The Importance of Enterprise GRC Software in Modern Business Operations
In today’s fast-paced and complex business environment, organisations face a multitude of challenges when it comes to governance, risk management, and compliance (GRC). Enterprises must adhere to a growing number of regulations, manage various risks, and ensure that their operations are conducted ethically and efficiently. This is where Enterprise GRC software plays a crucial role.
What is Enterprise GRC Software?
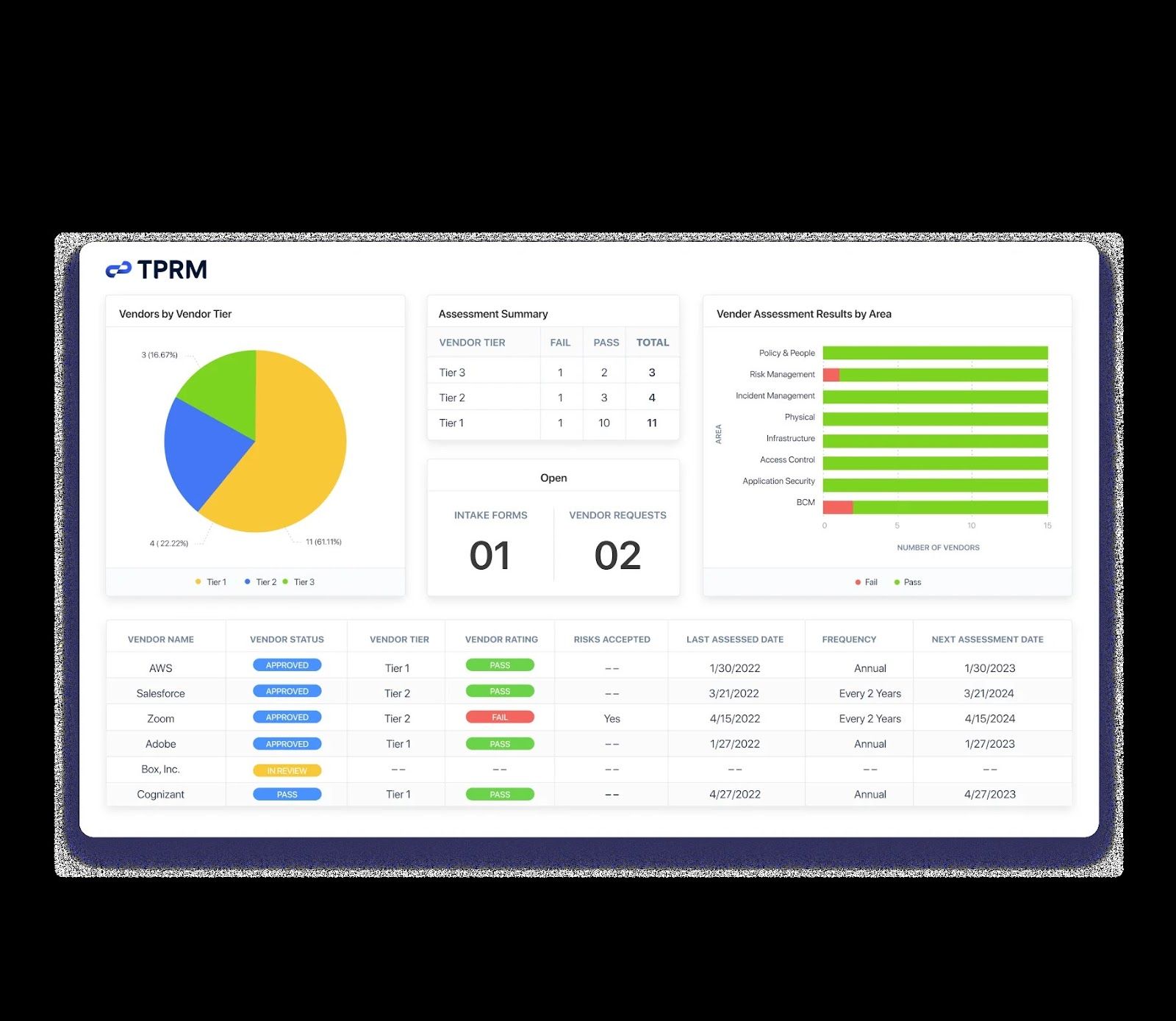
Enterprise GRC software refers to a comprehensive solution that helps organisations streamline their governance, risk management, and compliance processes. This software enables businesses to centralise their GRC activities, automate routine tasks, and gain real-time insights into their overall risk exposure and compliance status.
