The Importance of Supply Chain Compliance Software in Today’s Business Landscape
In the fast-paced and interconnected world of business, supply chains play a crucial role in ensuring the seamless flow of goods and services. However, with this complexity comes the need for robust compliance measures to mitigate risks and ensure ethical practices throughout the supply chain. This is where supply chain compliance software steps in as a vital tool for modern businesses.
What is Supply Chain Compliance Software?
Supply chain compliance software is a specialised solution designed to help companies monitor, manage, and enforce regulatory requirements and ethical standards within their supply chains. This software provides visibility into various aspects of the supply chain, including supplier performance, product quality, labour practices, environmental impact, and more.
The Benefits of Supply Chain Compliance Software
Implementing supply chain compliance software offers numerous benefits to businesses looking to enhance their operations:
- Risk Mitigation: By identifying potential compliance issues early on, companies can proactively address them before they escalate into larger problems.
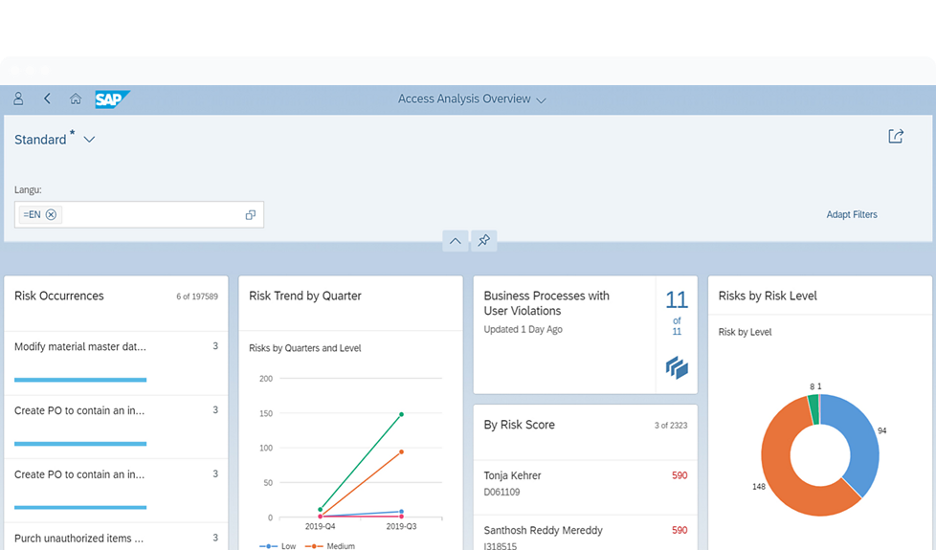
- Improved Transparency: With real-time data tracking and reporting capabilities, businesses can increase transparency across their supply chains and build trust with stakeholders.
- Enhanced Efficiency: Automation features streamline compliance processes, reducing manual errors and saving time for employees.
- Cost Savings: By identifying inefficiencies and non-compliant practices, businesses can optimise their operations and reduce financial risks associated with non-compliance.
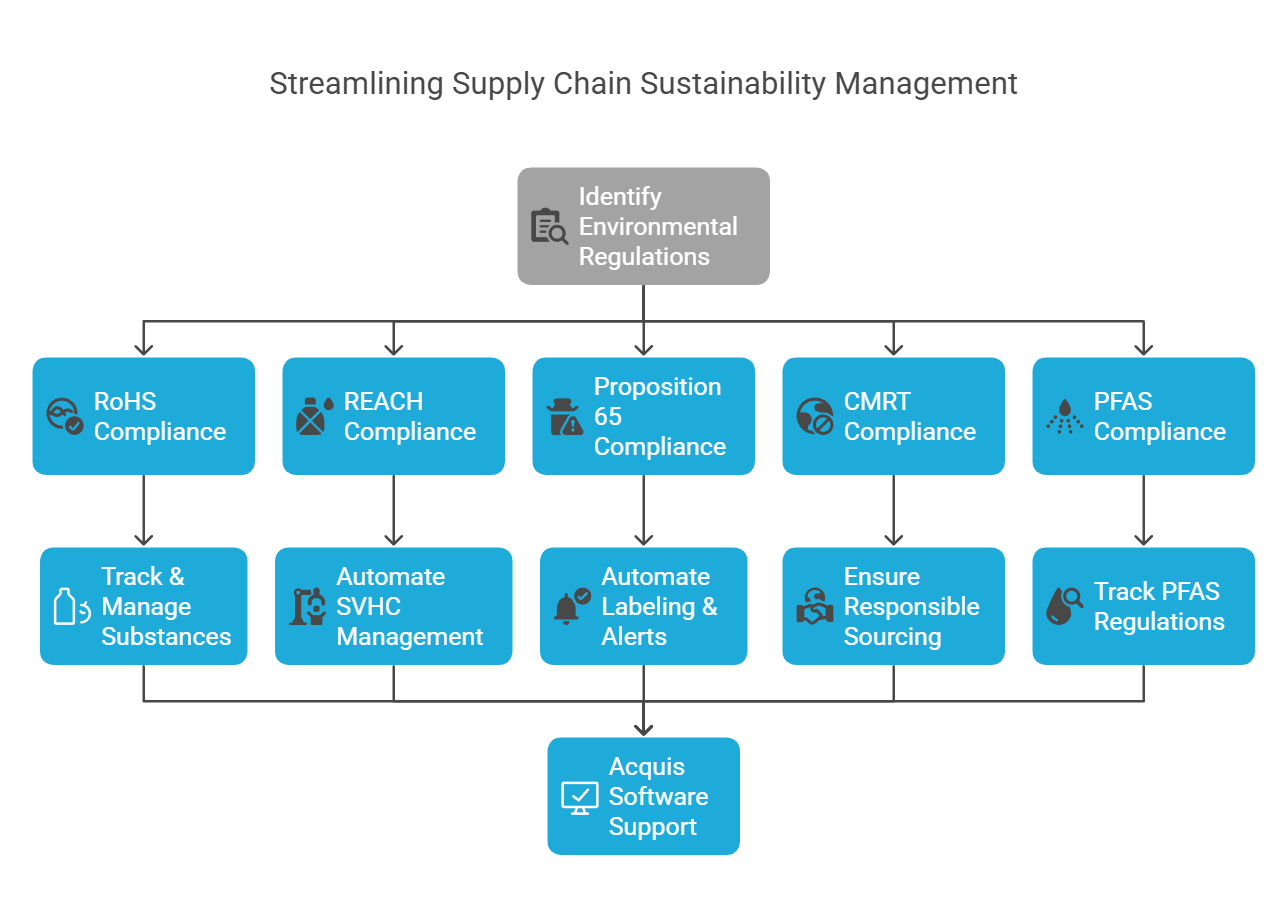
The Role of Supply Chain Compliance Software in Sustainability
In today’s environmentally conscious world, sustainability has become a key focus for many businesses. Supply chain compliance software plays a critical role in helping companies achieve their sustainability goals by monitoring environmental impacts across the entire supply chain. From carbon emissions to waste management practices, this software enables companies to track their environmental footprint and make informed decisions to reduce it.
Conclusion
