The Importance of Cyber Security in Ensuring Network Security
In today’s digital age, where information is exchanged and stored electronically, the need for robust cyber security measures to safeguard networks has never been greater. Network security, which encompasses the protection of data transmitted over interconnected devices and systems, plays a crucial role in preventing cyber threats and attacks that can compromise sensitive information.
Understanding Cyber Security
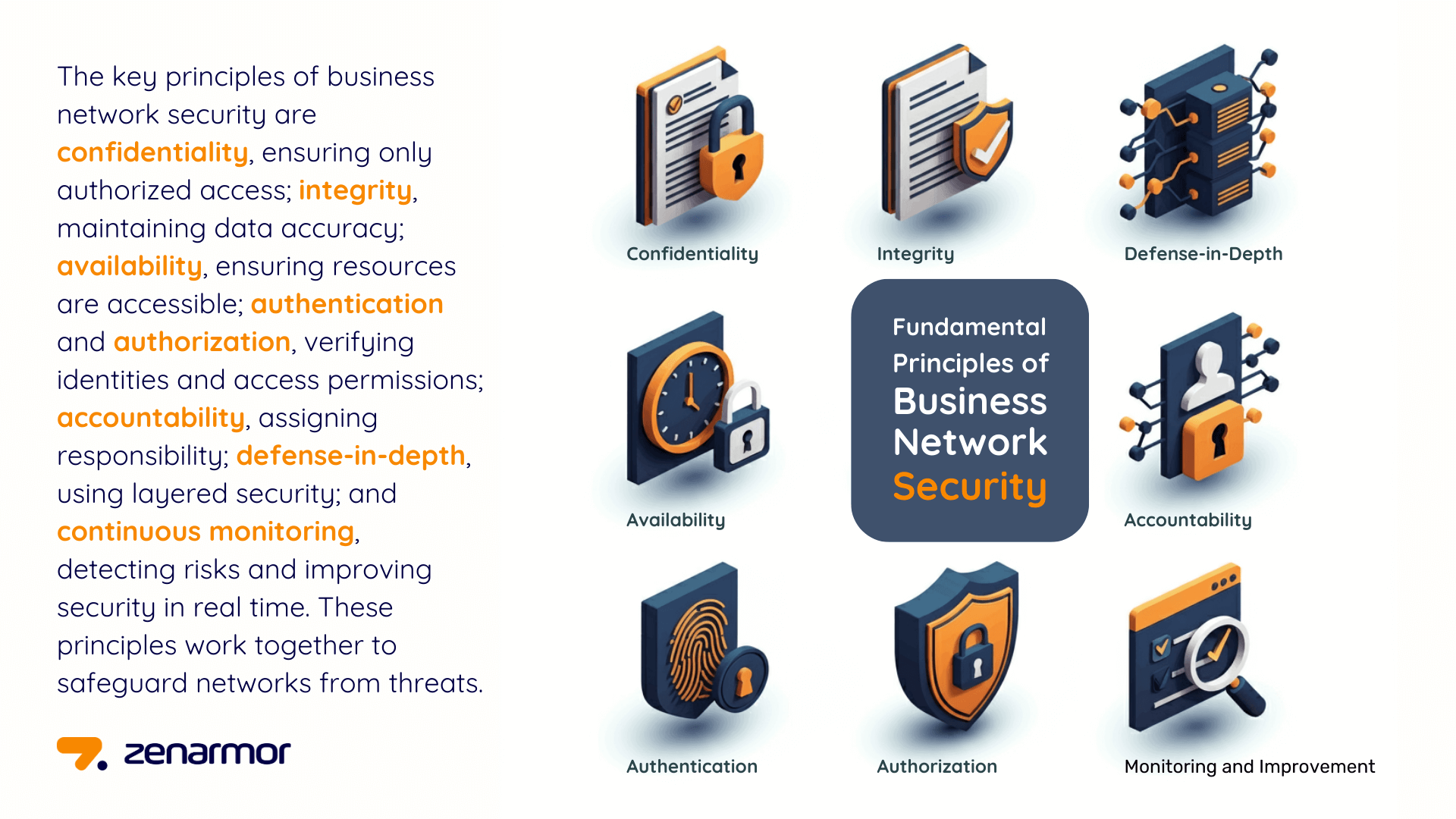
Cyber security refers to the practice of defending computer systems, networks, and data from malicious attacks. It involves implementing a combination of technologies, processes, and practices to protect against unauthorised access, data breaches, and other cyber threats. Effective cyber security measures are essential for maintaining the confidentiality, integrity, and availability of digital assets.
