Essentially, cloud identity management ensures that only authorised individuals can access specific data or applications in the cloud, enhancing security, scalability, and user productivity. By centralising identity management processes in the cloud, organisations can streamline access controls, simplify user authentication, and maintain compliance with regulatory requirements more effectively.