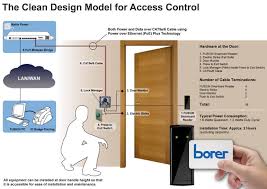
The Importance of Access Management Systems in Modern Businesses
Access management systems play a crucial role in ensuring the security and efficiency of modern businesses. In today’s digital age, where data breaches and cyber threats are prevalent, having robust access controls is essential to protect sensitive information and maintain regulatory compliance.
What is an Access Management System?
An access management system is a set of processes and technologies that govern how users are granted access to resources within an organisation’s IT infrastructure. This includes controlling who can access what information, when they can access it, and under what conditions.
The Benefits of Access Management Systems
Implementing an effective access management system offers several benefits to businesses:
- Enhanced Security: By enforcing strict access controls, organisations can prevent unauthorised users from accessing sensitive data or systems.
- Improved Compliance: Access management systems help businesses comply with regulations such as GDPR, HIPAA, or PCI DSS by ensuring that only authorised individuals have access to confidential information.
- Increased Productivity: By streamlining the process of granting and revoking access rights, employees can focus on their tasks without delays caused by administrative hurdles.
- Audit Trail: Access management systems provide detailed logs of user activities, which are invaluable for forensic investigations in case of security incidents.
Types of Access Management Systems
There are various types of access management systems available, including:
- Role-Based Access Control (RBAC): Users are assigned roles with specific permissions based on their job functions.
- Mandatory Access Control (MAC): Access rights are determined by system administrators and cannot be changed by users.
- Single Sign-On (SSO): Users can log in once to access multiple applications or systems without needing to re-enter credentials.
- Multi-Factor Authentication (MFA): Requires users to provide additional verification beyond passwords, such as biometrics or tokens.
Conclusion
In conclusion, implementing an effective access management system is essential for protecting sensitive data, maintaining compliance with regulations, and improving overall security posture. Businesses that invest in robust access controls not only reduce the risk of data breaches but also enhance operational efficiency and build trust with customers. As cyber threats continue to evolve, having a comprehensive access management strategy is critical for the long-term success of any organisation.
Contact us today to learn more about how our advanced access management solutions can help secure your business’s digital assets.
Top 6 Benefits of Implementing an Access Management System
- Enhanced security by preventing unauthorised access to sensitive data
- Improved compliance with regulations such as GDPR and HIPAA
- Increased productivity through streamlined access rights management
- Detailed audit trails for monitoring user activities and detecting anomalies
- Customisable access controls based on roles and responsibilities
- Integration with multi-factor authentication for added security
Seven Drawbacks of Access Management Systems: Challenges and Considerations
- Complex Implementation
- User Resistance
- Costly Maintenance
- Risk of Misconfigurations
- User Experience Issues
- Integration Challenges
- Potential for Single Point of Failure
Enhanced security by preventing unauthorised access to sensitive data
Enhanced security is a key advantage of access management systems, as they effectively prevent unauthorised access to sensitive data within an organisation’s IT infrastructure. By implementing strict access controls and authentication mechanisms, businesses can significantly reduce the risk of data breaches and cyber attacks. This proactive approach ensures that only authorised individuals have the necessary permissions to view or modify confidential information, safeguarding valuable assets and protecting the integrity of the organisation’s data.
Improved compliance with regulations such as GDPR and HIPAA
One of the key benefits of implementing an access management system is the improved compliance with regulations such as GDPR and HIPAA. By setting up strict access controls and ensuring that only authorised individuals have access to sensitive data, businesses can align with the requirements outlined in these regulatory frameworks. Access management systems help organisations demonstrate accountability and transparency in handling personal or healthcare information, reducing the risk of non-compliance penalties and safeguarding the privacy rights of individuals.
Increased productivity through streamlined access rights management
One significant advantage of an access management system is the increased productivity it brings through streamlined access rights management. By efficiently managing who has access to what resources within an organisation’s IT infrastructure, employees can focus on their core tasks without unnecessary delays or administrative obstacles. This streamlined approach not only saves time but also ensures that individuals have the appropriate level of access required to perform their duties effectively. As a result, businesses can operate more smoothly and efficiently, leading to improved overall productivity and performance.
