The Importance of IT Compliance Software in Today’s Business Environment
In the fast-paced and ever-evolving landscape of modern business, ensuring compliance with various regulations and standards is crucial for organisations across all industries. One area where compliance is particularly critical is in Information Technology (IT). With the increasing reliance on digital systems and data, maintaining IT compliance has become a top priority for businesses to protect their assets, mitigate risks, and uphold trust with customers.
What is IT Compliance Software?
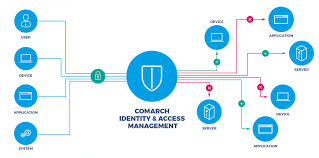
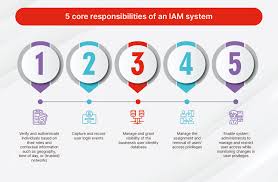
IT compliance software refers to tools and solutions designed to help organisations manage and monitor their adherence to regulatory requirements, industry standards, and internal policies related to IT operations. These software applications are essential for automating compliance processes, identifying potential issues, and ensuring that IT systems meet the necessary security and governance criteria.
The Benefits of Using IT Compliance Software
Implementing IT compliance software offers a range of benefits for businesses:
- Enhanced Security: By continuously monitoring IT systems for compliance violations, organisations can strengthen their security posture and detect potential threats before they escalate.
- Risk Mitigation: Identifying non-compliance issues proactively helps mitigate risks associated with data breaches, financial penalties, and reputational damage.
- Efficiency: Automation features in IT compliance software streamline auditing processes, saving time and resources while ensuring accuracy in compliance assessments.
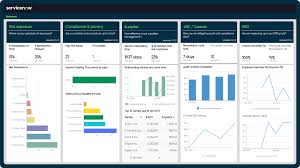
- Reporting & Documentation: Comprehensive reporting capabilities enable organisations to generate audit trails, documentation, and evidence of compliance efforts for regulatory purposes.
- Regulatory Alignment: Keeping up-to-date with regulatory changes becomes more manageable with IT compliance software that alerts users to new requirements and assists in adapting policies accordingly.
Choosing the Right IT Compliance Software
Selecting the most suitable IT compliance software for your organisation requires careful consideration of factors such as scalability, integration capabilities with existing systems, user-friendliness, reporting functionalities, and vendor support. It’s essential to assess your specific compliance needs and evaluate how each software solution aligns with your goals before making a decision.
In Conclusion
In today’s digital age where data privacy regulations are stringent and cyber threats are rampant, investing in robust IT compliance software is no longer optional but a necessity. By leveraging these tools effectively, businesses can stay ahead of regulatory requirements, safeguard sensitive information, build trust with stakeholders, and ultimately achieve long-term success in a compliant manner.
7 Essential Tips for Ensuring IT Compliance Software Meets Regulatory Standards
- Ensure the software complies with relevant data protection laws such as GDPR.
- Regularly update the software to address any security vulnerabilities.
- Implement user access controls to restrict access to sensitive information.
- Conduct regular audits to ensure compliance with industry regulations.
- Provide training to employees on using the software in a compliant manner.
- Maintain documentation of compliance efforts for record-keeping purposes.
- Consider automation features in the software to streamline compliance processes.
Ensure the software complies with relevant data protection laws such as GDPR.
It is crucial to ensure that the IT compliance software you choose aligns with pertinent data protection laws, such as the General Data Protection Regulation (GDPR). By selecting software that complies with GDPR and other relevant regulations, you can enhance data security, safeguard personal information, and demonstrate your commitment to upholding privacy rights. Ensuring compliance with data protection laws not only mitigates legal risks but also fosters trust with customers and stakeholders by showing your dedication to protecting their sensitive data.
Regularly update the software to address any security vulnerabilities.
It is crucial to regularly update IT compliance software to address any security vulnerabilities that may arise. By staying current with software updates, organisations can ensure that their systems are equipped with the latest security patches and enhancements to prevent potential cyber threats. Proactive software updates play a vital role in maintaining a robust IT compliance posture and safeguarding sensitive data from security breaches.
Implement user access controls to restrict access to sensitive information.
To enhance IT compliance and data security, it is crucial to implement robust user access controls that restrict access to sensitive information within an organisation’s IT systems. By setting up granular permissions and restrictions, businesses can ensure that only authorised personnel have the necessary privileges to view or modify sensitive data. This proactive measure not only helps prevent unauthorised access and potential data breaches but also aligns with regulatory requirements on data protection and confidentiality. Effective user access controls are a fundamental aspect of maintaining IT compliance and safeguarding valuable information assets.
Conduct regular audits to ensure compliance with industry regulations.
To maintain adherence to industry regulations, it is essential for organisations to conduct regular audits using IT compliance software. By scheduling routine assessments of IT systems and processes, businesses can proactively identify any non-compliance issues, rectify them promptly, and demonstrate a commitment to upholding regulatory standards. These audits not only help mitigate risks associated with breaches and penalties but also instil a culture of continuous improvement in IT governance and security practices.
Provide training to employees on using the software in a compliant manner.
To ensure effective implementation of IT compliance software within an organisation, it is essential to provide comprehensive training to employees on using the software in a compliant manner. Equipping staff with the necessary knowledge and skills not only enhances their understanding of regulatory requirements but also empowers them to utilise the software optimally to maintain data security and uphold compliance standards. By investing in training initiatives, businesses can foster a culture of compliance awareness among employees, mitigate human errors that could lead to non-compliance issues, and ultimately strengthen the overall cybersecurity posture of the organisation.
Maintain documentation of compliance efforts for record-keeping purposes.
It is essential for organisations to maintain thorough documentation of their compliance efforts when utilising IT compliance software. Keeping detailed records serves as a crucial aspect of record-keeping practices, enabling businesses to demonstrate their commitment to meeting regulatory requirements and internal policies. By documenting compliance activities, including audits, assessments, and remediation actions, organisations can establish a clear trail of their efforts towards maintaining a secure and compliant IT environment. This documentation not only aids in regulatory audits but also provides valuable insights for continuous improvement and accountability within the organisation.
Consider automation features in the software to streamline compliance processes.
When evaluating IT compliance software, it is advisable to consider the inclusion of automation features that can significantly streamline compliance processes. Automation not only saves time and resources but also enhances accuracy in compliance assessments by reducing the likelihood of human error. By automating repetitive tasks such as data collection, analysis, and reporting, organisations can efficiently manage their compliance efforts, identify issues promptly, and maintain a proactive stance towards regulatory requirements. Embracing automation in IT compliance software can lead to increased efficiency, improved security posture, and better overall governance of IT operations.