As global supply chains continue to grow in complexity, the importance of supply chain compliance software cannot be overstated. By investing in robust compliance solutions, businesses can not only meet regulatory requirements but also enhance transparency, efficiency, and sustainability throughout their supply chains. In an ever-evolving business landscape where reputation and ethical practices are paramount, supply chain compliance software emerges as a valuable asset for forward-thinking organisations.
Advantages of Supply Chain Compliance Software: Enhancing Transparency, Reducing Risks, and Supporting Sustainability
- Enhances transparency across the supply chain
- Reduces risks associated with non-compliance
- Improves operational efficiency through automation
- Helps in identifying and addressing compliance issues proactively
- Facilitates real-time monitoring of supplier performance
- Supports sustainability initiatives by tracking environmental impacts
Seven Challenges of Supply Chain Compliance Software: Costs, Complexity, and More
- Initial Implementation Costs
- Complexity
- Integration Challenges
- Data Security Risks
- Scalability Issues
- User Adoption Hurdles
- Maintenance Requirements
Enhances transparency across the supply chain
One significant advantage of supply chain compliance software is its ability to enhance transparency across the entire supply chain. By providing real-time data tracking and reporting capabilities, this software enables businesses to gain a comprehensive view of their suppliers, processes, and practices. This increased transparency not only fosters trust with stakeholders but also allows companies to identify potential compliance issues proactively. Ultimately, by promoting transparency, supply chain compliance software helps organisations build stronger relationships with suppliers, improve operational efficiency, and uphold ethical standards throughout their supply chains.
Reduces risks associated with non-compliance
One of the key advantages of supply chain compliance software is its ability to reduce risks associated with non-compliance. By implementing robust compliance measures and monitoring tools, businesses can proactively identify and address potential compliance issues before they escalate into significant problems. This proactive approach not only helps organisations avoid costly penalties and legal implications but also safeguards their reputation and relationships with stakeholders. Supply chain compliance software provides the necessary visibility and control to mitigate risks effectively, ensuring that companies operate ethically and in accordance with regulatory standards.
