The Importance of Enterprise Identity in Modern Business
In today’s digital age, where data breaches and cyber threats are on the rise, establishing a robust enterprise identity framework is crucial for the security and efficiency of any business. Enterprise identity refers to the management of digital identities within an organisation, encompassing employees, customers, partners, and other stakeholders.
One of the primary reasons why enterprise identity is essential is security. By implementing strong authentication mechanisms and access controls, businesses can safeguard their sensitive information from unauthorised access. A well-defined enterprise identity strategy ensures that only authorised individuals have access to specific resources, reducing the risk of data breaches and insider threats.
Moreover, enterprise identity plays a vital role in enhancing user experience and productivity. With a centralised identity management system, employees can seamlessly access the tools and applications they need to perform their tasks efficiently. Single sign-on capabilities streamline authentication processes, eliminating the need for multiple passwords and reducing user frustration.
From a compliance perspective, maintaining a comprehensive enterprise identity framework is essential for meeting regulatory requirements such as GDPR, HIPAA, and PCI DSS. By accurately managing user identities and permissions, businesses can demonstrate compliance with data protection laws and industry standards, avoiding costly fines and reputational damage.
As businesses continue to embrace cloud services and remote work arrangements, the need for a robust enterprise identity strategy becomes even more critical. Identity federation allows organisations to securely extend their identities beyond traditional boundaries, enabling seamless collaboration with external partners while maintaining control over access rights.
In conclusion, enterprise identity is not just about managing usernames and passwords; it is about establishing a comprehensive framework that protects sensitive data, enhances user experience, ensures compliance with regulations, and supports business growth. By investing in robust identity management solutions, businesses can strengthen their security posture and position themselves for success in an increasingly digital world.
7 Key Advantages of Enterprise Identity Management: Enhancing Security, Compliance, and Productivity
- Enhances security by implementing strong authentication measures
- Improves user experience with seamless access to resources
- Increases productivity by streamlining authentication processes
- Ensures compliance with data protection regulations and industry standards
- Facilitates secure collaboration with external partners through identity federation
- Centralises identity management for easier administration and control
- Supports business growth in the digital age by protecting sensitive information
Five Key Drawbacks of Enterprise Identity: Complexity, Cost, User Resistance, Security Risks, and Integration Challenges
Enhances security by implementing strong authentication measures
Enhancing security through the implementation of robust authentication measures is a key advantage of enterprise identity management. By requiring strong authentication methods such as multi-factor authentication and biometric verification, organisations can significantly reduce the risk of unauthorised access to sensitive data and resources. This proactive approach not only strengthens the overall security posture but also helps mitigate potential threats posed by cybercriminals seeking to exploit vulnerabilities in traditional password-based systems. With strong authentication measures in place, businesses can bolster their defences against evolving cyber threats and safeguard their critical assets more effectively.
Improves user experience with seamless access to resources
By implementing enterprise identity solutions, businesses can significantly enhance user experience by providing seamless access to resources. With a centralised identity management system in place, employees can easily navigate through various tools and applications without the hassle of multiple logins. This streamlined approach not only saves time but also boosts productivity as users can focus on their tasks rather than authentication processes. By offering a frictionless experience, enterprise identity solutions contribute to a more efficient and user-friendly work environment, ultimately benefiting both employees and the organisation as a whole.
Increases productivity by streamlining authentication processes
By streamlining authentication processes, enterprise identity solutions significantly boost productivity within organisations. Employees can access the necessary tools and resources swiftly and seamlessly without the hassle of managing multiple passwords or undergoing complex authentication procedures. This efficiency not only saves time but also minimises user frustration, allowing employees to focus on their core tasks and responsibilities. As a result, streamlined authentication processes contribute to a more productive work environment where employees can work more effectively and collaboratively towards achieving business objectives.
Ensures compliance with data protection regulations and industry standards
Ensuring compliance with data protection regulations and industry standards is a critical benefit of implementing an enterprise identity framework. By accurately managing user identities and permissions, businesses can demonstrate adherence to laws such as GDPR, HIPAA, and PCI DSS. This proactive approach not only helps in avoiding costly fines and penalties but also enhances trust with customers and partners by showcasing a commitment to protecting sensitive information. Compliance through effective enterprise identity management is essential for maintaining a strong reputation and mitigating legal risks in today’s data-driven business landscape.
