The Importance of Active Directory Assessment
Active Directory is a crucial component of many organisations’ IT infrastructure, serving as the central repository for user accounts, group policies, and security settings. As businesses grow and evolve, it is essential to regularly assess the health and security of their Active Directory environment.
Why Conduct an Active Directory Assessment?
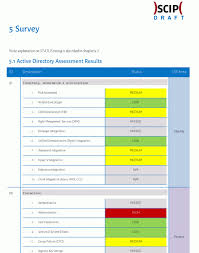
An Active Directory assessment involves evaluating various aspects of the directory service to ensure it is optimally configured, secure, and compliant with best practices. Here are some key reasons why conducting regular assessments is vital:
- Security: Assessing Active Directory helps identify potential security vulnerabilities and misconfigurations that could be exploited by malicious actors. By proactively addressing these issues, organisations can enhance their overall security posture.
- Performance: An assessment can reveal performance bottlenecks or inefficiencies within the Active Directory infrastructure. By identifying and addressing these issues, organisations can improve system performance and user experience.
- Compliance: Many industries have specific regulatory requirements regarding data security and access control. Regular assessments help ensure that the Active Directory environment meets compliance standards and avoids costly penalties.
- Risk Management: By assessing Active Directory regularly, organisations can better understand and mitigate risks associated with user access, authentication protocols, and data integrity.
Key Components of an Active Directory Assessment
An effective Active Directory assessment typically includes the following components:
- Security Audit: Evaluating security settings, group policies, permissions, and access controls to identify vulnerabilities.
- User Account Review: Reviewing user account permissions, inactive accounts, and privileged access to ensure proper user management.
- Password Policy Evaluation: Assessing password complexity requirements, expiration policies, and enforcement mechanisms to prevent unauthorised access.
The Benefits of Regular Assessments
Regularly assessing your Active Directory environment offers several benefits:
- Risk Mitigation: Identifying and addressing potential risks before they are exploited helps mitigate security threats.
- Improved Performance: Optimising configuration settings based on assessment findings can enhance system performance.
In conclusion, conducting regular assessments of your Active Directory environment is essential for maintaining a secure, efficient IT infrastructure. By identifying vulnerabilities, ensuring compliance with regulations, and proactively managing risks, organisations can safeguard their data assets and maintain operational continuity.
9 Essential Tips for Conducting a Comprehensive Active Directory Assessment
- Ensure all domain controllers are properly patched and up-to-date.
- Review group policies for security best practices and compliance requirements.
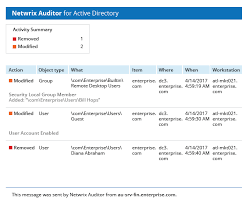
- Check for any inactive or orphaned user accounts and disable or remove them.
- Audit privileged groups and ensure proper access controls are in place.
- Monitor replication between domain controllers to detect any issues early on.
- Review DNS configurations to ensure proper name resolution within the network.
- Perform regular backups of Active Directory data to prevent data loss.
- Conduct regular security assessments to identify vulnerabilities and weaknesses.
- Train IT staff on best practices for managing Active Directory effectively.
Ensure all domain controllers are properly patched and up-to-date.
To ensure the security and reliability of your Active Directory environment, it is crucial to verify that all domain controllers are appropriately patched and kept up-to-date with the latest software updates. By maintaining current patches, you can address known vulnerabilities, enhance system stability, and minimise the risk of potential security breaches. Regularly updating domain controllers not only strengthens the overall security posture of your network but also ensures that your Active Directory infrastructure operates smoothly and efficiently.
Review group policies for security best practices and compliance requirements.
When conducting an Active Directory assessment, it is crucial to review group policies to ensure adherence to security best practices and compliance requirements. Group policies dictate user access, permissions, and security settings within the network, making them a critical component of maintaining a secure IT environment. By thoroughly examining and updating group policies based on established best practices and regulatory standards, organisations can enhance their overall security posture, mitigate risks, and ensure compliance with industry regulations. Regularly reviewing group policies is essential for proactively addressing potential vulnerabilities and maintaining a robust Active Directory infrastructure.
