The Importance of Security Access Management in Today’s Digital World
In an era where data breaches and cyber threats are increasingly prevalent, the need for robust security access management has never been more critical. Security access management refers to the processes and technologies that organisations implement to control and monitor access to their sensitive information and resources.
Effective security access management plays a vital role in safeguarding against unauthorised access, data leaks, and other security incidents that can compromise the integrity and confidentiality of valuable assets. By implementing stringent access controls, organisations can mitigate risks and ensure that only authorised individuals have the necessary permissions to view or modify sensitive data.
The Key Components of Security Access Management
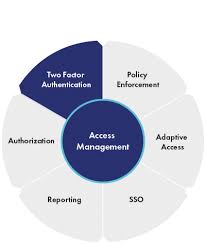
Security access management encompasses a range of practices aimed at protecting digital assets from internal and external threats. Some key components include:
- Authentication: Verifying the identity of users before granting access to systems or data.
- Authorisation: Assigning specific permissions and privileges based on users’ roles and responsibilities.
- Access Control: Implementing mechanisms to restrict or allow access to resources based on predefined policies.
- Audit Trails: Logging and monitoring user activities to track changes and detect suspicious behaviour.
The Benefits of Effective Security Access Management
Implementing robust security access management practices offers several benefits to organisations, including:
- Data Protection: Safeguarding sensitive information from unauthorised disclosure or tampering.
- Compliance: Ensuring adherence to regulatory requirements by controlling access to confidential data.
- Risk Mitigation: Minimising the likelihood of security incidents by proactively managing access rights.
- Operational Efficiency: Streamlining user authentication processes and reducing administrative overhead.
In Conclusion
In conclusion, security access management is a fundamental aspect of modern cybersecurity strategies. By establishing robust controls over who can access critical resources within an organisation, businesses can enhance their overall security posture and protect themselves against evolving cyber threats. Investing in effective security access management not only helps mitigate risks but also instils trust among stakeholders that their valuable data is being safeguarded appropriately.
Understanding Security Access Management: Key Questions and Insights
- What is security access management?
- Why is security access management important for businesses?
- How does security access management help in preventing data breaches?
- What are the key components of a security access management system?
- What role does authentication play in security access management?
What is security access management?
Security access management refers to the comprehensive set of processes and technologies implemented by organisations to regulate and supervise access to their digital assets, systems, and sensitive information. It involves mechanisms such as authentication, authorisation, access control, and audit trails to ensure that only authorised individuals have the necessary permissions to view or modify specific resources. By defining and enforcing access policies, security access management helps prevent unauthorised access, data breaches, and other security incidents that could compromise the confidentiality and integrity of valuable data. In essence, security access management is a crucial component of cybersecurity strategies aimed at protecting organisations from internal and external threats in today’s increasingly interconnected digital landscape.
Why is security access management important for businesses?
Ensuring effective security access management is crucial for businesses to protect their valuable assets and sensitive information from unauthorised access and potential security breaches. By implementing robust access controls, businesses can prevent data leaks, insider threats, and other security incidents that could compromise the integrity and confidentiality of their data. Security access management also helps businesses comply with regulatory requirements by ensuring that only authorised individuals have access to specific resources. By investing in comprehensive security access management practices, businesses can safeguard their digital infrastructure, mitigate risks, and maintain the trust of their customers and stakeholders in today’s increasingly interconnected and vulnerable digital landscape.
How does security access management help in preventing data breaches?
Security access management plays a crucial role in preventing data breaches by implementing strict controls over who can access sensitive information within an organisation. By enforcing robust authentication mechanisms, such as multi-factor authentication and strong password policies, security access management ensures that only authorised users can log in to systems and applications. Additionally, through effective authorisation practices, access rights are granted based on users’ roles and responsibilities, limiting exposure to confidential data. Access control mechanisms further restrict privileges to specific resources, reducing the risk of unauthorised data access or manipulation. By monitoring user activities and maintaining audit trails, security access management helps detect suspicious behaviour and potential security threats proactively, thus enhancing overall cybersecurity resilience and significantly reducing the likelihood of data breaches.
What are the key components of a security access management system?
When discussing the key components of a security access management system, it is essential to highlight several critical elements that form the foundation of robust access control. Authentication, authorisation, access control, and audit trails are fundamental components that work together to ensure the security and integrity of digital assets. Authentication involves verifying the identity of users before granting access, while authorisation assigns specific permissions based on roles and responsibilities. Access control mechanisms restrict or allow access to resources based on predefined policies, and audit trails enable the monitoring of user activities for tracking changes and detecting any suspicious behaviour. These components collectively contribute to a comprehensive security access management system that helps organisations protect their sensitive information from unauthorised access and potential security threats.
What role does authentication play in security access management?
Authentication plays a pivotal role in security access management by verifying the identity of users seeking access to digital resources. Through authentication mechanisms such as passwords, biometrics, or multi-factor authentication, organisations can ensure that individuals are who they claim to be before granting them permissions to sensitive data or systems. By authenticating users effectively, security access management can prevent unauthorised access and protect against potential security breaches. Strong authentication practices are essential in establishing a secure environment where only authorised users have the necessary privileges to interact with critical assets, thereby enhancing overall cybersecurity posture.