Facilitates secure collaboration with external partners through identity federation
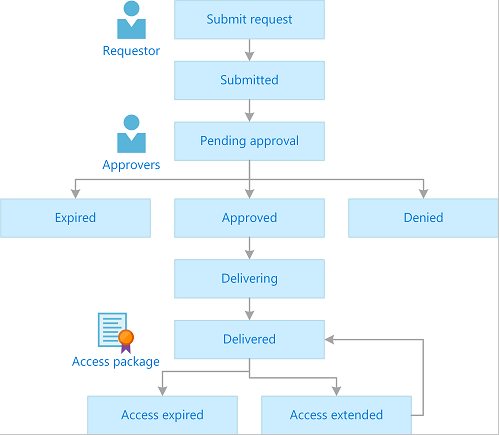
Enterprise identity solutions offer a significant advantage by enabling secure collaboration with external partners through identity federation. By extending identity management beyond organisational boundaries, businesses can establish trusted relationships with external entities while maintaining control over access rights and permissions. This facilitates seamless information sharing and collaboration, enhancing productivity and efficiency in joint projects or business endeavours. Identity federation ensures that data exchange remains secure and compliant with regulatory requirements, fostering a culture of trust and cooperation among partners.
Centralises identity management for easier administration and control
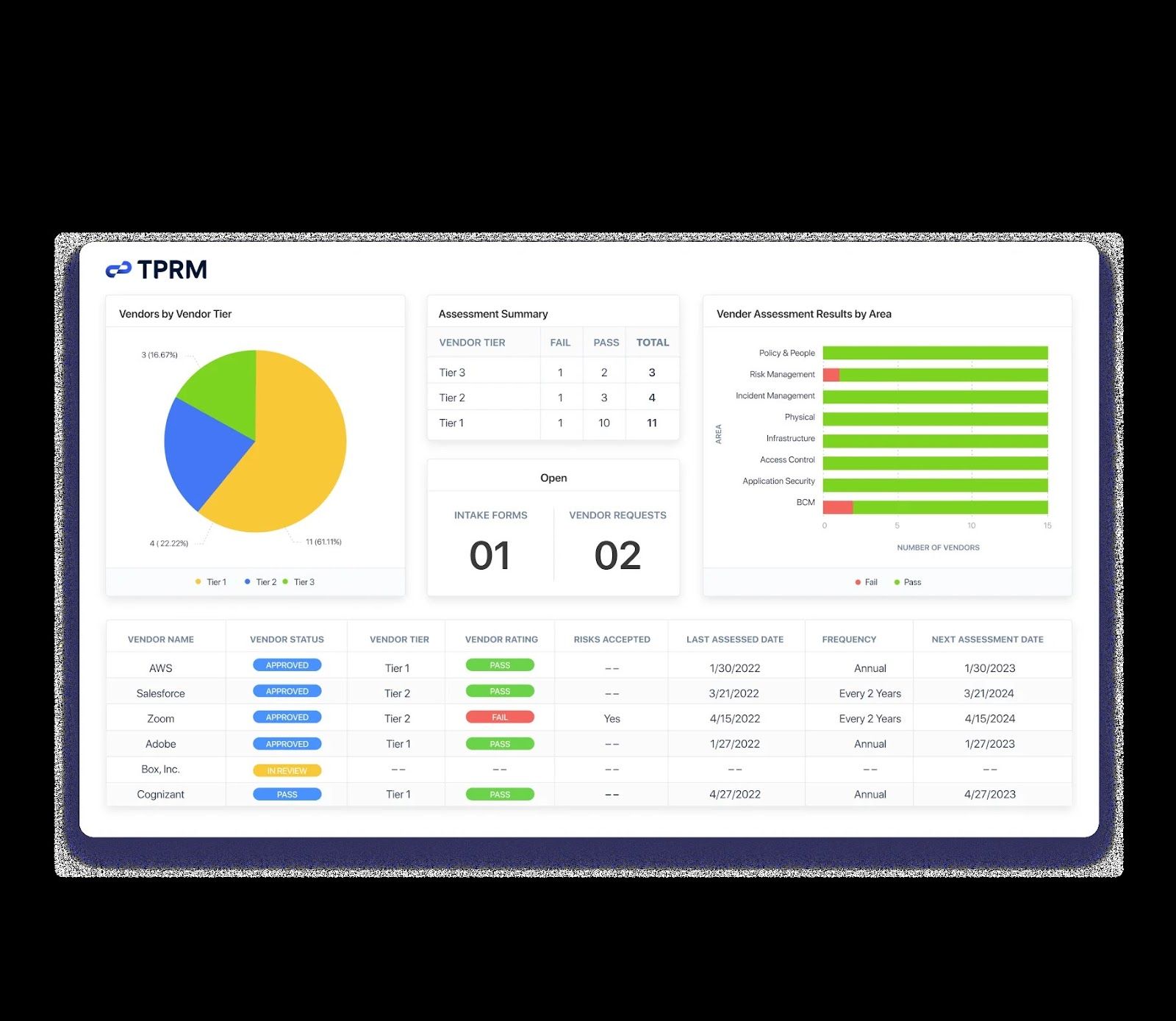
Centralising identity management within an enterprise offers a significant advantage by simplifying administration and enhancing control over user identities and access. By consolidating user accounts, permissions, and authentication processes into a centralised system, organisations can streamline the management of identities across various applications and systems. This approach not only reduces administrative overhead but also allows for more efficient monitoring of user activities and enforcement of security policies. Centralised identity management empowers administrators to quickly grant or revoke access rights, track user behaviour, and respond promptly to security incidents, ultimately strengthening overall security posture and operational effectiveness.
Supports business growth in the digital age by protecting sensitive information
In the digital age, enterprise identity plays a crucial role in supporting business growth by safeguarding sensitive information. By implementing robust identity management solutions, organisations can protect their valuable data from cyber threats and unauthorised access. This enhanced security not only instils trust among customers and partners but also ensures compliance with regulations, fostering a conducive environment for business expansion. With a strong enterprise identity framework in place, businesses can confidently pursue new opportunities, innovate with technology, and scale their operations while maintaining the integrity of their data assets.
Complexity
Implementing and managing an enterprise identity system can pose a significant challenge due to its inherent complexity. The intricacies involved in setting up and maintaining such a system demand dedicated resources and specialised expertise. From designing authentication protocols to configuring access controls and user permissions, every aspect of the enterprise identity framework requires meticulous attention to detail. Organisations may need to invest in training their staff or hiring external consultants to navigate the complexities of identity management effectively. The complexity of enterprise identity can lead to delays in implementation, increased operational costs, and potential vulnerabilities if not managed properly.