Check for any inactive or orphaned user accounts and disable or remove them.
When conducting an Active Directory assessment, it is crucial to check for any inactive or orphaned user accounts and take appropriate action by disabling or removing them. Inactive or orphaned accounts pose a security risk as they may provide unauthorized access to the network. By identifying and addressing these accounts, organisations can enhance their security posture, reduce the attack surface, and ensure that only authorised users have access to resources within the Active Directory environment. Regularly reviewing and managing user accounts is a fundamental step in maintaining a secure and well-organised directory service.
Audit privileged groups and ensure proper access controls are in place.
When conducting an Active Directory assessment, it is crucial to audit privileged groups and verify that appropriate access controls are implemented. Privileged groups hold significant authority within the network, making them prime targets for potential security breaches. By regularly reviewing and monitoring these groups, organisations can identify any anomalies or unauthorized access, thus strengthening the overall security posture of their Active Directory environment. Ensuring proper access controls are in place helps prevent unauthorised actions and minimises the risk of insider threats, ultimately safeguarding sensitive data and maintaining the integrity of the network.
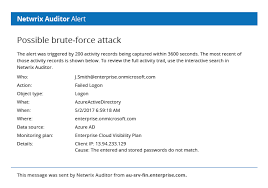
Monitor replication between domain controllers to detect any issues early on.
Monitoring replication between domain controllers is a crucial tip in Active Directory assessment. By keeping a close eye on the replication process, organisations can detect any issues early on and address them promptly. Timely detection of replication issues helps prevent data inconsistencies, ensures data integrity across the network, and enhances the overall reliability of the Active Directory environment. Proactive monitoring of replication can minimise downtime, improve system performance, and contribute to a more secure and efficient IT infrastructure.
Review DNS configurations to ensure proper name resolution within the network.
It is crucial to review DNS configurations as part of an Active Directory assessment to guarantee proper name resolution within the network. DNS (Domain Name System) plays a vital role in translating domain names into IP addresses, facilitating seamless communication between devices on the network. By ensuring that DNS configurations are accurate and up-to-date, organisations can prevent connectivity issues, improve network performance, and maintain the integrity of their Active Directory environment. Conducting regular reviews of DNS settings helps identify and rectify any misconfigurations that could impact the overall functionality and security of the network infrastructure.
Perform regular backups of Active Directory data to prevent data loss.
Performing regular backups of Active Directory data is a crucial tip to prevent data loss and ensure business continuity. By backing up critical information such as user accounts, group policies, and security settings, organisations can safeguard against unforeseen events like system failures, cyber attacks, or accidental deletions. Regular backups not only help in restoring data quickly in case of emergencies but also contribute to maintaining the integrity and availability of Active Directory services. By following this best practice, businesses can minimise the risk of data loss and ensure smooth operations in their IT environment.
Conduct regular security assessments to identify vulnerabilities and weaknesses.
Conducting regular security assessments is a fundamental tip for maintaining a robust Active Directory environment. By consistently evaluating the system for vulnerabilities and weaknesses, organisations can proactively identify potential security risks before they are exploited by malicious actors. This practice not only helps in strengthening the overall security posture but also enables timely remediation of any identified issues, ensuring a more resilient and secure Active Directory infrastructure.
Train IT staff on best practices for managing Active Directory effectively.
To enhance the effectiveness of Active Directory assessment, it is crucial to train IT staff on best practices for managing Active Directory efficiently. By providing comprehensive training on security protocols, user management, group policies, and compliance standards, IT personnel can better understand the complexities of Active Directory and implement proactive measures to ensure its optimal performance and security. Investing in staff training not only improves the overall management of Active Directory but also strengthens the organisation’s ability to identify and address potential vulnerabilities before they escalate into serious security threats.