Improves operational efficiency through automation
One significant advantage of supply chain compliance software is its ability to enhance operational efficiency through automation. By automating repetitive tasks and processes related to compliance monitoring and reporting, businesses can streamline their operations and reduce the time and resources spent on manual efforts. This not only increases productivity but also minimises the risk of human errors, ensuring that compliance activities are conducted accurately and efficiently. Ultimately, the automation capabilities of supply chain compliance software enable companies to focus on strategic initiatives and decision-making, driving overall operational excellence within their supply chains.
Helps in identifying and addressing compliance issues proactively
One key advantage of supply chain compliance software is its ability to help businesses identify and address compliance issues proactively. By leveraging real-time monitoring and data analysis capabilities, this software enables companies to detect potential non-compliance risks at an early stage. This proactive approach allows organisations to take timely corrective actions, thereby reducing the likelihood of regulatory violations and associated penalties. Ultimately, by staying ahead of compliance issues, businesses can maintain a strong reputation, build trust with stakeholders, and safeguard their operations from potential disruptions.
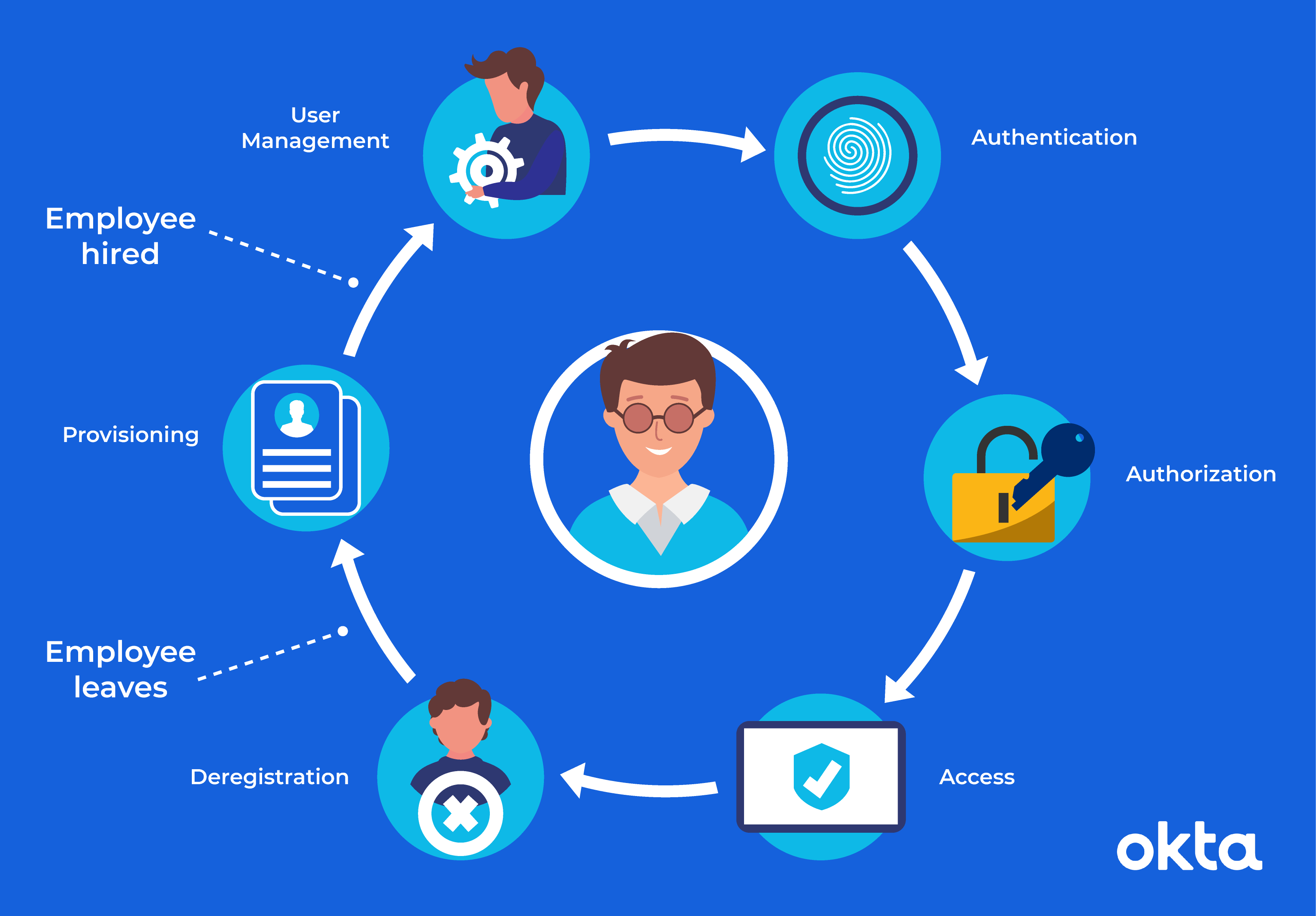
Facilitates real-time monitoring of supplier performance
Supply chain compliance software offers the valuable advantage of enabling real-time monitoring of supplier performance. This capability allows businesses to proactively track and evaluate their suppliers’ activities, ensuring that they meet quality standards, delivery timelines, and compliance requirements. By having instant access to supplier performance data, companies can identify issues promptly, address them efficiently, and maintain a high level of operational efficiency within their supply chains. This proactive approach not only improves overall supply chain management but also strengthens relationships with suppliers, ultimately leading to enhanced business outcomes.
