Article: Security Breach Detection Systems
The Importance of Security Breach Detection Systems
In today’s digital landscape, where cyber threats are constantly evolving and becoming more sophisticated, the need for robust security breach detection systems has never been more critical. These systems play a vital role in safeguarding organisations against malicious activities that could compromise their sensitive data and disrupt their operations.
How Security Breach Detection Systems Work
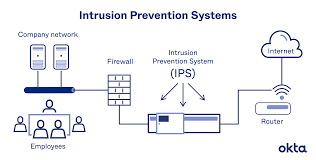
Security breach detection systems are designed to monitor network traffic, system logs, and user activities in real-time to identify any unusual or suspicious behaviour that may indicate a security breach. By analysing patterns and anomalies, these systems can detect potential threats early on, allowing organisations to take proactive measures to mitigate risks.
The Benefits of Security Breach Detection Systems
Implementing security breach detection systems offers several benefits, including:
- Early Threat Detection: These systems can detect security breaches as they occur, enabling rapid response and mitigation.
- Reduced Downtime: By identifying and addressing security incidents promptly, organisations can minimise downtime and maintain business continuity.
- Data Protection: Security breach detection systems help protect sensitive data from falling into the wrong hands, safeguarding the reputation and trust of the organisation.
- Regulatory Compliance: Many industries have strict regulations regarding data security. Implementing these systems can help organisations comply with regulatory requirements.
- Cost Savings: Detecting security breaches early can prevent costly data breaches and minimise the financial impact on the organisation.
In Conclusion
Security breach detection systems are indispensable tools for modern organisations looking to fortify their cybersecurity posture. By investing in these systems, businesses can stay one step ahead of cyber threats and protect their valuable assets from potential harm. In an era where cyber attacks are on the rise, implementing robust security breach detection systems is not just a best practice – it’s a necessity for ensuring long-term success and resilience in the face of evolving threats.
Seven Key Advantages of Security Breach Detection Systems: Bolstering Cyber Resilience and Protecting Business Integrity
- Early detection of security breaches
- Proactive threat mitigation
- Minimised downtime and business disruption
- Protection of sensitive data
- Enhanced regulatory compliance
- Cost savings by preventing data breaches
- Improved overall cybersecurity posture
Six Drawbacks of Security Breach Detection Systems: False Positives, Complexity, High Costs, Resource Demands, Skill Dependency, and Privacy Issues
- False Positives
- Complexity
- Cost
- Resource Intensive
- Skill Dependency
- Privacy Concerns
Early detection of security breaches
One significant advantage of security breach detection systems is their ability to provide early detection of security breaches. By monitoring network traffic, system logs, and user activities in real-time, these systems can swiftly identify any unusual or suspicious behaviour that may indicate a potential security breach. Early detection allows organisations to respond promptly to mitigate risks, minimise the impact of the breach, and prevent further damage to their systems and data. This proactive approach not only enhances the organisation’s cybersecurity posture but also helps maintain business continuity by addressing threats before they escalate.
Proactive threat mitigation
One significant advantage of security breach detection systems is their ability to facilitate proactive threat mitigation. By continuously monitoring network activities and analysing data for any signs of potential security breaches, these systems enable organisations to detect threats early on and take immediate action to mitigate risks before they escalate. This proactive approach not only helps in preventing security incidents but also minimises the impact of breaches, enhancing overall cybersecurity resilience and safeguarding sensitive data from malicious actors.
Minimised downtime and business disruption
One significant advantage of security breach detection systems is their ability to minimise downtime and business disruption. By promptly identifying and addressing security incidents, these systems help organisations mitigate the impact of potential breaches on their operations. With swift detection and response mechanisms in place, businesses can swiftly contain threats, restore normalcy to their systems, and ensure uninterrupted productivity. This proactive approach not only safeguards the continuity of operations but also enhances overall resilience against cybersecurity threats, allowing businesses to maintain a competitive edge in today’s dynamic digital landscape.
Protection of sensitive data
One significant advantage of security breach detection systems is their ability to protect sensitive data from falling into the wrong hands. By continuously monitoring network traffic and user activities, these systems can swiftly identify any suspicious behaviour that may indicate a potential security breach. This proactive approach not only helps in detecting and mitigating security incidents promptly but also ensures that confidential information remains secure, safeguarding the reputation and trust of the organisation.