The Significance of Network Security
Network security focuses on securing the communication pathways within an organisation’s IT infrastructure. It involves implementing controls such as firewalls, encryption protocols, intrusion detection systems, and access controls to prevent unauthorised access to network resources. By safeguarding network connections and data transmissions, network security plays a vital role in maintaining the overall integrity of an organisation’s IT environment.
The Interconnection between Cyber Security and Network Security
Cyber security and network security are closely intertwined concepts that work hand in hand to protect digital assets. A strong network security framework forms the foundation for effective cyber security practices. By securing network infrastructure against external threats and internal vulnerabilities, organisations can mitigate risks associated with cyber attacks such as malware infections, phishing scams, and data breaches.
Best Practices for Enhancing Cyber Security Network Security
Implementing a multi-layered approach to cyber security network security is essential for comprehensive protection against evolving threats. Some best practices include:
- Regularly updating software and firmware to patch known vulnerabilities
- Enforcing strong password policies and implementing multi-factor authentication
- Conducting regular security audits and assessments to identify weaknesses
- Training employees on cyber security awareness and best practices
- Establishing incident response plans to mitigate the impact of breaches
The Future of Cyber Security Network Security
As technology continues to advance rapidly, so do the tactics employed by cyber criminals. The future of cyber security network security will involve leveraging emerging technologies such as artificial intelligence (AI), machine learning (ML), and blockchain to enhance threat detection capabilities and improve response times. By staying proactive in adopting innovative solutions, organisations can stay ahead of potential threats in an increasingly interconnected digital landscape.
In conclusion, prioritising cyber security network security is essential for safeguarding critical assets in today’s digital world. By investing in robust defences and adopting best practices, organisations can mitigate risks posed by cyber threats while maintaining trust with customers and stakeholders.
Exploring Key Aspects of Cyber and Network Security: FAQs on Types, Interrelations, and Career Prospects
- What are the 5 types of network security?
- Does network security comes under cyber security?
- What are the five types of network security?
- What is network in cyber security?
- What is cyber security in network security?
- What are the 7 types of cyber security?
- What is network security in cyber security?
