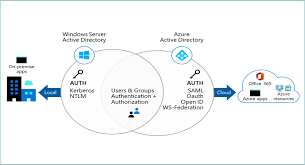
Azure Active Directory Access Control
Azure Active Directory (Azure AD) is Microsoft’s cloud-based identity and access management service that helps your employees sign in and access resources securely. One crucial aspect of Azure AD is access control, which plays a vital role in ensuring that only authorised users can access specific resources within your organisation.
Role-Based Access Control (RBAC)
Azure AD offers Role-Based Access Control (RBAC), a method of managing access to resources based on the roles assigned to users. With RBAC, you can define roles with specific permissions and assign those roles to users or groups. This approach simplifies access management by granting permissions at a role level rather than individual user level.
Conditional Access Policies
Conditional Access Policies in Azure AD enable you to enforce additional security measures based on specific conditions. For example, you can require multi-factor authentication for users attempting to access sensitive data outside the corporate network or prompt for device compliance checks before granting access. These policies help strengthen security without compromising user experience.
Privileged Identity Management (PIM)
Azure AD Privileged Identity Management (PIM) provides oversight and control over privileged roles within your organisation. PIM allows you to monitor and manage who has access to privileged roles, require approval for elevation of privileges, and enforce just-in-time access for critical tasks. By implementing PIM, you can reduce the risk of misuse of privileged accounts.
Access Reviews
To maintain a secure environment, regular access reviews are essential. Azure AD offers automated access reviews that enable administrators to periodically review user access rights and ensure that permissions are up-to-date and aligned with business requirements. By conducting these reviews, you can mitigate the risk of excessive or inappropriate access.
Conclusion
Azure Active Directory provides robust access control capabilities that empower organisations to secure their resources effectively. By leveraging features such as RBAC, Conditional Access Policies, Privileged Identity Management, and Access Reviews, organisations can establish a strong security posture while enabling seamless collaboration and productivity for their users.
Essential Tips for Enhancing Access Control with Azure Active Directory
- Use Azure AD roles to assign permissions to users and groups.
- Implement conditional access policies to control access based on conditions.
- Enable multi-factor authentication for added security.
- Regularly review and audit user access rights in Azure AD.
- Utilise Privileged Identity Management for managing admin roles effectively.
- Set up role-based access control (RBAC) to restrict access based on job roles.
- Integrate with Azure AD Connect to synchronise on-premises directories with Azure AD.
- Monitor sign-ins and security alerts in Azure AD for potential threats.
Use Azure AD roles to assign permissions to users and groups.
When implementing access control in Azure Active Directory, a valuable tip is to utilise Azure AD roles to assign permissions to users and groups. By defining roles with specific sets of permissions and then assigning those roles to users or groups, organisations can streamline access management processes. This approach simplifies the task of granting and revoking permissions, as administrators can manage access at a role level rather than dealing with individual user permissions. Utilising Azure AD roles enhances security, ensures consistency in access control, and facilitates efficient administration of resources within the Azure environment.
Implement conditional access policies to control access based on conditions.
By implementing conditional access policies in Azure Active Directory, organisations can exert granular control over user access based on specific conditions. This powerful feature allows administrators to set rules that dictate when and how users can access resources, adding an extra layer of security to the authentication process. By defining conditions such as location, device compliance, or user risk level, organisations can tailor access controls to match their security requirements, thereby enhancing overall data protection and reducing the risk of unauthorised access.
Enable multi-factor authentication for added security.
Enabling multi-factor authentication in Azure Active Directory is a highly recommended practice to enhance security. By requiring users to provide an additional verification method beyond just a password, such as a code sent to their mobile device or biometric authentication, organisations can significantly reduce the risk of unauthorised access. Multi-factor authentication adds an extra layer of protection that strengthens the overall security posture of the environment, safeguarding sensitive data and resources from potential threats.
Regularly review and audit user access rights in Azure AD.
Regularly reviewing and auditing user access rights in Azure Active Directory is a critical practice to ensure the security and integrity of your organisation’s resources. By conducting periodic assessments of user permissions, you can identify and rectify any discrepancies or unauthorised access promptly. This proactive approach not only helps prevent potential security breaches but also ensures that users have the appropriate level of access required for their roles. Regular reviews and audits of user access rights in Azure AD are essential steps towards maintaining a robust security posture and safeguarding sensitive data within your environment.
Utilise Privileged Identity Management for managing admin roles effectively.
By utilising Privileged Identity Management within Azure Active Directory, organisations can effectively manage admin roles and enhance security measures. Privileged Identity Management offers oversight and control over privileged roles, allowing administrators to monitor and regulate access to critical resources. By implementing PIM, organisations can enforce just-in-time access, require approval for privilege elevation, and reduce the risk of unauthorised access or misuse of privileged accounts. This proactive approach ensures that only authorised personnel have elevated permissions when necessary, strengthening overall security posture within the Azure environment.
Set up role-based access control (RBAC) to restrict access based on job roles.
Setting up Role-Based Access Control (RBAC) in Azure Active Directory is a powerful way to manage access and enhance security within an organisation. By assigning specific roles with predefined permissions to users based on their job functions, administrators can effectively restrict access to resources and data. This approach not only simplifies access management but also ensures that individuals have the necessary level of access required to perform their duties, reducing the risk of unauthorised actions and enhancing overall security posture.
Integrate with Azure AD Connect to synchronise on-premises directories with Azure AD.
Integrating with Azure AD Connect allows organisations to synchronise their on-premises directories with Azure AD seamlessly. By establishing this connection, user accounts, groups, and attributes can be synchronised between on-premises environments and the cloud, ensuring a consistent identity management experience. This integration streamlines user provisioning and access control processes, enabling administrators to manage user identities centrally while leveraging the security features of Azure AD across both on-premises and cloud resources.
Monitor sign-ins and security alerts in Azure AD for potential threats.
Monitoring sign-ins and security alerts in Azure Active Directory is a crucial tip for maintaining a secure environment. By actively monitoring user sign-ins and staying vigilant for security alerts, organisations can swiftly identify and respond to potential threats. Keeping a close eye on user activity allows for early detection of suspicious behaviour, such as unusual sign-in locations or multiple failed login attempts, enabling proactive measures to mitigate security risks. By leveraging the monitoring capabilities of Azure AD, organisations can stay ahead of potential threats and safeguard their resources effectively.