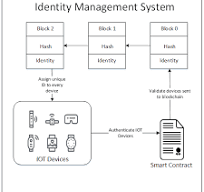
The Importance of Identity Management Systems in Today’s Digital World
In the era of digital transformation, where data breaches and cyber threats are on the rise, the need for robust identity management systems has become more critical than ever. An Identity Management System (IDM) is a framework of policies, processes, and technologies that facilitates the management of digital identities. It encompasses user authentication, access control, and identity governance to ensure secure access to resources while protecting sensitive information.
Enhancing Security
One of the primary functions of an IDM system is to enhance security by verifying the identities of users accessing digital assets. Through mechanisms such as multi-factor authentication and biometric verification, organisations can significantly reduce the risk of unauthorised access and data breaches. By implementing strong authentication methods, IDM systems create a secure barrier against cyber threats.
Improving Operational Efficiency
Identity management systems streamline user provisioning and deprovisioning processes, allowing organisations to efficiently manage user access throughout their lifecycle. Automated workflows for onboarding and offboarding employees not only save time but also reduce the likelihood of human errors that could lead to security vulnerabilities. By centralising user management tasks, IDM systems improve operational efficiency and compliance with regulatory requirements.
Enabling Single Sign-On
Another key benefit of IDM systems is their ability to enable Single Sign-On (SSO) capabilities. SSO allows users to access multiple applications with a single set of credentials, eliminating the need to remember multiple passwords. This not only enhances user experience but also reduces password fatigue and enhances security by minimising the risk of weak or reused passwords.
Ensuring Regulatory Compliance
In today’s regulatory landscape, organisations are required to adhere to various data protection laws and industry standards. Identity management systems play a crucial role in ensuring compliance by providing audit trails, access controls, and policy enforcement mechanisms. By maintaining a comprehensive record of user activities and permissions, IDM systems help organisations demonstrate compliance with regulations such as GDPR, HIPAA, and PCI-DSS.
The Future of Identity Management
As technology continues to evolve, so too will identity management systems. With advancements in artificial intelligence and machine learning, IDM systems are becoming more intelligent in detecting anomalies and predicting potential security threats. The future holds promise for adaptive authentication methods that adjust based on user behaviour patterns, further strengthening security measures.
In conclusion, identity management systems are indispensable tools for modern organisations seeking to safeguard their digital assets and maintain regulatory compliance. By investing in robust IDM solutions, businesses can fortify their cybersecurity posture while enabling seamless access for authorised users in today’s interconnected world.
8 Essential Tips for Effective Identity Management System Implementation
- 1. Implement strong password policies to enhance security.
- 2. Use multi-factor authentication for an added layer of protection.
- 3. Regularly review and update user access permissions.
- 4. Conduct training sessions to educate users on best practices for identity management.
- 5. Monitor user activity and set up alerts for suspicious behaviour.
- 6. Encrypt sensitive data to prevent unauthorised access.
- 7. Implement role-based access control to limit privileges based on job roles.
- 8. Have a clear process in place for handling account deactivation upon employee departure.
1. Implement strong password policies to enhance security.
Implementing strong password policies is a fundamental aspect of enhancing security within an Identity Management System. By requiring users to create complex passwords that include a combination of letters, numbers, and special characters, organisations can significantly reduce the risk of password-based attacks. Enforcing regular password changes and prohibiting the reuse of previous passwords further strengthens the authentication process and mitigates the likelihood of unauthorised access. Strong password policies not only bolster the overall security posture of an IDM system but also instil a culture of cybersecurity awareness among users, fostering a proactive approach to safeguarding sensitive information.
2. Use multi-factor authentication for an added layer of protection.
Employing multi-factor authentication is a highly effective strategy to bolster the security of an identity management system. By requiring users to provide two or more verification factors, such as a password, biometric data, or a unique code sent to their mobile device, organisations can significantly reduce the risk of unauthorised access. This additional layer of protection enhances the overall security posture of the system by making it more challenging for malicious actors to compromise user accounts. Multi-factor authentication is a proactive measure that strengthens identity verification processes and helps safeguard sensitive information from potential cyber threats.
3. Regularly review and update user access permissions.
It is crucial to regularly review and update user access permissions within an Identity Management System to maintain a secure and efficient digital environment. By conducting periodic reviews of user access rights, organisations can ensure that users have the appropriate level of access required for their roles while mitigating the risk of unauthorised access. Updating permissions in line with changes in employee roles or responsibilities helps prevent security gaps and reduces the likelihood of insider threats. By implementing a proactive approach to managing user access, organisations can enhance data security, compliance, and overall operational effectiveness within their IT infrastructure.
4. Conduct training sessions to educate users on best practices for identity management.
To enhance the effectiveness of your identity management system, it is crucial to conduct training sessions aimed at educating users on best practices. By empowering users with knowledge about identity management protocols and security measures, organisations can significantly reduce the risk of security breaches and data leaks. Training sessions provide users with valuable insights into creating strong passwords, recognising phishing attempts, and understanding the importance of safeguarding their digital identities. Through continuous education and awareness initiatives, organisations can foster a culture of security consciousness among employees, ultimately strengthening the overall cybersecurity posture of the organisation.
5. Monitor user activity and set up alerts for suspicious behaviour.
To enhance the security of your identity management system, it is crucial to monitor user activity and establish alerts for any suspicious behaviour. By actively tracking user actions, such as login attempts, access to sensitive data, or changes in permissions, organisations can quickly detect anomalies that may indicate a security threat. Setting up alerts for unusual patterns or activities can help mitigate risks proactively and enable timely responses to potential security incidents. Monitoring user activity and implementing alert systems are essential practices in maintaining a secure and vigilant identity management environment.
6. Encrypt sensitive data to prevent unauthorised access.
Encrypting sensitive data is a crucial step in safeguarding information within an Identity Management System. By encrypting data, organisations can protect it from unauthorised access and ensure that even if a breach occurs, the data remains secure and unreadable to malicious actors. Encryption adds an extra layer of security to sensitive information, making it essential in maintaining the confidentiality and integrity of user data within the IDM system.
7. Implement role-based access control to limit privileges based on job roles.
Implementing role-based access control is a crucial aspect of an effective Identity Management System. By assigning privileges based on job roles, organisations can ensure that users have access only to the resources and information necessary for their specific responsibilities. This granular approach not only enhances security by reducing the risk of unauthorised access but also streamlines user management processes. Role-based access control helps organisations enforce the principle of least privilege, limiting potential exposure to sensitive data and mitigating insider threats. By aligning access permissions with job roles, organisations can maintain a secure and compliant environment while promoting operational efficiency.
8. Have a clear process in place for handling account deactivation upon employee departure.
Having a clear process in place for handling account deactivation upon an employee’s departure is a crucial aspect of identity management system best practices. By promptly deactivating user accounts when an employee leaves the organisation, businesses can mitigate security risks associated with former employees retaining access to sensitive information. This proactive approach not only enhances data security but also ensures compliance with regulatory requirements concerning user access control. Implementing a structured account deactivation process is essential for maintaining the integrity of the organisation’s digital assets and safeguarding against potential threats.