Understanding Statutory Compliance Software: A Comprehensive Guide
In today’s rapidly evolving business landscape, maintaining statutory compliance is more crucial than ever. Organisations must adhere to a myriad of laws and regulations, which can be both time-consuming and complex. This is where statutory compliance software comes into play, offering businesses an efficient way to manage their compliance obligations.
What is Statutory Compliance Software?
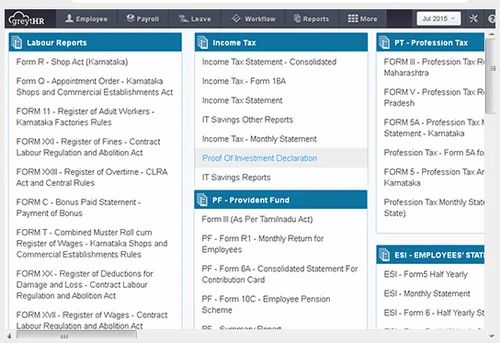
Statutory compliance software is a specialised tool designed to help businesses ensure that they meet all legal and regulatory requirements relevant to their industry. This type of software automates the tracking, reporting, and management of compliance tasks, reducing the risk of non-compliance and its associated penalties.
The Importance of Statutory Compliance
Non-compliance with statutory regulations can lead to severe consequences, including financial penalties, legal action, and reputational damage. For this reason, it is vital for organisations to stay up-to-date with the latest regulatory changes and ensure they are fully compliant at all times. Statutory compliance software simplifies this process by providing real-time updates and reminders about upcoming deadlines.
Key Features of Statutory Compliance Software
- Automated Alerts: Receive notifications about important dates and changes in legislation to ensure timely compliance.
- Comprehensive Reporting: Generate detailed reports that provide insights into your organisation’s compliance status.
- Document Management: Store and organise all necessary documents in a centralised location for easy access and retrieval.
- User-Friendly Interface: Navigate the software with ease thanks to intuitive design features.
- Integration Capabilities: Seamlessly integrate with existing systems for streamlined operations.
The Benefits of Using Statutory Compliance Software
The primary benefit of statutory compliance software is the reduction in administrative burden on businesses. By automating routine tasks such as tracking deadlines and generating reports, organisations can focus more on strategic activities rather than getting bogged down by paperwork. Additionally, such software enhances accuracy by minimising human error in compliance processes.
An added advantage is improved transparency within the organisation. With all compliance-related information stored in one place, stakeholders can easily access data when needed. This transparency fosters trust among employees, investors, and regulators alike.
Selecting the Right Software
Choosing the right statutory compliance software depends on several factors including your industry requirements, company size, budget constraints, and specific needs. It’s essential to evaluate different options based on these criteria before making a decision. Look for solutions that offer scalability so they can grow alongside your business while providing robust support services for any issues that may arise during implementation or use.
The Future of Statutory Compliance Software
The demand for statutory compliance software is expected to increase as regulatory environments become more complex globally. Advancements in technology such as artificial intelligence (AI) are likely to further enhance these tools’ capabilities by offering predictive analytics that anticipate potential risks before they occur.
In conclusion, investing in statutory compliance software not only helps mitigate risks associated with non-compliance but also streamlines operations through automation—ultimately contributing towards organisational success in an increasingly regulated world.
Enhancing Organisational Efficiency and Risk Management: The Benefits of Statutory Compliance Software
- Automates compliance tracking, reducing manual effort and human error.
- Provides real-time updates on regulatory changes to ensure timely adherence.
- Generates comprehensive reports for quick insights into compliance status.
- Centralises document management for easy access and retrieval of necessary files.
- Enhances transparency within the organisation by storing all compliance-related data in one place.
- Improves accuracy in compliance processes through automation and data validation features.
- Saves time and resources by streamlining compliance tasks and workflows.
- Helps mitigate risks associated with non-compliance, avoiding financial penalties and legal consequences.
- Increases operational efficiency by freeing up staff to focus on strategic initiatives rather than administrative tasks.
Challenges of Statutory Compliance Software: Cost, Complexity, and Integration Hurdles
Automates compliance tracking, reducing manual effort and human error.
One significant advantage of statutory compliance software is its ability to automate compliance tracking, effectively reducing the need for manual effort and minimising the risk of human error. By streamlining the process of monitoring regulatory requirements and deadlines, this feature ensures that organisations can maintain a high level of accuracy and efficiency in their compliance efforts. Automated tracking not only saves time and resources but also enhances the reliability of compliance data, ultimately contributing to a more robust and proactive approach to meeting statutory obligations.
Provides real-time updates on regulatory changes to ensure timely adherence.
One of the key benefits of statutory compliance software is its ability to provide real-time updates on regulatory changes, enabling organisations to stay informed and act promptly to ensure timely adherence. By receiving instant notifications about any modifications in laws or regulations relevant to their industry, businesses can proactively adjust their compliance strategies and processes. This feature not only helps mitigate the risk of non-compliance but also allows companies to maintain a proactive stance in meeting their legal obligations, ultimately promoting a culture of continuous compliance and risk management within the organisation.
