The Importance of PCI Privileged Access Management
Privileged access management (PAM) is a critical component of any organisation’s cybersecurity strategy, particularly when it comes to maintaining compliance with the Payment Card Industry Data Security Standard (PCI DSS). PCI DSS outlines specific requirements for securing cardholder data, and privileged access management plays a key role in meeting these requirements.
What is PCI Privileged Access Management?
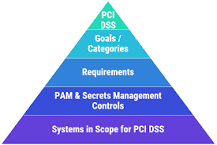
PCI privileged access management refers to the processes and technologies that organisations implement to control, monitor, and secure privileged accounts that have access to sensitive cardholder data. This includes accounts with elevated permissions that can potentially be exploited by cyber attackers to compromise the security of payment card information.
The Benefits of Implementing PCI PAM
By implementing PCI privileged access management, organisations can:
- Enhance security: By restricting and monitoring privileged access, organisations can reduce the risk of data breaches and unauthorised activities.
- Ensure compliance: Meeting PCI DSS requirements for privileged account management is essential for maintaining compliance and avoiding costly penalties.
- Improve visibility: PAM solutions provide detailed insights into who has accessed sensitive data, when, and for what purpose, enabling better threat detection and incident response.
- Streamline operations: Automating privilege management processes can increase operational efficiency and reduce the burden on IT teams.
Best Practices for PCI PAM
Organisations looking to enhance their PCI privileged access management should consider implementing the following best practices:
- Implement strong authentication mechanisms for privileged accounts.
- Enforce least privilege principles to restrict access based on job roles and responsibilities.
- Monitor and audit all privileged access activities in real-time.
- Regularly review and update access controls to align with changing business needs.
- Educate employees on the importance of secure privilege management practices.
In conclusion, PCI privileged access management is a crucial aspect of securing cardholder data and maintaining compliance with regulatory standards. By implementing robust PAM solutions and following best practices, organisations can strengthen their security posture, reduce risks, and safeguard sensitive information from cyber threats.
Understanding PCI Privileged Access Management: Standards, Management, Purpose, and PAM Usage
- What is PCI standard for?
- What is PCI management?
- What is the purpose of a PCI?
- What is Pam used for?
What is PCI standard for?
The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards established to ensure the secure handling of cardholder data and protect against payment card fraud. Compliance with the PCI DSS is mandatory for any organisation that processes, stores, or transmits payment card information. The standard aims to safeguard sensitive data, such as credit card numbers and personal information, by setting requirements for network security, access control measures, encryption protocols, regular monitoring, and vulnerability management. Adhering to the PCI DSS helps businesses build trust with customers, mitigate financial risks associated with data breaches, and demonstrate a commitment to maintaining a secure payment environment.
What is PCI management?
PCI management, in the context of cybersecurity and compliance, refers to the processes and practices implemented by organisations to ensure adherence to the Payment Card Industry Data Security Standard (PCI DSS). Specifically, PCI management involves the strategic handling of sensitive cardholder data, secure payment transactions, and the protection of systems and networks that store or process payment information. It encompasses a range of activities such as risk assessment, security controls implementation, monitoring, and reporting to maintain a secure environment for cardholder data. Effective PCI management is essential for businesses that handle payment card information to mitigate risks associated with data breaches and non-compliance with regulatory requirements.
What is the purpose of a PCI?
The purpose of the Payment Card Industry Data Security Standard (PCI DSS) is to ensure the secure handling of cardholder data to prevent fraud and protect sensitive information. PCI DSS sets out a comprehensive framework of security requirements that organisations that handle payment card data must adhere to in order to maintain the integrity and confidentiality of cardholder information. By implementing PCI DSS compliance measures, businesses can enhance their cybersecurity posture, build trust with customers, and mitigate the risk of data breaches and financial losses associated with compromised payment card data.
What is Pam used for?
Privileged Access Management (PAM) is a crucial cybersecurity tool used to control, monitor, and secure privileged accounts within an organisation. These privileged accounts typically have elevated permissions that grant access to sensitive data and critical systems. PAM solutions are utilised to enforce least privilege principles, ensuring that users only have access to the resources necessary for their specific job roles. By implementing PAM, organisations can enhance security by reducing the risk of insider threats, external cyber attacks, and data breaches. Additionally, PAM helps organisations maintain compliance with regulatory standards such as the Payment Card Industry Data Security Standard (PCI DSS) by providing detailed audit trails and monitoring capabilities for privileged access activities.