Detailed audit trails for monitoring user activities and detecting anomalies
One significant advantage of implementing an access management system is the provision of detailed audit trails that enable the monitoring of user activities and the timely detection of anomalies. By maintaining comprehensive logs of user interactions within the system, organisations can track who accessed what information, when they did so, and from where. This level of visibility not only aids in identifying potential security breaches or suspicious behaviour but also facilitates compliance with regulatory requirements by providing a transparent record of user actions. The ability to proactively monitor user activities and swiftly respond to any irregularities enhances overall security posture and strengthens the organisation’s defences against potential threats.
Customisable access controls based on roles and responsibilities
One significant advantage of an access management system is the ability to customise access controls based on roles and responsibilities within an organisation. By implementing role-based access control (RBAC), businesses can assign specific permissions to users according to their job functions, ensuring that individuals only have access to the resources necessary for their tasks. This granular level of control not only enhances security by limiting exposure to sensitive data but also streamlines workflow efficiency by providing employees with the appropriate level of access required to fulfil their responsibilities effectively.
Integration with multi-factor authentication for added security
Integration with multi-factor authentication is a significant advantage of access management systems, enhancing security measures by requiring users to provide additional verification beyond passwords. By implementing multi-factor authentication as part of the access control process, organisations add an extra layer of protection against unauthorised access attempts. This approach significantly reduces the risk of compromised credentials and strengthens overall security posture, ensuring that only legitimate users with verified identities can access sensitive information and systems.
Complex Implementation
One significant drawback of access management systems is the complexity involved in their implementation. Establishing an access management system can be a time-consuming process that demands a high level of expertise. Organisations may face challenges in configuring the system to align with their specific requirements, integrating it with existing infrastructure, and ensuring seamless user experience. The need for skilled professionals to oversee the implementation phase can lead to delays and increased costs, making it a barrier for some businesses seeking to enhance their security measures through access controls.
User Resistance
One significant con of access management systems is user resistance, where employees may be hesitant or resistant to changes in access controls. This resistance can stem from various factors, such as fear of increased complexity, concerns about workflow disruptions, or simply a reluctance to adapt to new security measures. User resistance can pose challenges during the adoption phase of an access management system implementation, potentially delaying the process and hindering the system’s effectiveness. Addressing employee concerns through effective communication, training programmes, and highlighting the benefits of enhanced security can help mitigate user resistance and facilitate smoother integration of access controls within the organisation.
Costly Maintenance
One significant drawback of access management systems is the costly maintenance involved. Ongoing upkeep and updates of the system can result in additional expenses for the organisation. From software upgrades to regular monitoring and troubleshooting, the financial burden of maintaining an access management system can add up over time. These costs may include licensing fees, training for IT staff, and hiring external experts for technical support, making it a considerable investment that organisations need to factor into their budget planning.
Risk of Misconfigurations
One significant con of access management systems is the risk of misconfigurations. Incorrectly configured access controls can create security vulnerabilities within an organisation’s IT infrastructure, potentially exposing sensitive data to unauthorised users. These misconfigurations can result in data breaches, where malicious actors exploit loopholes in the system to gain access to confidential information. It is crucial for businesses to regularly review and update their access management settings to mitigate the risk of misconfigurations and safeguard their data from potential security threats.
User Experience Issues
User Experience can be a significant con of access management systems when overly restrictive access policies are in place. While security is paramount, excessively strict controls can impede productivity and lead to user frustration. When users encounter frequent access denials or cumbersome authentication processes, their efficiency and morale may suffer. Striking a balance between security and usability is crucial to ensure that access management systems enhance, rather than hinder, the overall user experience within an organisation.
Integration Challenges
Integration Challenges: One significant drawback of access management systems is the potential for compatibility issues with existing systems or applications when implementing them. This can lead to disruptions in operations, delays in deployment, and additional costs associated with resolving compatibility issues. Ensuring seamless integration between the access management system and other IT infrastructure components is crucial to avoid hindering productivity and user experience. Addressing these integration challenges requires careful planning, coordination, and possibly customisation to align the access management system with the organisation’s existing technology stack effectively.
Potential for Single Point of Failure
One significant drawback of access management systems is the potential for a single point of failure. In the event that the access management system encounters downtime or malfunctions, it has the capacity to disrupt operations throughout the entire organisation. This vulnerability highlights the critical importance of ensuring the reliability and redundancy of access management systems to mitigate the risk of such disruptions. Organizations must implement robust contingency plans and backup measures to address this con effectively and maintain seamless operations even in the face of system failures.