The Importance of GRC Audit Software in Modern Businesses
In today’s rapidly evolving business landscape, organisations face increasing regulatory requirements and cybersecurity threats. To effectively manage risks and ensure compliance with regulations, many businesses are turning to Governance, Risk, and Compliance (GRC) audit software.
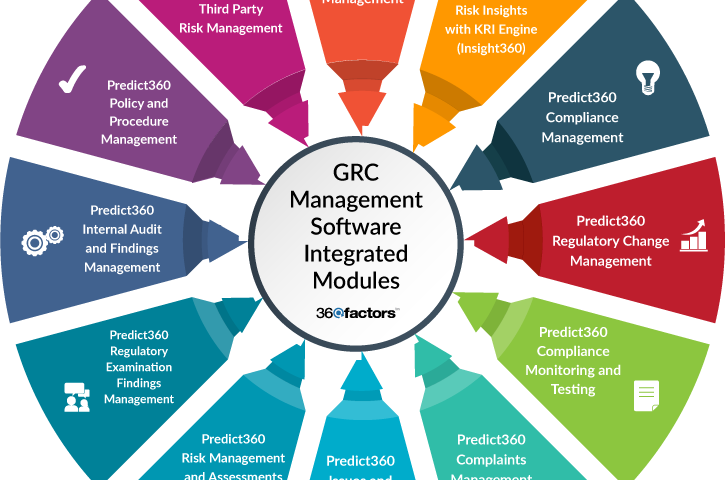
GRC audit software plays a crucial role in helping businesses streamline their audit processes, enhance transparency, and mitigate risks across various operational areas. Here are some key reasons why GRC audit software is essential for modern businesses:
Comprehensive Risk Management
Effective risk management is vital for safeguarding business operations and maintaining stakeholder trust. GRC audit software enables organisations to identify, assess, and prioritise risks across different functions within the company. By centralising risk data and providing real-time insights, businesses can proactively address potential threats and vulnerabilities.
Regulatory Compliance
Compliance with industry regulations and standards is a critical aspect of business operations. GRC audit software helps businesses stay up-to-date with changing regulatory requirements by automating compliance monitoring and reporting processes. This ensures that organisations avoid costly penalties and reputational damage due to non-compliance.
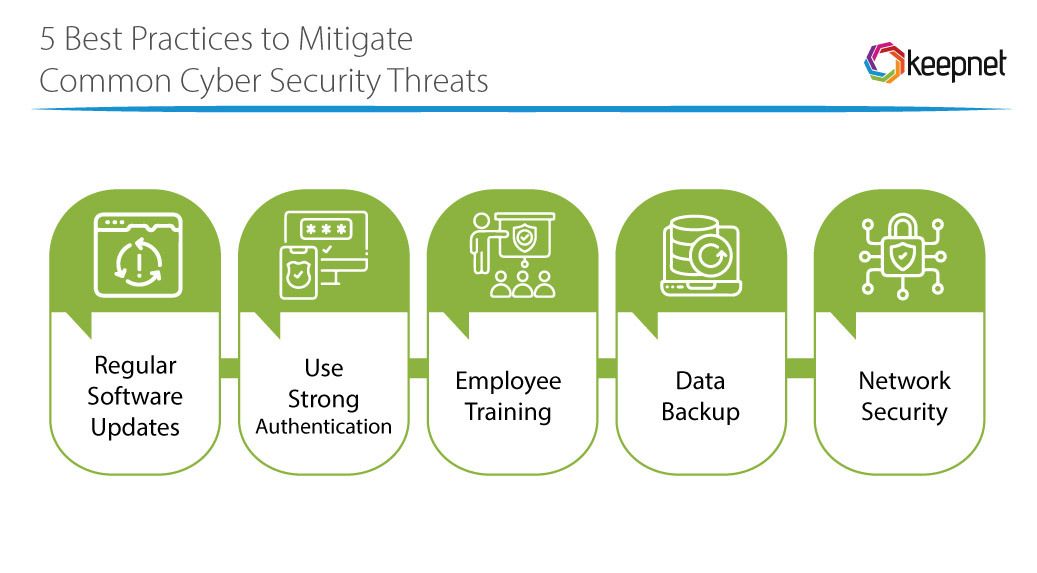
Enhanced Data Security
Protecting sensitive data from cyber threats is a top priority for modern businesses. GRC audit software offers robust security features that help organisations monitor access controls, detect suspicious activities, and prevent data breaches. By implementing stringent security measures through GRC software, businesses can strengthen their cybersecurity posture.
Improved Operational Efficiency
GRC audit software streamlines audit workflows and eliminates manual tasks associated with compliance management. By automating repetitive processes such as data collection, analysis, and reporting, businesses can improve operational efficiency and allocate resources more effectively towards strategic initiatives.
Strategic Decision-Making
Access to real-time data insights provided by GRC audit software empowers business leaders to make informed decisions that drive growth and innovation. By having a comprehensive view of risks, compliance status, and performance metrics, organisations can align their strategic objectives with risk mitigation efforts for sustainable business success.