The Benefits of Enterprise GRC Software
Enhanced Efficiency: By leveraging Enterprise GRC software, organisations can standardise their GRC processes, eliminate manual tasks, and improve operational efficiency.
Risk Mitigation: With robust risk management capabilities, businesses can identify potential risks proactively, assess their impact, and implement mitigation strategies to protect their assets.
Compliance Management: Enterprise GRC software helps companies stay compliant with relevant regulations by providing tools for monitoring regulatory changes, conducting audits, and generating compliance reports.
Data Security: By centralising data related to governance, risk, and compliance activities, organisations can enhance data security measures and reduce the risk of data breaches or unauthorised access.
Key Features of Enterprise GRC Software
Risk Assessment Tools: Allows businesses to identify, assess, and prioritise risks based on predefined criteria.
Audit Trail Capabilities: Tracks all changes made within the system for accountability and transparency purposes.
Policy Management: Facilitates the creation, dissemination, and enforcement of corporate policies across the organisation.
Compliance Monitoring: Monitors regulatory requirements and alerts users to any non-compliance issues that need attention.
The Future of Enterprise GRC Software
As the business landscape continues to evolve with new technologies and regulations emerging regularly, the role of Enterprise GRC software will become even more critical. Organisations that invest in advanced GRC solutions will be better equipped to navigate complex challenges effectively while maintaining a competitive edge in the market.
In conclusion, Enterprise GRC software is an indispensable tool for modern businesses looking to manage risks efficiently, ensure compliance with regulations effortlessly, and maintain robust governance practices. By embracing this technology-driven approach to GRC management, organisations can safeguard their reputation, protect their assets, and drive sustainable growth in today’s dynamic business environment.
Optimising Enterprise GRC Software: 9 Essential Tips for Effective Implementation and Management
- Ensure the enterprise GRC software is user-friendly for easy adoption.
- Customise the software to meet the specific needs and requirements of your organisation.
- Regularly update and maintain the software to ensure optimal performance.
- Provide comprehensive training to employees on how to use the GRC software effectively.
- Integrate the GRC software with other systems for seamless data flow and analysis.
- Implement strong access controls to protect sensitive information stored in the software.
- Regularly review and assess the effectiveness of the GRC software in meeting compliance requirements.
- Utilise reporting features to track key metrics and generate insights for decision-making.
- Engage with vendors and peers in the industry to stay informed about best practices and new developments in enterprise GRC technology.
Ensure the enterprise GRC software is user-friendly for easy adoption.
To maximise the effectiveness of enterprise GRC software, it is crucial to ensure that the system is user-friendly for seamless adoption across the organisation. A user-friendly interface and intuitive design simplify the learning curve for employees, encouraging widespread acceptance and engagement with the software. By prioritising ease of use, businesses can enhance user satisfaction, boost productivity, and ultimately derive greater value from their investment in enterprise GRC software.
Customise the software to meet the specific needs and requirements of your organisation.
Customising Enterprise GRC software to align with the specific needs and requirements of your organisation is a crucial tip for maximising its effectiveness. By tailoring the software to fit your unique business processes, risk appetite, and compliance objectives, you can enhance its usability and relevance within your organisation. Customisation allows you to focus on key areas of concern, streamline workflows, and generate insights that are directly applicable to your operations. This personalised approach ensures that the Enterprise GRC software becomes a valuable asset that not only addresses your current challenges but also evolves with your organisation’s changing GRC landscape.
