The Importance of Active Directory Audit Software
The Importance of Active Directory Audit Software
In today’s digital landscape, where cybersecurity threats are constantly evolving, maintaining the security and integrity of your organisation’s IT infrastructure is paramount. One crucial aspect of this is ensuring the proper management and monitoring of your Active Directory.
Active Directory is a vital component of most corporate networks, serving as a centralised database that stores information about network resources and enables administrators to manage users, groups, and permissions. Given its critical role, it is essential to have robust audit software in place to track and monitor changes within Active Directory effectively.
Benefits of Active Directory Audit Software:
- Enhanced Security: By implementing audit software, you can proactively detect suspicious activities, unauthorised access attempts, and potential security breaches within your Active Directory environment.
- Compliance Management: Many industries have stringent regulatory requirements concerning data security and privacy. Active Directory audit software helps you demonstrate compliance by generating detailed reports on user actions and system changes.
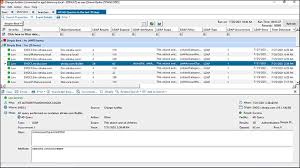
- Insightful Reporting: Audit software provides comprehensive reports that offer insights into user behaviour, permission changes, group modifications, and other critical events occurring within Active Directory.
- Real-time Monitoring: With real-time monitoring capabilities, you can stay informed about any changes or anomalies in your Active Directory environment as they happen, allowing for immediate action to be taken.
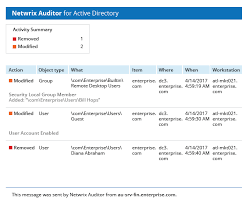
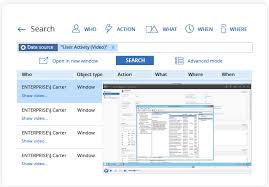
- Auditing User Activity: By tracking user activity logs, audit software enables you to identify who accessed specific resources or made changes within the directory, aiding in forensic investigations or compliance audits.
Overall, investing in high-quality Active Directory audit software is a proactive measure that can help safeguard your organisation’s sensitive data, mitigate security risks, and ensure regulatory compliance. By leveraging the power of audit tools tailored for Active Directory environments, you can strengthen your overall cybersecurity posture and maintain the trust of stakeholders.
9 Advantages of Active Directory Audit Software: Boosting Security and Efficiency
- Enhances security by detecting and alerting on suspicious activities.
- Provides detailed insights into user behaviour within Active Directory.
- Helps in compliance management by generating audit reports for regulatory requirements.
- Enables real-time monitoring of changes and access in the directory.
- Facilitates tracking of user activity logs for forensic investigations.
- Improves accountability by identifying who accessed specific resources or made changes.
- Streamlines troubleshooting with comprehensive reporting on system modifications.
- Increases operational efficiency by automating audit processes.
- Strengthens overall cybersecurity posture through proactive monitoring and analysis.
Challenges of Active Directory Audit Software: Navigating Complexity, Costs, and Integration Issues
- 1. Complexity
- 2. Resource Intensive
- 3. Cost
- 4. Training Needs
- 5. False Positives
- 6. Integration Challenges
- 7. Maintenance Overhead
Enhances security by detecting and alerting on suspicious activities.
Active Directory audit software plays a crucial role in enhancing security by actively detecting and alerting on suspicious activities within the network environment. By continuously monitoring user actions, permissions changes, and system events, the software can swiftly identify potential security threats or unauthorised access attempts. Through timely alerts and notifications, administrators can take immediate action to investigate and mitigate risks, thus strengthening the overall security posture of the organisation’s Active Directory infrastructure.
Provides detailed insights into user behaviour within Active Directory.
Active Directory audit software offers a significant advantage by providing detailed insights into user behaviour within the Active Directory environment. By tracking and analysing user actions, permissions changes, and group modifications, this feature enables organisations to gain a comprehensive understanding of how users interact with the directory. These insights not only help in identifying potential security threats and suspicious activities but also contribute to improving overall system management and compliance efforts. Understanding user behaviour within Active Directory is crucial for maintaining a secure and efficient IT infrastructure, making this capability an invaluable asset for organisations seeking to enhance their cybersecurity measures.
Helps in compliance management by generating audit reports for regulatory requirements.
Active Directory audit software plays a crucial role in compliance management by generating detailed audit reports that adhere to regulatory requirements. These reports provide a comprehensive overview of user activities, system changes, and security events within the Active Directory environment. By automating the process of tracking and documenting these activities, organisations can easily demonstrate compliance with industry regulations and standards. This proactive approach not only ensures data security and integrity but also helps in maintaining regulatory alignment, thereby mitigating risks associated with non-compliance.
Enables real-time monitoring of changes and access in the directory.
Active Directory audit software offers a significant advantage by enabling real-time monitoring of changes and access within the directory. This capability allows organisations to stay informed about any modifications or suspicious activities occurring in their Active Directory environment as they happen. By providing immediate alerts and notifications, real-time monitoring empowers administrators to swiftly respond to potential security threats, unauthorised access attempts, or policy violations, thereby enhancing overall cybersecurity resilience and ensuring the integrity of the network infrastructure.
Facilitates tracking of user activity logs for forensic investigations.
Active Directory audit software plays a crucial role in facilitating the tracking of user activity logs for forensic investigations. By meticulously recording and monitoring user actions within the Active Directory environment, this software provides valuable insights into who accessed specific resources, made changes to permissions, or performed other critical activities. In the event of a security incident or compliance breach, the ability to trace and analyse user activity logs becomes paramount for conducting thorough forensic investigations. This proactively enhances an organisation’s ability to identify and respond to security threats effectively, thereby bolstering its overall cybersecurity posture.