Cost
Setting up a robust enterprise identity management infrastructure can pose a significant challenge in terms of cost. The initial investment required for acquiring hardware, software, and training resources can be substantial. Organisations may need to allocate a considerable budget to implement and maintain a comprehensive identity management system effectively. These upfront costs can sometimes deter businesses, especially smaller ones, from prioritising the development of a secure identity framework. However, it is crucial for businesses to weigh the long-term benefits of enhanced security and efficiency against the immediate financial outlay when considering investing in enterprise identity solutions.
User Resistance
When implementing enterprise identity solutions, one significant con to consider is user resistance. Employees may exhibit reluctance towards adopting new authentication methods or access controls, which can result in potential productivity issues within the organisation. Resistance to change can stem from a variety of factors, including unfamiliarity with new technologies, concerns about increased complexity, or simply a preference for familiar routines. Overcoming user resistance requires effective communication, training, and support to help employees understand the benefits of enhanced security measures and how they contribute to overall business objectives. Failure to address user resistance adequately can hinder the successful implementation of enterprise identity solutions and impact operational efficiency.
Security Risks
Security Risks: Without proper configuration and maintenance, enterprise identity systems can pose significant security risks to organisations. Vulnerabilities in the system can be exploited by cybercriminals to gain unauthorised access to sensitive data, leading to potential data breaches and financial losses. It is essential for businesses to regularly update and monitor their enterprise identity systems to mitigate these risks and ensure the protection of valuable information against evolving cyber threats.
Integration Challenges
Integration Challenges: One significant drawback of enterprise identity management is the potential for integration challenges. When implementing identity management solutions within an organisation, compatibility issues with existing IT systems and applications may arise, leading to disruptions in workflow and operations. Ensuring seamless integration between disparate systems can be complex and time-consuming, requiring careful planning and coordination to minimise potential setbacks and maintain business continuity.