The Importance of Intrusion Detection Systems in Cybersecurity
In today’s digital age, where cyber threats are constantly evolving and becoming more sophisticated, having robust cybersecurity measures in place is essential for any organisation. One crucial component of a comprehensive cybersecurity strategy is an Intrusion Detection System (IDS).
What is an Intrusion Detection System?
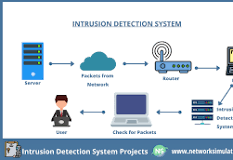
An Intrusion Detection System is a security technology that monitors network or system activities for malicious activities or policy violations. It works by analysing network traffic, system logs, and other sources of information to identify potential security incidents.
Types of Intrusion Detection Systems
There are two main types of IDS: Network-based IDS and Host-based IDS. Network-based IDS monitors network traffic for suspicious patterns, while Host-based IDS focuses on individual devices or hosts for signs of malicious activities.
The Benefits of Using an IDS
- Early Threat Detection: An IDS can detect potential security breaches early on, allowing organisations to respond quickly and mitigate the impact of the intrusion.
- Enhanced Security: By continuously monitoring network and system activities, an IDS helps enhance overall security posture and reduces the risk of data breaches.
- Compliance Requirements: Many regulatory standards require the use of intrusion detection systems to ensure data protection and compliance with industry regulations.
- Anomaly Detection: IDS can identify abnormal behaviour within a network or system that may indicate a security threat, even if it’s a new or unknown attack vector.
Challenges Faced by IDS
While intrusion detection systems are powerful tools in cybersecurity defence, they also face challenges such as false positives (alerting on non-threatening events) and false negatives (failing to detect actual threats). It’s crucial for organisations to fine-tune their IDS configurations to reduce these issues.
In Conclusion
Implementing an Intrusion Detection System is a critical step towards strengthening your organisation’s cybersecurity posture. By proactively monitoring network and system activities for potential threats, an IDS plays a vital role in safeguarding sensitive data, maintaining compliance, and mitigating cyber risks. Investing in an effective IDS solution can help protect your organisation from the ever-evolving landscape of cyber threats.
Understanding Intrusion Detection Systems: Types, Tools, and Differences with IDS and IPS
- What are the 3 types of intrusion detection systems?
- Which tool is used for intrusion detection system?
- What are the four types of IDS?
- What is the IDS and IPS system?
- What is the difference between IDS and IPS?
- What is the difference between IDS and firewall?
What are the 3 types of intrusion detection systems?
When it comes to intrusion detection systems (IDS), there are three main types that organisations commonly utilise: Network-based IDS, Host-based IDS, and Hybrid IDS. Network-based IDS focuses on monitoring network traffic for suspicious activities, while Host-based IDS examines activities on individual devices or hosts for signs of intrusion. Hybrid IDS combines elements of both network and host-based detection methods to provide a more comprehensive security solution. Each type of IDS plays a crucial role in identifying and responding to potential security threats within an organisation’s IT infrastructure.
Which tool is used for intrusion detection system?
When it comes to implementing an Intrusion Detection System (IDS), various tools are available to assist in monitoring and analysing network or system activities for potential security threats. Commonly used tools for intrusion detection include Snort, Suricata, Bro IDS, and OSSEC. These tools offer different features and capabilities, allowing organisations to choose the one that best fits their specific security requirements. Selecting the right tool for an IDS is crucial in effectively detecting and responding to security incidents, helping enhance overall cybersecurity defences.
What are the four types of IDS?
When discussing the types of Intrusion Detection Systems (IDS), it is important to highlight the four main categories that these systems fall into: Network-based IDS, Host-based IDS, Signature-based IDS, and Anomaly-based IDS. Network-based IDS focuses on monitoring network traffic for suspicious patterns, while Host-based IDS analyses activities on individual devices or hosts. Signature-based IDS identifies known attack signatures by comparing network traffic to a database of predefined patterns, whereas Anomaly-based IDS detects deviations from normal behaviour within a network or system. Understanding the distinctions between these four types of IDS is crucial in selecting the most appropriate solution for enhancing cybersecurity defences.
What is the IDS and IPS system?
An Intrusion Detection System (IDS) and Intrusion Prevention System (IPS) are essential components of a robust cybersecurity strategy. While an IDS is designed to monitor network or system activities for potential security incidents and raise alerts when suspicious behaviour is detected, an IPS goes a step further by actively blocking or preventing identified threats in real-time. Essentially, an IDS acts as a watchdog that observes and reports on unusual activities, while an IPS functions as a proactive guardian that not only detects but also takes immediate action to thwart potential cyber threats before they can cause harm. Together, these systems work in tandem to enhance the overall security posture of an organisation and safeguard against various cyber risks.
What is the difference between IDS and IPS?
When discussing cybersecurity measures, a common query is the distinction between Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS). While both technologies are crucial for safeguarding networks, they serve distinct purposes. An IDS monitors and analyses network traffic to identify potential security incidents or policy violations, providing alerts for further investigation. On the other hand, an IPS goes a step further by not only detecting suspicious activities but also taking automated actions to block or prevent identified threats in real-time. In essence, an IDS acts as a passive observer, while an IPS acts as an active defender against cyber threats, enhancing overall network security. Understanding the variances between IDS and IPS is essential in implementing a comprehensive cybersecurity strategy tailored to specific organisational needs.
What is the difference between IDS and firewall?
When discussing the difference between an Intrusion Detection System (IDS) and a firewall, it is important to understand their distinct roles in cybersecurity. A firewall acts as a barrier between a trusted internal network and untrusted external networks, controlling incoming and outgoing network traffic based on predetermined security rules. On the other hand, an IDS monitors network or system activities for suspicious behaviour or policy violations, providing real-time alerts when potential threats are detected. While a firewall primarily focuses on preventing unauthorised access to the network, an IDS is designed to detect and respond to security incidents that may bypass the firewall’s defences. In essence, a firewall acts as a gatekeeper, while an IDS serves as a surveillance system within the network infrastructure.