- What is network security defense in cyber security?
- Is cyber security a high salary?
What are the 5 types of network security?
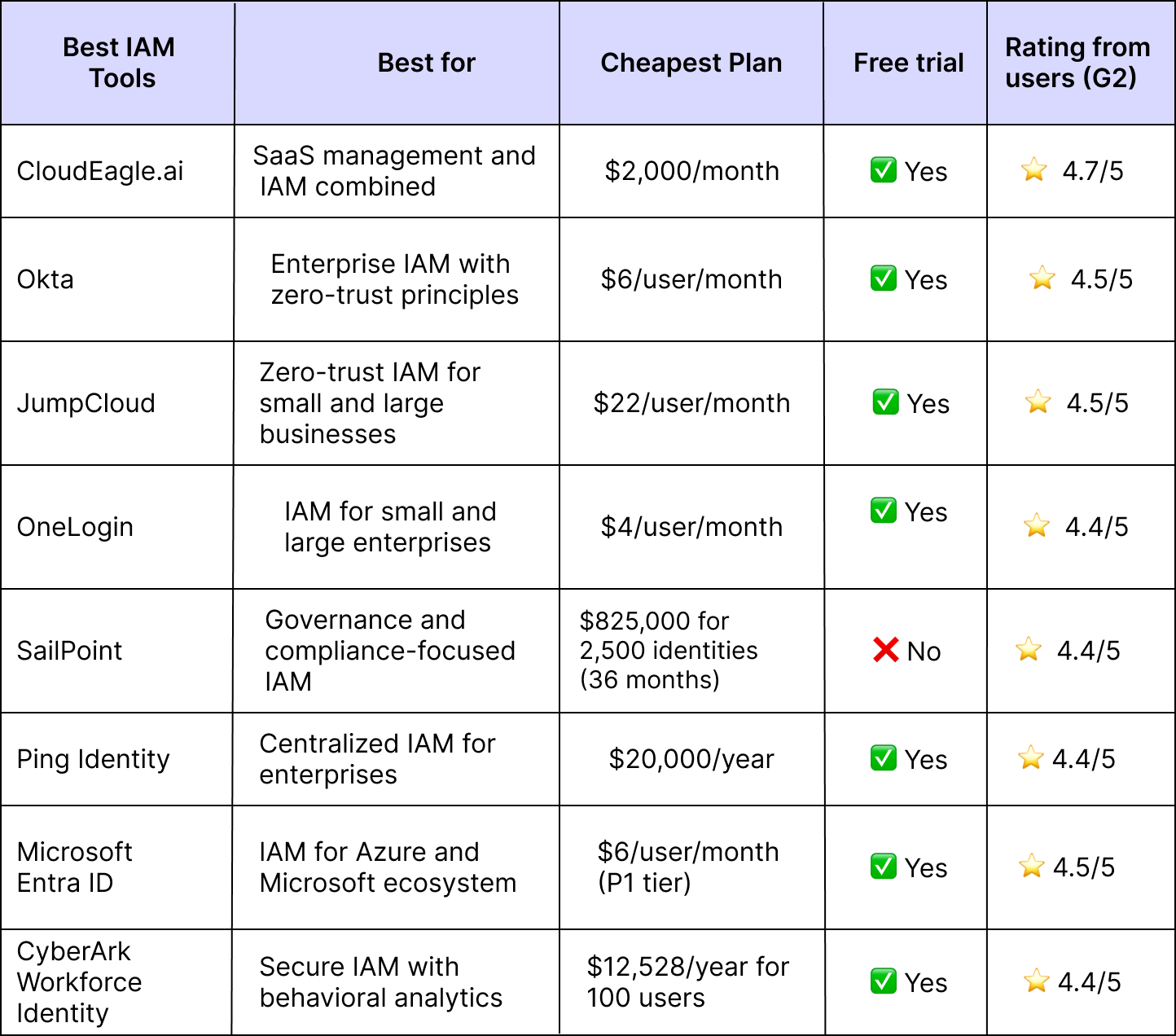
When it comes to network security, understanding the different types of measures that can be implemented is crucial for protecting digital assets. The five main types of network security include: 1) Access Control, which regulates who can access the network and what resources they can use; 2) Firewalls, which monitor and control incoming and outgoing network traffic based on predetermined security rules; 3) Intrusion Detection and Prevention Systems (IDPS), which detect and respond to potential threats in real-time; 4) Virtual Private Networks (VPNs), which create secure connections over public networks for remote access; and 5) Encryption, which scrambles data to make it unreadable without the correct decryption key. By employing a combination of these network security measures, organisations can establish a robust defence against cyber threats and ensure the integrity of their networks.
Does network security comes under cyber security?
Yes, network security falls under the broader umbrella of cyber security. Network security specifically focuses on safeguarding the communication pathways and data transmissions within an organisation’s IT infrastructure. It involves implementing measures such as firewalls, encryption protocols, intrusion detection systems, and access controls to protect against unauthorised access and cyber threats. By securing network connections and preventing potential vulnerabilities, network security contributes to the overall cyber security posture of an organisation by helping to defend against various forms of cyber attacks and ensuring the integrity of digital assets.
What are the five types of network security?
When it comes to network security, understanding the different types of safeguards is crucial in protecting digital assets from cyber threats. The five main types of network security include: 1) Firewalls, which act as a barrier between internal networks and external sources to monitor and control incoming and outgoing traffic; 2) Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS), which detect and respond to suspicious activities or potential attacks in real-time; 3) Virtual Private Networks (VPNs), which create secure connections over public networks to ensure encrypted data transmission; 4) Access Control, which regulates user permissions and restricts access to sensitive information based on defined policies; and 5) Email Security, which involves implementing measures to protect email communications from phishing attempts, malware, and other threats. Each type plays a vital role in fortifying network defences and maintaining the integrity of digital infrastructures.