Improves accountability by identifying who accessed specific resources or made changes.
Active Directory audit software plays a crucial role in enhancing accountability within an organisation by accurately identifying individuals who have accessed specific resources or made changes within the system. This level of transparency not only promotes a culture of responsibility among users but also enables administrators to track and attribute actions to specific individuals, facilitating effective incident response, compliance management, and security investigations. By providing detailed insights into user activity, the software strengthens accountability measures and helps organisations maintain a secure and well-monitored Active Directory environment.
Streamlines troubleshooting with comprehensive reporting on system modifications.
Active Directory audit software offers a significant advantage by streamlining troubleshooting processes through its ability to provide comprehensive reporting on system modifications. By generating detailed reports on changes made within the Active Directory environment, IT administrators can quickly identify and address any issues that may arise. This proactive approach not only saves time but also enhances the efficiency of troubleshooting efforts, ensuring that any system modifications are promptly reviewed and resolved to maintain the integrity and security of the network.
Increases operational efficiency by automating audit processes.
Active Directory audit software offers a significant advantage by enhancing operational efficiency through the automation of audit processes. By streamlining the monitoring and tracking of user activities, system changes, and security events within Active Directory, organisations can save valuable time and resources that would otherwise be spent on manual audits. This automation not only accelerates the detection of potential security threats but also allows IT teams to focus on strategic tasks rather than routine monitoring, ultimately boosting productivity and optimising workflow efficiency.
Strengthens overall cybersecurity posture through proactive monitoring and analysis.
Active Directory audit software plays a crucial role in strengthening an organisation’s overall cybersecurity posture through proactive monitoring and analysis. By continuously tracking and analysing activities within the Active Directory environment, this software enables administrators to detect potential security threats before they escalate. Through real-time alerts and detailed reports, proactive monitoring helps identify vulnerabilities, suspicious behaviour, and unauthorised access attempts, allowing for timely intervention to mitigate risks and enhance the overall security resilience of the IT infrastructure.
1. Complexity
Implementing and configuring Active Directory audit software can pose a significant challenge due to its complexity, often necessitating a high level of technical expertise. Setting up the software to effectively monitor and track activities within the Active Directory environment may involve intricate configurations and detailed knowledge of the system’s architecture. Organisations may need to allocate resources for training or hire specialised personnel to ensure the software is optimally configured and utilised. The complexity involved in deploying Active Directory audit software underscores the importance of thorough planning and expertise to maximise its benefits while minimising potential implementation hurdles.
2. Resource Intensive
Audit software for Active Directory, while beneficial in many aspects, presents a notable drawback in its resource-intensive nature. The constant monitoring and tracking of activities within the directory can place a strain on system resources, potentially leading to decreased network performance. This increased demand for resources may result in slower processing speeds, delays in user authentication, or even system downtime. Organisations considering the implementation of Active Directory audit software should carefully assess their network’s capacity to handle the additional load to mitigate any adverse effects on overall performance.
3. Cost
High-quality Active Directory audit software can present a significant challenge in terms of cost, particularly for small to medium-sized businesses. The initial investment required to acquire and implement top-tier audit solutions may strain the budget constraints of organisations with limited resources. The ongoing maintenance and licensing fees associated with such software can further add to the financial burden, making it a considerable con for businesses aiming to enhance their IT security within budgetary constraints. As a result, careful consideration and evaluation of cost-effective alternatives are essential for ensuring that the benefits of Active Directory audit software outweigh its financial implications for smaller enterprises.
4. Training Needs
One notable drawback of active directory audit software is the potential training needs that users may face in order to maximise the utility of all its features. Implementing and managing audit software effectively often requires a certain level of expertise and familiarity with the tool’s functionalities. Users may need training sessions or resources to fully grasp how to navigate the software, interpret audit reports, set up custom alerts, and utilise advanced monitoring capabilities. This additional training can demand time and resources from organisations, impacting productivity in the short term but ultimately leading to a more secure and compliant Active Directory environment in the long run.
5. False Positives
Some audit tools may introduce the con of false positives, where they generate inaccurate alerts or reports within the Active Directory environment. This can result in IT teams having to conduct unnecessary investigations and spend valuable time addressing non-existent issues. False positives not only create confusion but also divert resources away from genuine security threats, potentially impacting the overall efficiency of the auditing process and increasing the burden on IT personnel. It is crucial for organisations to carefully evaluate the reliability and accuracy of audit software to minimise the occurrence of false positives and ensure that their efforts are focused on addressing real security concerns effectively.
6. Integration Challenges
Integration Challenges can pose a significant con when it comes to Active Directory audit software. Compatibility issues with existing IT infrastructure or applications may arise during the implementation process. These challenges can lead to disruptions in operations, delays in monitoring capabilities, and potential conflicts between the audit software and other essential systems within the organisation. Overcoming integration hurdles requires careful planning, testing, and collaboration between IT teams to ensure a seamless and effective deployment of the audit software while maintaining the functionality of existing systems.
7. Maintenance Overhead
One notable drawback of active directory audit software is the maintenance overhead it entails. Regular updates and ongoing maintenance tasks are essential to uphold the software’s functionality and effectiveness. This requirement for continuous attention can add to the workload of IT teams, requiring dedicated time and resources to ensure that the audit software remains up-to-date and capable of providing accurate insights into Active Directory activities. Failure to keep the software properly maintained may result in gaps in monitoring capabilities, potentially leaving the network vulnerable to undetected security threats.