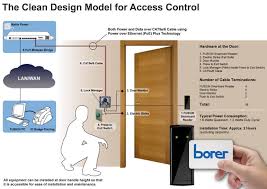
The Importance of Enterprise Identity in Today’s Business Landscape
In the digital age, where data breaches and cyber threats are prevalent, managing enterprise identity has become a critical aspect of business operations. Enterprise identity refers to the collection of information that defines an individual within an organisation’s network, granting them access to resources based on their role and permissions.
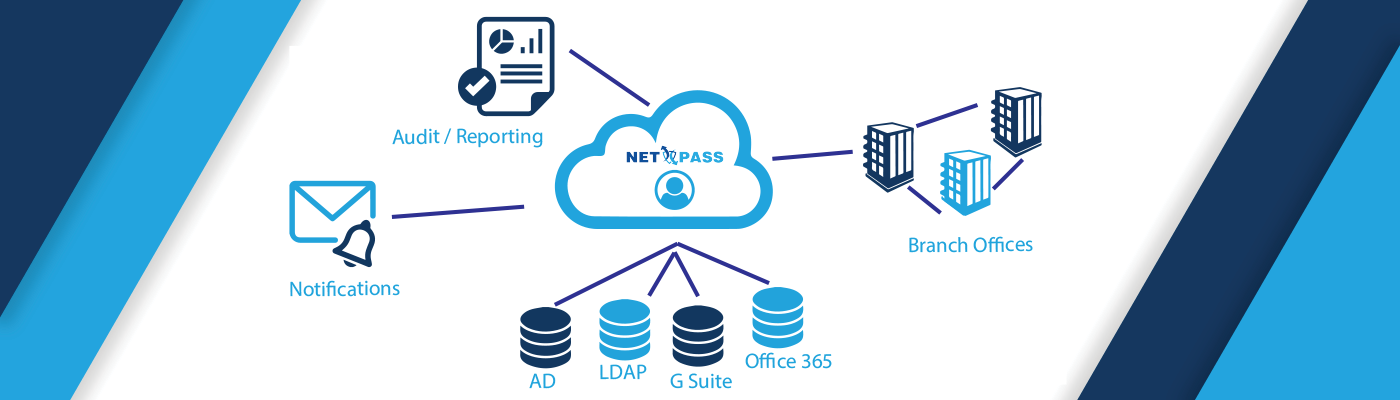
Effective management of enterprise identity is essential for maintaining security, streamlining processes, and ensuring compliance with regulations. By establishing robust identity and access management (IAM) practices, businesses can protect sensitive data, prevent unauthorised access, and facilitate seamless collaboration across departments.
Key Components of Enterprise Identity Management
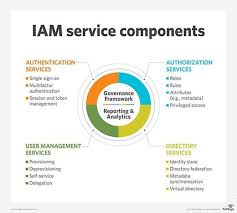
Enterprise identity management encompasses several key components:
- Authentication: Verifying the identity of users through passwords, biometrics, or multi-factor authentication methods.
- Authorisation: Determining what resources and actions users are allowed based on their roles and permissions.
- Account Provisioning: Creating, modifying, and disabling user accounts as needed throughout their lifecycle within the organisation.
- Single Sign-On (SSO): Allowing users to access multiple applications with a single set of credentials, enhancing user experience and productivity.
- Identity Governance: Establishing policies and procedures to govern access rights and ensure compliance with internal policies and regulatory requirements.
The Benefits of Effective Enterprise Identity Management
Implementing a robust enterprise identity management strategy offers numerous benefits to organisations:
- Enhanced Security: By enforcing strong authentication methods and access controls, businesses can reduce the risk of data breaches and insider threats.
- Improved Productivity: Streamlining user access to resources through SSO and automated provisioning processes enhances efficiency and reduces administrative overhead.
- Better Compliance: Meeting regulatory requirements such as GDPR or HIPAA becomes more manageable when organisations have clear visibility into user access rights and activities.
- Cross-Platform Integration: Seamless integration with cloud services, mobile devices, and third-party applications allows for greater flexibility in how employees work.
In conclusion, enterprise identity management plays a crucial role in safeguarding sensitive information, optimising business processes, and ensuring regulatory compliance. By investing in robust IAM solutions and best practices, organisations can mitigate risks associated with identity-related threats while empowering employees to work securely across various platforms.
Understanding Enterprise Identity: Key FAQs and Insights on IAM and IdP
- What’s the difference between IdP and IAM?
- What is an enterprise identity?
- What are the 4 pillars of IAM?
- What is the IAM identity?
- What are the three types of identity?
- What is IAM for an enterprise?
- What are the benefits of enterprise identity management approach?
- What is identity enterprise?
What’s the difference between IdP and IAM?
