The Importance of Identity and Access Management Services
In today’s digital age, where data breaches and cyber threats are on the rise, organisations must prioritise the security of their information assets. One crucial aspect of ensuring data security is implementing robust Identity and Access Management (IAM) services.
What is Identity and Access Management?
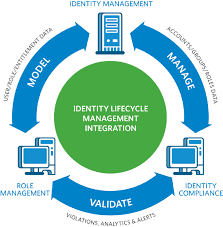
Identity and Access Management is a framework of policies, technologies, and processes that enables organisations to manage and control user identities and their access to resources within the IT infrastructure. IAM solutions help in securely managing user identities, enforcing access controls, and ensuring compliance with regulatory requirements.
The Benefits of IAM Services
Implementing IAM services offers several benefits to organisations:
- Enhanced Security: IAM solutions help in preventing unauthorised access to sensitive data by enforcing strict access controls.
- Improved Compliance: Organisations can meet regulatory requirements by implementing IAM solutions that provide audit trails and enforce policies.
- Increased Productivity: By streamlining user access processes, IAM services enable users to quickly obtain the necessary permissions for their roles.
- Centralised Management: IAM solutions provide a centralised platform for managing user identities, reducing administrative overhead.
- Risk Mitigation: By implementing IAM services, organisations can reduce the risk of insider threats and data breaches.
Choosing the Right IAM Solution
When selecting an IAM solution for your organisation, consider factors such as scalability, ease of integration with existing systems, compliance capabilities, reporting functionalities, and user experience. It is essential to choose a solution that aligns with your organisation’s security requirements and future growth plans.
In Conclusion
Identity and Access Management services play a critical role in safeguarding organisational data assets from cyber threats. By implementing robust IAM solutions, organisations can enhance security, improve compliance posture, streamline access management processes, and mitigate risks effectively. Investing in IAM services is not only a proactive measure but also a strategic decision towards building a secure digital environment.
Essential Insights into Identity and Access Management: Key Questions and Answers
- What is Identity and Access Management (IAM) and why is it important?
- How does Identity and Access Management help in enhancing cybersecurity?
- What are the key components of an Identity and Access Management system?
- How can Identity and Access Management services benefit my organisation?
- What are the common challenges faced when implementing Identity and Access Management solutions?
- How do Identity and Access Management systems ensure compliance with data protection regulations?
- What factors should organisations consider when selecting an Identity and Access Management solution?
What is Identity and Access Management (IAM) and why is it important?
Identity and Access Management (IAM) is a comprehensive framework of policies, technologies, and processes that organisations utilise to manage user identities and control their access to resources within the IT infrastructure. IAM plays a crucial role in enhancing data security by ensuring that only authorised individuals have access to sensitive information, thereby reducing the risk of data breaches and insider threats. By enforcing strict access controls, IAM solutions help organisations comply with regulatory requirements and maintain a secure digital environment. In essence, IAM is vital for safeguarding organisational data assets, improving compliance posture, streamlining access management processes, and mitigating risks effectively in today’s evolving cybersecurity landscape.
How does Identity and Access Management help in enhancing cybersecurity?
Identity and Access Management (IAM) plays a pivotal role in enhancing cybersecurity by providing a comprehensive framework for managing user identities and controlling their access to critical resources within an organisation’s IT infrastructure. By implementing IAM solutions, businesses can enforce strict access controls, authenticate users effectively, and monitor user activities in real-time. This proactive approach helps in preventing unauthorised access to sensitive data, reducing the risk of insider threats and external cyber attacks. IAM also aids in ensuring compliance with regulatory requirements by maintaining audit trails and enforcing security policies. Overall, IAM acts as a robust security layer that strengthens an organisation’s cybersecurity posture by safeguarding against potential vulnerabilities and mitigating risks associated with identity-related breaches.
What are the key components of an Identity and Access Management system?
In an Identity and Access Management (IAM) system, several key components work together to ensure secure and efficient management of user identities and access rights. These components typically include authentication mechanisms, which verify the identity of users through methods like passwords, biometrics, or multi-factor authentication. Authorisation controls determine the level of access granted to users based on their roles and permissions. User provisioning and deprovisioning tools manage the creation, modification, and removal of user accounts across systems. Additionally, audit and reporting functionalities track user activities for compliance purposes and security monitoring. Centralised directories such as LDAP or Active Directory store user information, while Single Sign-On (SSO) capabilities streamline user access to multiple applications with a single set of credentials. Together, these components form a comprehensive IAM system that enhances security, compliance, and operational efficiency within an organisation’s IT infrastructure.
How can Identity and Access Management services benefit my organisation?
Identity and Access Management (IAM) services offer a multitude of benefits to organisations. By implementing IAM solutions, your organisation can significantly enhance its security posture by ensuring that only authorised individuals have access to sensitive data and resources. IAM services also help in improving compliance with regulatory requirements by providing audit trails and enforcing access policies. Furthermore, IAM solutions streamline user access processes, leading to increased productivity and reduced administrative overhead. Overall, investing in IAM services can empower your organisation to mitigate risks, enhance operational efficiency, and safeguard critical information assets effectively.
What are the common challenges faced when implementing Identity and Access Management solutions?
When organisations embark on implementing Identity and Access Management (IAM) solutions, they often encounter common challenges that can impact the success of the deployment. One prevalent issue is the complexity of integrating IAM systems with existing IT infrastructure, which can lead to compatibility issues and disruptions in user access. Another challenge is ensuring a balance between security and user convenience, as overly stringent access controls may hinder productivity. Additionally, managing the lifecycle of user identities, such as provisioning and deprovisioning access rights effectively, poses a significant challenge. Addressing these challenges requires careful planning, stakeholder engagement, and continuous monitoring to ensure a seamless implementation of IAM solutions that meet both security requirements and user needs.
How do Identity and Access Management systems ensure compliance with data protection regulations?
Identity and Access Management (IAM) systems play a vital role in ensuring compliance with data protection regulations by implementing robust security measures and access controls. These systems help organisations adhere to regulations such as the GDPR by managing user identities, enforcing authentication protocols, and controlling access to sensitive data based on predefined policies. IAM systems provide audit trails and reporting functionalities that enable organisations to monitor and track user activities, ensuring that data is accessed only by authorised individuals. By centralising identity management processes and enforcing strict access controls, IAM systems help organisations demonstrate compliance with data protection regulations and safeguard against potential breaches or non-compliance issues.
What factors should organisations consider when selecting an Identity and Access Management solution?
When organisations are evaluating Identity and Access Management solutions, several key factors should be taken into consideration to ensure the selection of the most suitable solution. Firstly, scalability is crucial, as the chosen IAM solution should be able to accommodate the organisation’s current needs and future growth. Integration capabilities with existing systems and applications are also important to ensure seamless operation across the IT infrastructure. Compliance features play a significant role in meeting regulatory requirements and maintaining data security standards. Additionally, robust reporting functionalities help in monitoring user activities and identifying potential security risks. User experience is another essential factor to consider, as a user-friendly IAM solution enhances productivity and adoption rates within the organisation. By carefully assessing these factors, organisations can make informed decisions when selecting an Identity and Access Management solution that aligns with their security objectives and operational requirements.