What is network in cyber security?
In the realm of cyber security, a network refers to the interconnected system of devices, servers, and infrastructure that facilitate the exchange of data and information within an organisation or across the internet. Networks serve as the backbone of digital communication, enabling devices to communicate with each other and access shared resources. In the context of cyber security, understanding the concept of a network is crucial as it forms the basis for implementing protective measures to safeguard against potential threats and vulnerabilities. Securing networks through robust protocols, encryption methods, access controls, and monitoring mechanisms is essential to prevent unauthorised access, data breaches, and other malicious activities that could compromise the integrity and confidentiality of sensitive information.
What is cyber security in network security?
Cyber security in network security refers to the comprehensive measures and practices implemented to protect computer networks, systems, and data from cyber threats and attacks. It involves the deployment of security protocols, technologies, and policies to safeguard network infrastructure against unauthorised access, data breaches, malware infections, and other malicious activities. Essentially, cyber security within network security aims to ensure the confidentiality, integrity, and availability of digital assets transmitted across interconnected devices. By integrating cyber security principles into network security strategies, organisations can create a robust defence mechanism that mitigates risks and enhances the overall resilience of their IT environment.
What are the 7 types of cyber security?
There are seven key types of cyber security that encompass different aspects of protecting digital assets and information. These include network security, which focuses on securing communication pathways and data transmissions within an organisation’s IT infrastructure. Another type is application security, which involves safeguarding software and web applications from threats. Information security pertains to protecting data from unauthorised access or disclosure. Endpoint security focuses on securing individual devices such as laptops and mobile phones. Similarly, cloud security involves protecting data stored in cloud platforms. Identity management ensures that only authorised individuals have access to systems and data. Finally, disaster recovery and business continuity planning are essential for mitigating the impact of cyber incidents and ensuring operational resilience in the face of disruptions. Each type plays a critical role in fortifying cyber defences and maintaining the integrity of digital environments.
What is network security in cyber security?
Network security in cyber security refers to the measures and protocols implemented to protect the integrity, confidentiality, and availability of data transmitted over computer networks. It involves deploying a combination of hardware and software technologies, such as firewalls, intrusion detection systems, and encryption mechanisms, to safeguard network infrastructure from unauthorised access and cyber threats. Network security plays a critical role in preventing malicious actors from compromising sensitive information and disrupting communication channels within an organisation’s IT environment. By establishing robust network security controls, organisations can create a secure framework that forms the foundation for effective cyber security practices.
What is network security defense in cyber security?
Network security defence in cyber security refers to the comprehensive set of measures and strategies implemented to protect a network infrastructure from potential cyber threats and attacks. It involves the deployment of various security controls, such as firewalls, intrusion detection systems, encryption protocols, access controls, and monitoring tools, to safeguard network resources and data transmissions. Network security defence aims to prevent unauthorised access, data breaches, malware infections, and other malicious activities that could compromise the confidentiality, integrity, and availability of critical information within an organisation’s network. By establishing strong network security defences, organisations can proactively defend against evolving cyber threats and ensure the resilience of their digital assets.
Is cyber security a high salary?
In the field of cyber security, salaries can vary depending on factors such as job role, experience, qualifications, and the specific industry or organisation. Generally, cyber security professionals are in high demand due to the increasing prevalence of cyber threats and attacks. As a result, many companies are willing to offer competitive salaries to attract and retain skilled individuals who can effectively protect their digital assets. Roles such as ethical hackers, security analysts, and chief information security officers (CISOs) often command higher salaries due to their specialised skills and responsibilities in ensuring network security. Overall, while cyber security can indeed offer lucrative salary opportunities for those with the right expertise and experience, it is essential for professionals to continuously update their skills and stay abreast of industry trends to remain competitive in this dynamic field.