The Benefits of Using a Bulk Backlink Checker for Free
Backlinks are crucial for improving a website’s search engine ranking and visibility. Monitoring backlinks is essential to ensure the quality and relevance of inbound links. However, checking backlinks manually can be time-consuming and inefficient, especially for websites with a large number of links.
That’s where a bulk backlink checker comes in handy. A bulk backlink checker allows you to analyse multiple backlinks simultaneously, saving you time and effort. What’s even better is when you can access this tool for free.
Benefits of Using a Bulk Backlink Checker:
- Efficiency: With a bulk backlink checker, you can quickly assess the quality of your backlinks in one go, rather than checking them individually.
- Time-saving: Checking backlinks in bulk saves you valuable time that can be allocated to other important tasks related to your website’s SEO.
- Insightful Analysis: A bulk backlink checker provides detailed insights into your backlink profile, helping you identify spammy or low-quality links that could harm your site’s reputation.
- Enhanced SEO Strategy: By regularly monitoring your backlinks with a bulk checker, you can make informed decisions about link building strategies and improve your overall SEO performance.
- Cost-effective: Opting for a free bulk backlink checker allows you to enjoy the benefits of automated link analysis without any additional cost.
In conclusion, using a bulk backlink checker for free offers numerous advantages for website owners looking to enhance their SEO efforts. By leveraging this tool, you can streamline the process of monitoring backlinks and make data-driven decisions to boost your website’s search engine ranking effectively.
Understanding the Advantages of Using a Free Bulk Backlink Checker: Frequently Asked Questions
- 1. How does a bulk backlink checker help in analysing multiple backlinks at once?
- 2. What are the time-saving benefits of using a bulk backlink checker for free?
- 3. Can a bulk backlink checker provide insightful analysis of backlink profiles?
- 4. How does using a bulk backlink checker enhance one’s SEO strategy?
- 5. Are there any costs associated with using a free bulk backlink checker?
- 6. What type of information can be obtained from a bulk backlink checker report?
- 7. How can website owners benefit from regularly monitoring their backlinks with a bulk checker?
1. How does a bulk backlink checker help in analysing multiple backlinks at once?
A bulk backlink checker simplifies the process of analysing multiple backlinks simultaneously by allowing users to input a list of URLs or domains and then automatically scanning and evaluating each link’s quality, relevance, and authority. This tool streamlines the time-consuming task of individually checking each backlink by providing a comprehensive overview in a single report. Users can quickly identify patterns, trends, and potential issues within their backlink profile, enabling them to make informed decisions about their SEO strategy and take necessary actions to improve their website’s search engine ranking.
2. What are the time-saving benefits of using a bulk backlink checker for free?
When utilising a bulk backlink checker for free, one can reap significant time-saving benefits. By analysing multiple backlinks simultaneously, this tool streamlines the process of assessing the quality and relevance of inbound links. Rather than tediously checking each link individually, a bulk backlink checker allows users to efficiently evaluate their backlink profile in one go. This time-saving advantage enables website owners to dedicate more time to other essential SEO tasks, ultimately enhancing their overall digital marketing strategies.
3. Can a bulk backlink checker provide insightful analysis of backlink profiles?
When considering the use of a bulk backlink checker for free, a common query that arises is whether such a tool can offer insightful analysis of backlink profiles. The answer is affirmative. A reliable bulk backlink checker has the capability to provide in-depth and valuable insights into backlink profiles. By analysing multiple backlinks simultaneously, this tool can help users identify the quality, relevance, and authority of inbound links, enabling them to make informed decisions about their SEO strategies. With detailed analytics and reports generated by a bulk backlink checker, website owners can gain a comprehensive understanding of their backlink profiles and take necessary actions to improve their site’s search engine performance.
4. How does using a bulk backlink checker enhance one’s SEO strategy?
Using a bulk backlink checker can significantly enhance one’s SEO strategy by providing valuable insights into the quality and quantity of backlinks pointing to a website. By analysing backlinks in bulk, website owners can identify patterns, trends, and potential issues within their link profile. This information enables them to make informed decisions about link building strategies, disavowing harmful links, and improving the overall authority of their website. With a comprehensive overview of their backlink profile, users can refine their SEO efforts, increase organic traffic, and ultimately boost their search engine rankings.
