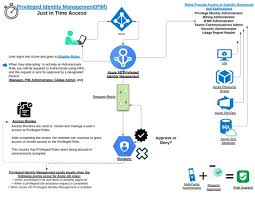
The Importance of Office 365 Privileged Identity Management
Office 365 has become an essential tool for businesses worldwide, offering a wide range of applications and services to enhance productivity and collaboration. However, with great power comes great responsibility, especially when it comes to managing privileged identities within the Office 365 environment.
Privileged identities refer to user accounts with elevated permissions that can access sensitive data and perform critical actions within Office 365. These accounts are often targeted by cybercriminals seeking to exploit vulnerabilities and gain unauthorised access to valuable information.
Office 365 Privileged Identity Management (PIM) is a crucial feature that helps organisations mitigate these risks by providing a secure way to manage, control, and monitor privileged access within their Office 365 environment. With PIM, administrators can enforce strict access controls, reduce the risk of insider threats, and ensure compliance with industry regulations.
Key Benefits of Office 365 Privileged Identity Management:
- Enhanced Security: By implementing just-in-time access and approval workflows, PIM reduces the exposure of privileged accounts to potential security threats.
- Granular Access Control: Administrators can assign temporary privileges based on specific tasks or roles, limiting the scope of what privileged users can do within Office 365.
- Audit Trail: PIM provides detailed logs and reports on all privileged access activities, allowing organisations to track changes and monitor suspicious behaviour effectively.
- Compliance Management: With PIM’s automated policy enforcement and reporting capabilities, organisations can easily demonstrate compliance with regulatory requirements related to privileged access management.
It is essential for businesses to recognise the significance of Office 365 Privileged Identity Management in safeguarding their critical data and maintaining a secure digital workspace. By leveraging the capabilities of PIM, organisations can proactively protect their Office 365 environment from potential security breaches and ensure the integrity of their sensitive information.
In conclusion, investing in Office 365 Privileged Identity Management is not only a proactive approach towards enhancing cybersecurity but also a strategic decision that reinforces trust among employees and stakeholders. By prioritising the security of privileged identities within Office 365, organisations can build a resilient defence against evolving cyber threats and safeguard their digital assets effectively.
Understanding Privileged Identity Management and Access Solutions in Office 365: FAQs on PIM and PAM
- What is privileged access management in Office 365?
- What is PIM in Microsoft 365?
- Does Microsoft offer a PAM solution?
- What is the difference between PIM and PAM in Office 365?
What is privileged access management in Office 365?
Privileged Access Management in Office 365 refers to the practice of controlling and monitoring access to sensitive resources and data within the Office 365 environment. It involves managing user accounts with elevated permissions, often referred to as privileged identities, to minimise the risk of security breaches and unauthorised activities. By implementing Privileged Access Management, organisations can enforce strict controls over who has access to critical information, limit the scope of privileges granted to users, and track all privileged access activities for auditing and compliance purposes. This proactive approach helps enhance security posture, reduce insider threats, and ensure that only authorised personnel can perform high-impact actions within Office 365.
What is PIM in Microsoft 365?
Privileged Identity Management (PIM) in Microsoft 365 is a robust security feature designed to help organisations manage and control access to critical resources within their Office 365 environment. PIM allows administrators to assign, monitor, and govern privileged roles effectively, reducing the risk of unauthorised access and potential security breaches. By implementing PIM, organisations can enforce just-in-time access, granular permissions, and audit trails for privileged accounts, enhancing overall security posture and compliance with regulatory standards. In essence, PIM in Microsoft 365 empowers businesses to proactively protect their sensitive data and maintain a secure digital workspace by strengthening their privileged identity management practices.
Does Microsoft offer a PAM solution?
One frequently asked question regarding Office 365 Privileged Identity Management is whether Microsoft offers a Privileged Access Management (PAM) solution. Microsoft does provide a PAM solution as part of its broader security offerings, which includes Azure AD Privileged Identity Management (PIM). Azure AD PIM allows organisations to manage, control, and monitor access to resources within their Azure environment, including Office 365. By utilising Azure AD PIM, businesses can enforce strict access controls for privileged accounts, reduce the risk of security breaches, and enhance overall security posture.
What is the difference between PIM and PAM in Office 365?
In the realm of Office 365 security, a common query revolves around distinguishing between Privileged Identity Management (PIM) and Privileged Access Management (PAM). While both concepts aim to bolster security by controlling access to sensitive resources, they operate in slightly different ways within the Office 365 environment. PIM specifically focuses on managing and monitoring privileged identities, offering features such as just-in-time access and temporary role assignments to minimise exposure to security risks. On the other hand, PAM encompasses a broader approach that includes not only identity management but also the governance and oversight of privileged access across various systems and applications. Understanding this distinction is crucial for organisations seeking to implement robust security measures within their Office 365 infrastructure.