In conclusion, GRC audit software has become an indispensable tool for modern businesses looking to navigate complex regulatory landscapes and mitigate emerging risks effectively. By investing in robust GRC solutions, organisations can proactively protect their assets, enhance operational resilience, and foster a culture of compliance across all levels of the company.
Understanding GRC Audit Software: Key Benefits, Features, and Suitability for Businesses
- What is GRC audit software?
- GRC audit software is a tool used by organisations to streamline governance, risk management, and compliance processes. It helps businesses manage risks, ensure regulatory compliance, and enhance transparency.
- How does GRC audit software benefit businesses?
- What features should I look for in GRC audit software?
- Is GRC audit software suitable for small businesses?
- How does GRC audit software help with regulatory compliance?
- providing alerts on non-compliance issues,
generating reports for audits,
and centralising documentation needed for demonstrating adherence to regulations.
What is GRC audit software?
GRC audit software, short for Governance, Risk, and Compliance audit software, is a specialised tool designed to help businesses manage their governance, risk management, and compliance processes effectively. This software enables organisations to centralise and automate various aspects of auditing, including risk assessment, regulatory compliance monitoring, and internal control evaluations. By providing real-time insights into key risk areas and compliance status, GRC audit software empowers businesses to enhance transparency, streamline audit workflows, and proactively address potential threats. Overall, GRC audit software plays a crucial role in enabling businesses to navigate complex regulatory environments, mitigate risks, and strengthen their overall governance framework.
GRC audit software is a tool used by organisations to streamline governance, risk management, and compliance processes. It helps businesses manage risks, ensure regulatory compliance, and enhance transparency.
GRC audit software is a valuable tool utilised by organisations to streamline governance, risk management, and compliance processes effectively. By leveraging this software, businesses can efficiently manage risks, uphold regulatory compliance standards, and improve transparency within their operations. This comprehensive solution plays a critical role in empowering businesses to proactively identify and address potential risks while maintaining adherence to industry regulations, ultimately fostering a culture of accountability and operational excellence.
How does GRC audit software benefit businesses?
GRC audit software offers a multitude of benefits to businesses by streamlining audit processes, enhancing risk management capabilities, ensuring regulatory compliance, and improving overall operational efficiency. By centralising risk data and providing real-time insights, GRC audit software enables businesses to proactively identify and address risks across various operational areas. Moreover, the automation of compliance monitoring and reporting processes helps organisations stay up-to-date with regulatory requirements, avoiding potential penalties and reputational damage. Additionally, the enhanced data security features of GRC audit software help protect sensitive information from cyber threats, while also improving decision-making through access to real-time data insights. Ultimately, GRC audit software plays a crucial role in helping businesses navigate complex regulatory landscapes, mitigate risks effectively, and drive sustainable growth.
What features should I look for in GRC audit software?
When evaluating GRC audit software, it is essential to consider several key features that can enhance your organisation’s risk management and compliance efforts. Look for software that offers comprehensive risk assessment capabilities, robust compliance monitoring tools, advanced data security features, streamlined audit workflows for improved efficiency, and real-time reporting functionalities to support strategic decision-making. Additionally, seek out GRC audit software with customisable dashboards and alerts to ensure timely identification of potential risks and non-compliance issues. By prioritising these features in your selection process, you can choose a GRC audit software solution that aligns with your business objectives and enhances your overall governance, risk management, and compliance practices.
Is GRC audit software suitable for small businesses?
When considering whether GRC audit software is suitable for small businesses, it’s important to recognise that the benefits of such software extend beyond the size of the organisation. While larger enterprises often have more complex regulatory requirements and risk management needs, small businesses can also benefit from GRC audit software in various ways. Implementing GRC audit software can help small businesses enhance their risk management practices, ensure compliance with relevant regulations, improve data security measures, streamline operational processes, and make informed strategic decisions. By investing in GRC audit software tailored to their specific needs and scale, small businesses can effectively manage risks, protect their assets, and foster a culture of governance and compliance essential for sustainable growth.
How does GRC audit software help with regulatory compliance?
GRC audit software plays a vital role in assisting organisations with regulatory compliance by automating and streamlining the complex processes involved. By centralising data and providing real-time insights, GRC audit software enables businesses to monitor and track their compliance status with various regulations and standards. This software helps in identifying potential gaps or non-compliance issues, allowing organisations to take corrective actions promptly. Additionally, GRC audit software simplifies reporting requirements, making it easier for businesses to generate comprehensive compliance reports for internal stakeholders and regulatory authorities. Overall, GRC audit software enhances transparency, efficiency, and accuracy in managing regulatory compliance efforts within modern businesses.
providing alerts on non-compliance issues,
generating reports for audits,
and centralising documentation needed for demonstrating adherence to regulations.
One frequently asked question regarding GRC audit software revolves around its capabilities in providing alerts on non-compliance issues, generating reports for audits, and centralising documentation needed for demonstrating adherence to regulations. Businesses often seek clarity on how GRC audit software can efficiently monitor their operations, promptly notify them of any regulatory violations or risks, streamline the audit process by automating report generation, and maintain a central repository for all necessary documentation to showcase compliance with industry regulations. This comprehensive functionality not only ensures proactive risk management but also facilitates seamless regulatory compliance across various aspects of business operations.