In the realm of enterprise identity management, a common query revolves around distinguishing between IdP (Identity Provider) and IAM (Identity and Access Management). The primary disparity lies in their functions: an IdP is responsible for authenticating users’ identities and providing them with access to applications and services, acting as a trusted source for user authentication. On the other hand, IAM encompasses a broader scope, focusing on not only authentication but also authorisation, provisioning, and governance of user identities throughout their lifecycle within an organisation. While an IdP serves as a specific component within the broader framework of IAM, understanding this contrast is crucial for establishing comprehensive identity management strategies that enhance security and efficiency in today’s interconnected business landscape.
What is an enterprise identity?
An enterprise identity refers to the digital representation of an individual within an organisation’s network, encompassing information such as user credentials, roles, and permissions. It serves as a means of uniquely identifying and authenticating users to grant them access to specific resources and applications based on their designated privileges. Effectively managing enterprise identity is crucial for maintaining security, ensuring compliance with regulations, and facilitating seamless collaboration across departments within a business environment. By defining and controlling user identities within the enterprise network, organisations can enhance data protection, streamline access control processes, and establish a foundation for robust identity and access management practices.
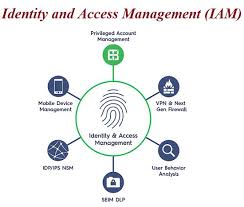
What are the 4 pillars of IAM?
In the realm of enterprise identity management, the concept of IAM (Identity and Access Management) revolves around four fundamental pillars that form the foundation of a robust security framework. These pillars include authentication, authorisation, accountability, and assurance. Authentication involves verifying the identity of users accessing resources within the network. Authorisation determines the level of access and permissions granted to individuals based on their roles. Accountability ensures that user actions are traceable and auditable for security and compliance purposes. Lastly, assurance encompasses measures to guarantee the integrity and confidentiality of data throughout the identity lifecycle within an organisation’s IT ecosystem. These four pillars collectively strengthen IAM practices, safeguarding sensitive information and bolstering overall cybersecurity posture.
What is the IAM identity?
In the realm of enterprise identity management, the term “IAM identity” refers to the unique digital representation of an individual or entity within an organisation’s Identity and Access Management (IAM) system. IAM identity encompasses a range of attributes and permissions that define a user’s access rights to resources, applications, and data within the enterprise network. By managing IAM identities effectively, businesses can ensure secure authentication, authorisation, and governance processes that protect sensitive information while enabling seamless collaboration and productivity across the organisation.
What are the three types of identity?
In the realm of enterprise identity management, a frequently asked question revolves around the three primary types of identity: user identity, device identity, and application identity. User identity refers to the individual accessing the system and encompasses attributes such as username, password, and role within the organisation. Device identity pertains to the unique characteristics of devices connecting to the network, allowing for secure authentication and authorisation based on device-specific information. Application identity involves the identification and authentication of software applications interacting within the enterprise ecosystem, ensuring secure communication and data exchange between different services. Understanding these distinct types of identities is crucial for implementing a comprehensive identity management strategy that safeguards sensitive data and enhances overall security within an organisation’s digital infrastructure.
What is IAM for an enterprise?
Identity and Access Management (IAM) for an enterprise refers to the framework of policies, technologies, and processes that organisations implement to manage digital identities and control access to their resources. IAM systems play a crucial role in ensuring that the right individuals have the appropriate level of access to company data and applications based on their roles and responsibilities. By centralising identity management, enforcing strong authentication measures, and maintaining strict access controls, enterprises can enhance security, streamline user provisioning processes, and achieve compliance with regulatory requirements. IAM is essential for protecting sensitive information, preventing data breaches, and fostering a secure digital environment within the enterprise.
What are the benefits of enterprise identity management approach?
When considering the benefits of an enterprise identity management approach, organisations can expect enhanced security measures, streamlined access controls, improved operational efficiency, and simplified compliance with regulatory standards. By implementing robust identity management practices, businesses can reduce the risk of data breaches, enforce strict authentication protocols, enhance user productivity through seamless access to resources, and establish a clear governance framework for managing user identities and permissions effectively. This approach not only strengthens overall security posture but also facilitates smoother collaboration across departments and ensures that businesses meet industry-specific compliance requirements with greater ease.
What is identity enterprise?
In the realm of cybersecurity and IT infrastructure, the term “identity enterprise” refers to the comprehensive framework and practices put in place by organisations to manage and secure the digital identities of individuals accessing their systems and resources. This includes defining user roles, assigning appropriate permissions, implementing authentication mechanisms, and monitoring user activities to ensure compliance and mitigate security risks. Essentially, an identity enterprise is a strategic approach that focuses on effectively controlling and protecting user identities within an organisation’s network, playing a pivotal role in maintaining data integrity and safeguarding against potential cyber threats.