The Importance of GRC Software in Modern Business Operations
In today’s rapidly evolving business landscape, organisations face a myriad of challenges related to governance, risk management, and compliance (GRC). To effectively address these challenges and ensure the sustainability of their operations, many businesses are turning to GRC software solutions.
What is GRC Software?
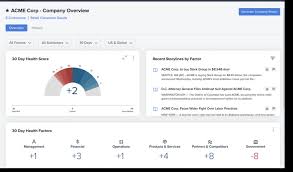
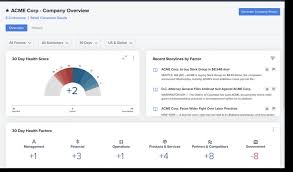
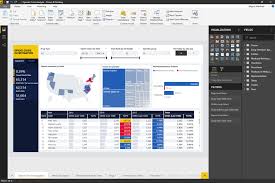
GRC software is a comprehensive tool that integrates governance, risk management, and compliance processes into a unified platform. This software enables organisations to streamline their GRC efforts, enhance visibility into potential risks and compliance issues, and improve decision-making based on data-driven insights.
The Benefits of GRC Software
Enhanced Efficiency: GRC software automates manual processes, reducing the time and resources required for compliance activities. This allows organisations to focus on strategic initiatives rather than administrative tasks.
Improved Risk Management: By centralising risk data and providing real-time monitoring capabilities, GRC software helps businesses identify and mitigate risks proactively. This leads to better decision-making and a more resilient enterprise.
Regulatory Compliance: Maintaining compliance with industry regulations and standards is crucial for avoiding penalties and reputational damage. GRC software simplifies compliance management by providing tools for tracking regulatory changes, assessing impacts, and demonstrating adherence to requirements.
Data Security: Protecting sensitive data is a top priority for modern businesses. GRC software includes features for monitoring access controls, detecting anomalies in user behaviour, and ensuring data integrity across the organisation.
Implementing GRC Software
When implementing GRC software, organisations should consider their specific needs and objectives. It’s essential to assess the current state of governance, risk management, and compliance practices within the company to determine how the software can best support improvement efforts.
Training employees on using the GRC software effectively is also crucial for maximising its benefits. By fostering a culture of accountability and transparency around GRC processes, businesses can create a more resilient framework for managing risks and complying with regulations.
The Future of GRC Software
As businesses continue to navigate complex regulatory environments and evolving cybersecurity threats, the role of GRC software will become increasingly critical. Innovations in artificial intelligence, machine learning, and predictive analytics are shaping the future of GRC solutions, enabling organisations to stay ahead of risks and compliance challenges.
In conclusion, investing in robust GRC software is not just a matter of regulatory requirements; it’s a strategic imperative for building a resilient business that can adapt to changing circumstances with confidence.
Top 5 Tips for Effectively Implementing GRC Software in Your Organisation
- Ensure the GRCC software is user-friendly for easy adoption by all team members.
- Regularly update and maintain the GRCC software to ensure optimal performance and security.
- Provide adequate training and support to users to maximize the benefits of the GRCC software.
- Customize the GRCC software to align with your organization’s specific risk management needs.
- Regularly review and assess the effectiveness of the GRCC software in managing risks and compliance.
Ensure the GRCC software is user-friendly for easy adoption by all team members.
To maximise the effectiveness of GRC software within an organisation, it is crucial to ensure that the GRCC software is user-friendly for easy adoption by all team members. A user-friendly interface and intuitive features can streamline the implementation process and encourage widespread usage across departments. By prioritising ease of use, businesses can enhance collaboration, increase engagement, and empower employees to actively participate in governance, risk management, and compliance efforts. Ultimately, a user-friendly GRCC software promotes efficiency and effectiveness in achieving GRC objectives throughout the organisation.
Regularly update and maintain the GRCC software to ensure optimal performance and security.
It is essential to regularly update and maintain your GRC software to guarantee optimal performance and security. By keeping the software up-to-date with the latest patches and enhancements, you can ensure that it remains effective in managing governance, risk, and compliance processes within your organisation. Regular maintenance also helps to address any potential vulnerabilities or issues that could compromise the security of your data and systems. By prioritising the upkeep of your GRC software, you can maximise its benefits and safeguard your business operations effectively.
Provide adequate training and support to users to maximize the benefits of the GRCC software.
To maximise the benefits of GRC software, it is essential to provide adequate training and support to users. By ensuring that employees are well-versed in using the software effectively, organisations can enhance efficiency, improve risk management practices, and maintain regulatory compliance. Investing in comprehensive training programmes and ongoing support mechanisms empowers users to leverage the full potential of the GRC software, leading to a more secure and resilient business environment.
Customize the GRCC software to align with your organization’s specific risk management needs.
Customising GRC software to align with your organisation’s specific risk management needs is a crucial tip for maximising the effectiveness of your GRC efforts. By tailoring the software to reflect the unique risks and compliance requirements of your business, you can ensure that it provides relevant insights and actionable data that directly address your challenges. Customisation allows you to focus on key risk indicators, automate processes specific to your industry, and streamline compliance activities, leading to a more efficient and targeted approach to governance, risk management, and compliance within your organisation.
Regularly review and assess the effectiveness of the GRCC software in managing risks and compliance.
It is essential for organisations to regularly review and assess the effectiveness of their GRC software in managing risks and compliance. By conducting routine evaluations, businesses can ensure that the software aligns with their evolving needs and regulatory requirements. This proactive approach allows for the identification of any gaps or areas for improvement, enabling timely adjustments to enhance the overall effectiveness of risk management and compliance efforts. Regular reviews also foster a culture of continuous improvement, where feedback from stakeholders can be incorporated to optimise the use of GRC software for better decision-making and operational resilience.