Enhanced regulatory compliance
One significant advantage of security breach detection systems is their ability to enhance regulatory compliance for organisations. By implementing these systems, businesses can better adhere to industry-specific regulations and data protection laws. The real-time monitoring and analysis capabilities of these systems enable companies to quickly identify and respond to security incidents, ensuring that they meet the stringent requirements set forth by regulatory bodies. This proactive approach not only helps in avoiding costly non-compliance penalties but also instils trust among customers and stakeholders by demonstrating a commitment to protecting sensitive information in accordance with legal mandates.
Cost savings by preventing data breaches
One significant advantage of security breach detection systems is the potential for cost savings by preventing data breaches. By identifying and addressing security incidents in their early stages, organisations can avoid the financial repercussions associated with data breaches, such as regulatory fines, legal fees, remediation costs, and reputational damage. Investing in robust security breach detection systems not only enhances the overall cybersecurity posture of an organisation but also helps mitigate the financial impact of potential breaches, ultimately leading to long-term cost savings and preserving the integrity of the business.
Improved overall cybersecurity posture
An essential benefit of security breach detection systems is the significant enhancement they bring to an organisation’s overall cybersecurity posture. By continuously monitoring network activities and swiftly identifying potential security breaches, these systems bolster the organisation’s ability to proactively address vulnerabilities and mitigate risks. This proactive approach not only strengthens the resilience of the IT infrastructure but also instils a culture of heightened awareness and readiness against evolving cyber threats. Ultimately, improved overall cybersecurity posture achieved through the implementation of breach detection systems reinforces the organisation’s ability to safeguard critical assets and maintain operational continuity in an increasingly digital world.
False Positives
One significant drawback of security breach detection systems is the occurrence of false positives. These systems, while effective in flagging potential security threats, can sometimes produce false alarms, indicating the presence of a threat where none actually exists. This can result in wasted time and resources as security teams are forced to investigate and respond to non-existent or benign issues, diverting their attention away from genuine security incidents. False positives not only create unnecessary workloads but also have the potential to undermine confidence in the system’s accuracy and reliability.
Complexity
The complexity involved in implementing and managing security breach detection systems poses a significant challenge for organisations. These systems often require specialised knowledge and expertise to set up effectively, as well as ongoing maintenance to ensure optimal performance. The intricacies of configuring and fine-tuning these systems can be daunting, especially for those without a background in cybersecurity. Moreover, the ever-evolving nature of cyber threats demands constant updates and adjustments to the system, adding to the complexity of maintenance. Navigating through this intricate process can be time-consuming and resource-intensive, highlighting a notable drawback of security breach detection systems in terms of their complexity.
Cost
One notable drawback of security breach detection systems is the associated cost. High-quality systems often come with a hefty price tag, encompassing not only the initial acquisition but also deployment and ongoing maintenance expenses. For many organisations, this financial commitment can be substantial, posing a challenge in terms of budget allocation and resource management. The investment required to implement top-tier security breach detection systems may deter some businesses from fully embracing these crucial cybersecurity measures, potentially leaving them vulnerable to sophisticated cyber threats.
Resource Intensive
One significant drawback of security breach detection systems is their resource-intensive nature. These systems often require substantial computing resources to continuously monitor and analyse network traffic and system data. As a result, they may compete for resources with other critical IT operations, leading to potential performance issues and slowdowns in overall system functionality. Organisations must carefully balance the need for robust security measures with the impact on system performance when implementing such resource-intensive security solutions.
Skill Dependency
One significant drawback of security breach detection systems is the skill dependency it entails. Effectively utilising these systems typically necessitates personnel with expertise in cybersecurity, well-versed in best practices and incident response protocols. Without skilled individuals to operate and interpret the data generated by these systems, organisations may struggle to identify and respond promptly to security breaches, leaving their networks vulnerable to potential threats. This skill dependency can pose a challenge for businesses that lack the resources or expertise to maintain a proficient cybersecurity team, highlighting a potential barrier to maximising the benefits of security breach detection systems.
Privacy Concerns
Constant monitoring by security breach detection systems may raise privacy concerns among employees or individuals whose activities are being monitored. The intrusive nature of continuous surveillance can lead to feelings of discomfort and a sense of being constantly scrutinised. Employees may worry about their personal information being accessed or their every move being tracked, potentially leading to a decrease in morale and productivity. Balancing the need for robust security measures with respect for individual privacy rights is crucial to maintain a positive work environment and uphold ethical standards within an organisation.