Regularly update and maintain the software to ensure optimal performance.
It is crucial for organisations utilising Enterprise GRC software to adhere to the best practice of regularly updating and maintaining the software to guarantee optimal performance. By staying current with software updates, businesses can benefit from enhanced security measures, improved functionality, and bug fixes that contribute to a smoother and more efficient GRC process. Additionally, keeping the software up-to-date ensures compatibility with evolving regulatory requirements and industry standards, enabling organisations to maintain a proactive approach to governance, risk management, and compliance activities.
Provide comprehensive training to employees on how to use the GRC software effectively.
To maximise the benefits of Enterprise GRC software, it is essential to provide comprehensive training to employees on how to utilise the software effectively. By offering thorough training sessions, organisations can ensure that their staff understand the functionalities of the GRC software, enabling them to navigate the system proficiently and leverage its features to streamline governance, risk management, and compliance processes. Well-trained employees are better equipped to proactively manage risks, maintain compliance standards, and contribute towards a culture of transparency and accountability within the organisation.
Integrate the GRC software with other systems for seamless data flow and analysis.
Integrating GRC software with other systems is a crucial tip for maximising its effectiveness in enterprise operations. By seamlessly connecting GRC software with existing systems, organisations can ensure a smooth flow of data and enable comprehensive analysis across different functions. This integration not only enhances the accuracy and timeliness of risk assessments and compliance monitoring but also promotes better decision-making based on holistic insights derived from interconnected data sources. Ultimately, by leveraging integrated GRC software, businesses can strengthen their governance practices, mitigate risks proactively, and maintain compliance more efficiently in today’s dynamic business landscape.
Implement strong access controls to protect sensitive information stored in the software.
To enhance the security of sensitive information stored within Enterprise GRC software, it is crucial to implement robust access controls. By setting up stringent access permissions and authentication mechanisms, organisations can ensure that only authorised personnel have the ability to view or modify critical data. Strong access controls help prevent data breaches, insider threats, and unauthorised access, thereby safeguarding the integrity and confidentiality of valuable information within the software. This proactive measure not only fortifies data protection but also aligns with regulatory compliance requirements, reinforcing the overall governance framework of the organisation.
Regularly review and assess the effectiveness of the GRC software in meeting compliance requirements.
It is essential for organisations to regularly review and assess the effectiveness of their Enterprise GRC software in meeting compliance requirements. By conducting periodic evaluations, businesses can ensure that the software remains aligned with changing regulations and industry standards. This proactive approach allows companies to identify any gaps or inefficiencies in their GRC processes and take corrective actions promptly. Regular reviews also enable organisations to optimise the use of their GRC software, enhance overall compliance posture, and mitigate potential risks effectively.
Utilise reporting features to track key metrics and generate insights for decision-making.
To maximise the benefits of Enterprise GRC software, it is essential to leverage its reporting features effectively. By utilising these reporting capabilities, organisations can track key metrics related to governance, risk management, and compliance activities. This data-driven approach enables businesses to generate valuable insights that inform strategic decision-making processes. Through detailed reports and analytics provided by the software, stakeholders can gain a comprehensive understanding of their GRC performance, identify areas for improvement, and make informed decisions that enhance overall operational efficiency and effectiveness.
Engage with vendors and peers in the industry to stay informed about best practices and new developments in enterprise GRC technology.
To maximise the effectiveness of Enterprise GRC software, it is essential to engage with vendors and peers in the industry. By actively participating in discussions and networking with experts, organisations can stay informed about best practices and new developments in GRC technology. This proactive approach not only helps businesses to leverage the latest innovations but also fosters a collaborative environment where knowledge sharing leads to enhanced strategies for governance, risk management, and compliance within the enterprise.