5. Are there any costs associated with using a free bulk backlink checker?
When it comes to using a free bulk backlink checker, one common question that arises is whether there are any costs involved. The beauty of a free bulk backlink checker is that it allows users to access valuable insights into their backlink profiles without incurring any expenses. Unlike paid tools, a free bulk backlink checker eliminates the financial barrier, enabling website owners to efficiently monitor and analyse their backlinks at no cost. This accessibility to essential SEO data without the burden of fees makes utilising a free bulk backlink checker an attractive and cost-effective option for enhancing website performance and search engine optimisation strategies.
6. What type of information can be obtained from a bulk backlink checker report?
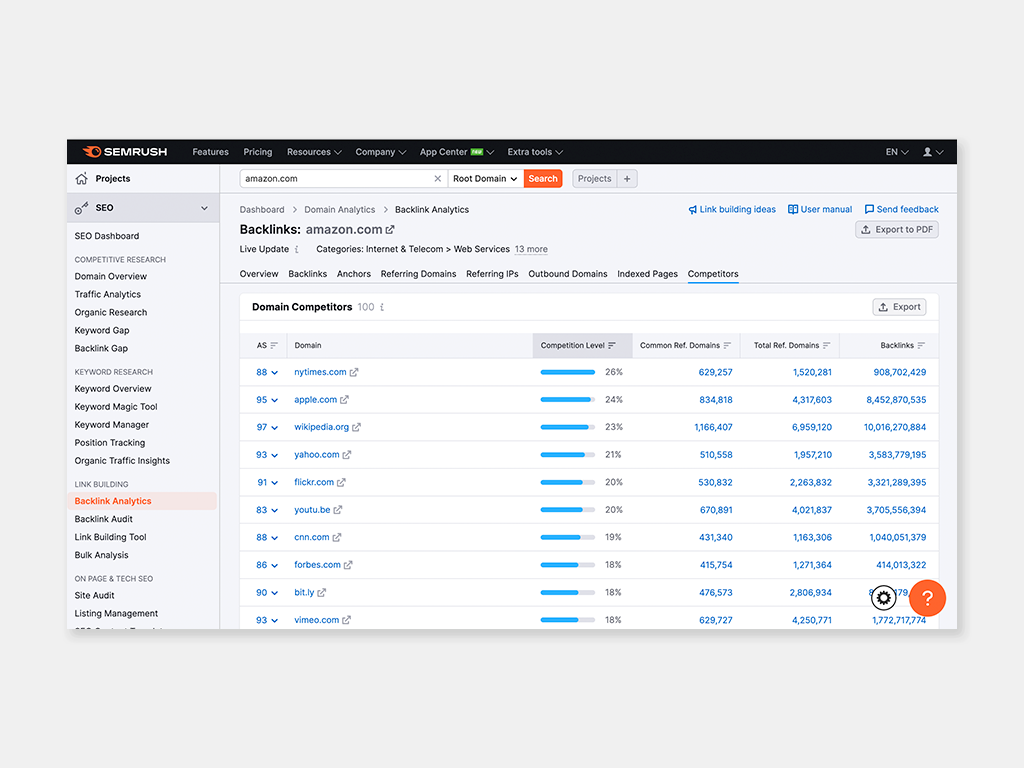
A bulk backlink checker report provides valuable insights into the backlink profile of a website. This type of report typically includes information such as the total number of backlinks, the domain authority of linking websites, anchor text used in the backlinks, the status of each link (e.g., active or broken), and the quality score of backlinks based on various metrics. Additionally, a bulk backlink checker report may highlight any toxic or spammy links that could potentially harm the website’s SEO performance. By analysing this comprehensive data, website owners can make informed decisions about their link building strategies and take necessary actions to improve their site’s search engine ranking and credibility.
7. How can website owners benefit from regularly monitoring their backlinks with a bulk checker?
Website owners can benefit significantly from regularly monitoring their backlinks with a bulk checker. By using this tool, website owners can gain valuable insights into the quality and relevance of their backlink profile. Regular monitoring helps in identifying any spammy or low-quality links that could potentially harm the website’s SEO performance. Additionally, by analysing backlinks in bulk, website owners can make informed decisions about their link building strategies, improve their overall SEO efforts, and enhance their website’s search engine ranking effectively.