The Importance of PKI in Identity and Access Management
Public Key Infrastructure (PKI) plays a crucial role in modern Identity and Access Management (IAM) systems, providing a secure framework for managing digital identities, authentication, and access control. In an increasingly interconnected digital world, where data breaches and cyber threats are prevalent, implementing robust PKI solutions is essential to safeguard sensitive information and ensure secure access to resources.
Understanding PKI
PKI is a comprehensive system that enables the creation, distribution, revocation, and management of digital certificates used for secure communication over networks. These certificates contain public keys that are paired with private keys held by authorised users or devices. By leveraging asymmetric encryption techniques, PKI establishes trust between entities in a networked environment.
The Role of PKI in IAM
Within an IAM framework, PKI serves as the foundation for authenticating users, devices, and services while ensuring data confidentiality and integrity. By issuing digital certificates to individuals or entities, organisations can verify their identities and control access to resources based on predefined policies. PKI also facilitates secure communication channels through encryption protocols like SSL/TLS.
Benefits of Integrating PKI into IAM
- Enhanced Security: PKI enhances security by enabling strong authentication mechanisms and encrypting data transmissions.
- Regulatory Compliance: Implementing PKI helps organisations comply with data protection regulations by securing sensitive information.
- User Convenience: Users can securely access resources without the need for complex passwords through PKI-based authentication methods.
- Risk Mitigation: By implementing robust identity verification processes using PKI, organisations can mitigate the risk of unauthorised access and data breaches.
Conclusion
In conclusion, integrating PKI into Identity and Access Management systems is essential for establishing a strong security posture in today’s digital landscape. By leveraging the capabilities of PKI to authenticate identities, control access privileges, and secure communication channels, organisations can effectively protect their assets from cyber threats while ensuring regulatory compliance. As technology continues to advance, the role of PKI in IAM will remain critical in safeguarding sensitive information and maintaining trust in online interactions.
Understanding PKI in Identity and Access Management: Key Components, Roles, and Examples
- What is PKI in IAM?
- What are the four main components of PKI?
- What does a PKI engineer do?
- What is PKI and how does it work?
- What are the 4 pillars of PKI?
- What is an example of a PKI?
- What is PKI in identity management?
What is PKI in IAM?
Public Key Infrastructure (PKI) in Identity and Access Management (IAM) is a fundamental framework that enables secure authentication, authorisation, and encryption within digital environments. PKI serves as the backbone of IAM systems by providing a robust mechanism for managing digital identities and ensuring secure access to resources. In essence, PKI in IAM utilises digital certificates, public and private key pairs, and encryption protocols to establish trust between entities, authenticate users, control access privileges, and facilitate secure communication channels. By integrating PKI into IAM strategies, organisations can enhance their security posture, mitigate risks of unauthorised access, and comply with regulatory requirements while maintaining a seamless user experience.
What are the four main components of PKI?
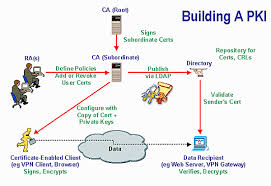
In the realm of PKI (Public Key Infrastructure) for identity and access management, understanding its fundamental components is crucial. The four main components of PKI include a Certificate Authority (CA), Registration Authority (RA), Certificate Store, and Key Management System. The Certificate Authority is responsible for issuing digital certificates that validate the identities of users or devices. The Registration Authority verifies the identity of entities before certificates are issued. The Certificate Store securely stores issued certificates for reference and validation purposes. Finally, the Key Management System oversees the generation, distribution, and protection of cryptographic keys used in encryption and authentication processes within the PKI framework. These components work together to establish a secure environment for managing digital identities and controlling access to resources effectively.
What does a PKI engineer do?
A PKI engineer is responsible for designing, implementing, and managing Public Key Infrastructure (PKI) systems within an organisation. Their role involves creating and maintaining the framework for issuing digital certificates, managing cryptographic keys, and ensuring secure authentication and data encryption processes. PKI engineers work to establish trust relationships between users, devices, and services by configuring certificate authorities, revocation mechanisms, and encryption protocols. They play a crucial role in safeguarding sensitive information, controlling access to resources based on identity verification, and ensuring compliance with security standards and regulations in the realm of Identity and Access Management.
What is PKI and how does it work?
Public Key Infrastructure (PKI) is a fundamental component of Identity and Access Management (IAM) systems, providing a secure framework for managing digital identities, authentication, and access control. PKI operates using asymmetric encryption techniques, where each entity in a network possesses a pair of cryptographic keys: a public key and a private key. The public key is distributed widely and used for encryption or verifying digital signatures, while the private key is kept confidential and used for decryption or signing messages. Through the issuance of digital certificates by Certificate Authorities (CAs), PKI establishes trust between entities by verifying their identities and enabling secure communication channels. This robust system ensures data confidentiality, integrity, and authenticity within an organisation’s network infrastructure.
What are the 4 pillars of PKI?
In the realm of PKI (Public Key Infrastructure) identity and access management, the concept of the “4 pillars of PKI” serves as a fundamental framework for understanding the core components that underpin a robust PKI system. These pillars encompass key elements such as Certificate Authority (CA), Registration Authority (RA), Certificate Revocation List (CRL), and Public Key Cryptography Standards (PKCS). The CA acts as a trusted entity responsible for issuing digital certificates, while the RA verifies user identities before certificate issuance. The CRL maintains a list of revoked certificates to ensure security, and PKCS defines standards for cryptographic operations within the PKI ecosystem. Understanding and implementing these pillars are essential for establishing a secure and efficient PKI infrastructure that effectively manages digital identities and access control.
What is an example of a PKI?
An example of a Public Key Infrastructure (PKI) is the use of digital certificates to secure online transactions in e-commerce platforms. In this scenario, a trusted Certificate Authority issues digital certificates to both the online merchant and the customer. The merchant’s digital certificate contains their public key, which is used to encrypt sensitive payment information before sending it over the internet. The customer’s browser can then verify the authenticity of the merchant’s certificate using the Certificate Authority’s public key, establishing a secure and encrypted communication channel for conducting safe online transactions. This application of PKI demonstrates how digital certificates play a vital role in verifying identities and ensuring secure access in online environments.
What is PKI in identity management?
Public Key Infrastructure (PKI) in identity management is a system that enables the secure management of digital identities, authentication processes, and access control within an organisation. PKI utilises digital certificates to verify the identities of users, devices, and services in a networked environment. These certificates contain public keys that are paired with private keys, allowing for secure communication and data exchange. By integrating PKI into identity management practices, organisations can establish trust, enhance security measures, and ensure compliance with regulatory requirements by effectively managing access to resources based on predefined policies.

I’m extremely inspired with your writing skills as well as with
the structure in your blog. Is this a paid subject or did you customize it yourself?
Either way stay up the excellent quality writing, it’s
uncommon to see a great blog like this one today. TikTok ManyChat!
Thank you for your kind words! We’re glad you enjoyed the content on PKI Identity and Access Management. Our focus is on providing valuable information to our readers in a clear and informative manner. Feel free to explore more articles on related topics for further insights.