Generates comprehensive reports for quick insights into compliance status.
One significant advantage of statutory compliance software is its ability to generate comprehensive reports that provide quick insights into an organisation’s compliance status. These reports offer a snapshot of the company’s adherence to various regulations and highlight areas that may require attention. By consolidating relevant data and presenting it in an easily digestible format, businesses can promptly identify any gaps in compliance and take proactive measures to address them. This feature not only saves time but also enables informed decision-making based on real-time information, ultimately enhancing overall compliance effectiveness.
Centralises document management for easy access and retrieval of necessary files.
One key advantage of statutory compliance software is its ability to centralise document management, facilitating easy access and retrieval of necessary files. By storing all compliance-related documents in a single, organised location, businesses can streamline their operations and ensure that essential files are readily available when needed. This feature not only enhances efficiency but also promotes transparency within the organisation, as stakeholders can quickly retrieve relevant documents for audits, reporting, or regulatory purposes. Centralised document management simplifies the compliance process, reducing the risk of errors and ensuring that businesses can demonstrate their adherence to statutory regulations effectively.
Enhances transparency within the organisation by storing all compliance-related data in one place.
Statutory compliance software offers the significant advantage of enhancing transparency within the organisation by centralising all compliance-related data in one accessible location. This consolidated approach ensures that stakeholders have easy access to vital information, promoting a culture of openness and accountability. By having a single source of truth for compliance data, organisations can foster trust among employees, investors, and regulators, demonstrating a commitment to upholding legal and regulatory standards. The transparency facilitated by statutory compliance software not only improves internal communication but also strengthens external relationships by providing clear and reliable information on compliance efforts.
Improves accuracy in compliance processes through automation and data validation features.
Statutory compliance software offers a significant advantage by enhancing accuracy in compliance processes through automation and data validation features. By automating routine tasks and cross-referencing data against regulatory requirements, this software minimises the risk of errors that can occur with manual entry. Through automated checks and validations, organisations can ensure that their compliance efforts are consistently aligned with the latest regulations, reducing the likelihood of costly mistakes and non-compliance issues. This improved accuracy not only saves time but also instils confidence in stakeholders that regulatory obligations are being met effectively and efficiently.
Saves time and resources by streamlining compliance tasks and workflows.
Statutory compliance software offers a significant advantage by saving time and resources through the streamlining of compliance tasks and workflows. By automating repetitive processes, such as tracking deadlines and generating reports, organisations can allocate their resources more efficiently towards strategic initiatives. This efficiency not only reduces the burden of manual work but also enhances overall productivity, allowing businesses to focus on core operations while ensuring adherence to regulatory requirements seamlessly.
Helps mitigate risks associated with non-compliance, avoiding financial penalties and legal consequences.
Statutory compliance software plays a crucial role in mitigating risks linked to non-compliance by providing businesses with a proactive approach to meeting legal and regulatory requirements. By utilising this software, organisations can stay informed about key deadlines, changes in legislation, and necessary actions to ensure adherence to laws. This proactive stance helps prevent potential financial penalties and legal consequences that may arise from failing to comply with statutory regulations. Ultimately, statutory compliance software acts as a safeguard against costly repercussions, allowing businesses to operate with confidence within the boundaries of the law.
Increases operational efficiency by freeing up staff to focus on strategic initiatives rather than administrative tasks.
Statutory compliance software offers a significant advantage by enhancing operational efficiency within organisations. By automating time-consuming administrative tasks related to compliance management, staff members are liberated to concentrate on strategic initiatives that drive business growth and innovation. This shift in focus allows employees to channel their expertise and creativity towards value-adding projects, ultimately boosting productivity and fostering a more agile and competitive business environment.
Cost
One significant drawback of statutory compliance software is the cost associated with its implementation and maintenance. This expense can pose a considerable challenge, particularly for small businesses operating on limited budgets. The initial investment required to set up the software and the ongoing costs for updates and support services may strain financial resources that could be allocated to other critical areas of the business. As a result, some small businesses may find it difficult to justify the expenditure on statutory compliance software, despite its potential benefits in ensuring regulatory adherence.
Complexity
One significant drawback of statutory compliance software is its complexity. Certain solutions in this category may present a steep learning curve, demanding extensive training for users to unlock and maximise all available features. Navigating through intricate functionalities and understanding the software’s nuances can be time-consuming and resource-intensive. This complexity may hinder the seamless adoption of the software within an organisation, leading to delays in implementation and potential inefficiencies in compliance management processes. Businesses must carefully consider the level of training and support required before investing in statutory compliance software to ensure a smooth transition and optimal utilisation of the tool’s capabilities.
Integration Challenges
One significant drawback of statutory compliance software is the integration challenges it presents. Connecting this specialised software with existing systems within an organisation can prove to be a complex and time-consuming task. The process of integration may disrupt workflow processes, leading to potential inefficiencies and delays in operations. Ensuring seamless compatibility between statutory compliance software and other systems requires careful planning, resources, and expertise to overcome these integration challenges effectively.