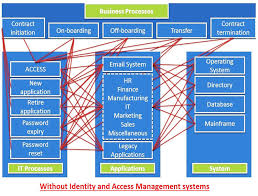
The Power of Oracle Cloud Identity and Access Management
Oracle Cloud Identity and Access Management (IAM) is a comprehensive solution that empowers organisations to secure their digital assets while enabling seamless access for authorised users. As businesses increasingly move towards cloud-based infrastructures, the need for robust identity and access management tools has become paramount.
Key Features of Oracle Cloud IAM:
- Single Sign-On (SSO): Oracle Cloud IAM offers SSO capabilities, allowing users to access multiple applications with a single set of credentials. This enhances user experience and simplifies access management.
- Multi-Factor Authentication (MFA): By supporting MFA, Oracle Cloud IAM adds an extra layer of security to user logins, reducing the risk of unauthorised access.
- User Lifecycle Management: Organisations can efficiently manage user identities throughout their lifecycle, from onboarding to offboarding, ensuring proper access control at all times.
- Role-Based Access Control (RBAC): With RBAC capabilities, administrators can assign roles to users based on their responsibilities, streamlining access permissions and reducing the risk of data breaches.
- Audit and Compliance: Oracle Cloud IAM provides robust auditing features that track user activities and changes to access permissions, helping organisations meet compliance requirements.
The Benefits of Oracle Cloud IAM:
Implementing Oracle Cloud IAM offers several benefits to organisations:
- Enhanced Security: By centralising identity management and enforcing strong authentication mechanisms, Oracle Cloud IAM strengthens security posture and mitigates risks.
- Improved Productivity: With streamlined access processes and automated user provisioning, employees can focus on their tasks without being hindered by complex login procedures.
- Cost Efficiency: Oracle Cloud IAM eliminates the need for costly on-premises infrastructure for identity management, reducing operational expenses for organisations.
- Simplified Compliance: The audit trails and reporting capabilities of Oracle Cloud IAM facilitate compliance with regulatory standards such as GDPR or HIPAA by providing visibility into user actions.
In Conclusion
In today’s digital landscape, protecting sensitive data and ensuring secure access are critical components of any organisation’s IT strategy. Oracle Cloud Identity and Access Management equips businesses with the tools they need to manage identities effectively, enforce access controls, and maintain compliance in a rapidly evolving environment. By leveraging the power of Oracle Cloud IAM, organisations can enhance their security posture while enabling seamless user experiences across cloud applications.
Understanding Oracle Cloud Identity and Access Management: Key Components and Roles Explained
- What is cloud identity and access management?
- Which 3 components are a part of OCI Identity and Access Management Service?
- What is Oracle Identity access management?
- What is the role of IAM in oracle cloud?
What is cloud identity and access management?
Cloud Identity and Access Management (IAM) in the context of Oracle Cloud refers to a set of tools and processes designed to securely manage user identities and control access to cloud resources. It encompasses authentication, authorisation, and user provisioning, ensuring that only authorised individuals can access specific applications or data within the cloud environment. Cloud IAM solutions like Oracle’s provide organisations with the means to centralise identity management, enforce security policies, and streamline access control across their cloud infrastructure. By implementing cloud IAM, businesses can enhance data security, improve operational efficiency, and meet compliance requirements in an increasingly digital and interconnected world.
Which 3 components are a part of OCI Identity and Access Management Service?
Within the Oracle Cloud Identity and Access Management (IAM) Service, three key components play a crucial role in managing identities and controlling access within the Oracle Cloud Infrastructure (OCI). These components include Identity Providers, Users, and Groups. Identity Providers facilitate authentication processes, Users represent individuals granted access to resources, and Groups allow for efficient management of access permissions by grouping users with similar roles or responsibilities. By leveraging these essential components, organisations can establish a secure and well-structured identity and access management framework within the Oracle Cloud environment.
What is Oracle Identity access management?
Oracle Identity Access Management, or Oracle IAM, is a robust solution designed to manage user identities and control access to resources within an organisation’s IT environment. It encompasses a set of tools and processes that enable businesses to authenticate users, assign appropriate levels of access based on roles and responsibilities, and monitor user activities for security and compliance purposes. Oracle IAM streamlines identity management tasks, enhances security through features like multi-factor authentication, and helps organisations maintain regulatory compliance by providing audit trails and reporting capabilities. Overall, Oracle Identity Access Management plays a crucial role in securing digital assets and ensuring efficient access control in today’s complex IT landscapes.
What is the role of IAM in oracle cloud?
In Oracle Cloud, Identity and Access Management (IAM) plays a crucial role in ensuring the security and integrity of digital assets within the cloud environment. IAM in Oracle Cloud is responsible for managing user identities, controlling access to resources, and enforcing security policies to protect sensitive data. By defining roles, permissions, and access controls, IAM enables organisations to establish a secure framework that governs who can access what resources and under what conditions. This proactive approach not only safeguards against unauthorised access but also streamlines user management processes, enhances compliance efforts, and contributes to overall data protection within the Oracle Cloud ecosystem.