Supports sustainability initiatives by tracking environmental impacts
Supply chain compliance software plays a pivotal role in supporting sustainability initiatives by meticulously tracking environmental impacts throughout the supply chain. By monitoring factors such as carbon emissions, waste management practices, and energy consumption, businesses can gain valuable insights into their environmental footprint. This data empowers companies to make informed decisions that reduce their impact on the environment, driving towards a more sustainable and eco-friendly supply chain. Ultimately, the ability of supply chain compliance software to track and manage environmental impacts not only benefits the planet but also enhances the reputation and credibility of businesses committed to sustainable practices.
Initial Implementation Costs
One notable drawback of supply chain compliance software is the initial implementation costs associated with its setup. Businesses considering the adoption of such software may face substantial upfront expenses for licensing, training, and customisation. These costs can pose a financial challenge, especially for smaller companies with limited budgets. The investment required for the implementation of supply chain compliance software may deter some organisations from taking advantage of its benefits, despite the long-term advantages it offers in terms of risk mitigation and operational efficiency.
Complexity
One significant drawback of supply chain compliance software is its inherent complexity, which can pose challenges for businesses. The intricate nature of these systems often demands specialised knowledge and dedicated resources to effectively utilise and maintain them. Companies may need to invest in training or hire personnel with expertise in the software to ensure its optimal functionality. This added layer of complexity can potentially increase operational costs and create barriers for smaller organisations with limited resources looking to implement such solutions.
Integration Challenges
One significant drawback of supply chain compliance software is the integration challenges it presents. Incorporating this software into existing systems and processes can be a time-consuming endeavour that poses the risk of operational disruptions. The complexity of aligning different technologies and data sources may result in delays and require substantial effort to ensure seamless integration. Moreover, any disruptions during the integration phase could impact the day-to-day operations of a business, potentially causing inefficiencies and affecting overall productivity.
Data Security Risks
Data Security Risks: One significant drawback of supply chain compliance software is the inherent data security risks associated with storing sensitive supply chain information in a centralised system. Without adequate cybersecurity measures in place, such as encryption protocols, access controls, and regular security audits, companies are vulnerable to data breaches and cyberattacks that could compromise the confidentiality and integrity of their critical business data. The potential consequences of inadequate data security measures highlight the importance of prioritising robust cybersecurity practices when implementing supply chain compliance software to safeguard against potential threats and protect sensitive information from falling into the wrong hands.
Scalability Issues
Scalability issues pose a significant con for some supply chain compliance software solutions. As businesses expand or evolve, the software may struggle to keep up with the increased demands, resulting in limitations in functionality. This can hinder the software’s ability to adapt to changing business needs and may ultimately impede the company’s efforts to maintain compliance across a growing and complex supply chain. Businesses must carefully assess the scalability capabilities of supply chain compliance software to ensure that it can effectively grow alongside their operations and continue to meet their evolving compliance requirements.
User Adoption Hurdles
One significant con of supply chain compliance software is the user adoption hurdles that employees may encounter. The introduction of new software can lead to resistance or challenges among staff members, who may struggle to adapt to unfamiliar interfaces or processes. This resistance can hinder the efficient implementation of compliance measures and reduce the overall effectiveness of the software in monitoring and managing supply chain activities. Overcoming these user adoption hurdles requires adequate training, communication, and support to ensure that employees embrace the new technology and fully utilise its capabilities for improved compliance outcomes.
Maintenance Requirements
An inherent drawback of supply chain compliance software lies in its maintenance requirements. Continuous updates and ongoing maintenance are essential for the software to uphold its effectiveness and relevance. However, these necessary upkeep tasks contribute to the overall cost of ownership, potentially posing a financial burden on businesses seeking to implement and sustain compliance software within their supply chains. The need for regular maintenance can demand additional resources in terms of time, manpower, and financial investment, impacting the total cost of utilising supply chain compliance software in the long run.