The Importance of Identity & Access Management System in Modern Businesses
In today’s digital age, where cyber threats are constantly evolving, ensuring the security of sensitive data and resources is a top priority for businesses of all sizes. One crucial component of a robust cybersecurity strategy is the implementation of an Identity and Access Management (IAM) system.
What is Identity & Access Management?
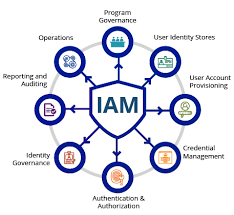
Identity and Access Management is a framework of policies and technologies that enables organisations to manage and control user identities and their access to various systems and applications within the IT infrastructure. It encompasses processes such as user authentication, authorisation, provisioning, deprovisioning, and access governance.
The Benefits of IAM System
Implementing an IAM system offers numerous benefits to businesses:
- Enhanced Security: IAM helps prevent unauthorised access to critical systems and data by ensuring that only authenticated users have the appropriate level of access.
- Improved Compliance: IAM systems assist in meeting regulatory requirements by providing detailed audit trails and enforcing security policies.
- Increased Productivity: By streamlining user onboarding processes and automating access requests, IAM reduces administrative burden and enhances operational efficiency.
- Cost Savings: Centralising identity management can lead to cost savings through reduced IT support overheads and mitigating the risk of security breaches.
- User Convenience: IAM systems offer users a seamless experience across multiple applications with single sign-on capabilities, enhancing user convenience without compromising security.
The Future of IAM
As businesses continue to digitalise their operations and adopt cloud-based services, the role of IAM becomes even more critical. The future of IAM lies in integrating advanced technologies such as biometrics, artificial intelligence, and machine learning to enhance authentication methods and adapt to evolving security threats.
In conclusion, implementing an Identity & Access Management system is essential for safeguarding sensitive data, ensuring regulatory compliance, enhancing operational efficiency, and protecting against cyber threats. By investing in a robust IAM framework, businesses can strengthen their overall cybersecurity posture in an increasingly interconnected world.
Understanding Identity & Access Management Systems: Key Concepts and Examples
- What is the purpose of the IAM system?
- What is CMS identity and access management system?
- What is an example of IAM?
- What is identity access management system?
What is the purpose of the IAM system?
The primary purpose of an Identity and Access Management (IAM) system is to securely manage and control the identities of users within an organisation and regulate their access to various systems, applications, and data resources. By implementing an IAM system, businesses can ensure that only authorised individuals have the appropriate level of access to sensitive information, thereby reducing the risk of data breaches and insider threats. IAM systems play a crucial role in enhancing security, streamlining user authentication processes, enforcing compliance with regulations, and improving overall operational efficiency within an IT environment.
What is CMS identity and access management system?
The CMS Identity and Access Management System, often abbreviated as CMS IAM, is a specialised solution designed to manage user identities and control access within the context of Content Management Systems (CMS). This system allows organisations to regulate user permissions, authenticate users securely, and monitor user activities within their CMS environment. By implementing CMS IAM, businesses can ensure that only authorised individuals have access to sensitive content, streamline user management processes, and enhance overall security measures within their content management infrastructure.
What is an example of IAM?
An example of an Identity and Access Management (IAM) system is Microsoft Azure Active Directory (AAD). AAD is a cloud-based identity management service that allows organisations to manage user identities and control access to various applications and resources within the Azure ecosystem. With AAD, administrators can set up user accounts, assign permissions, enforce security policies, and enable single sign-on for seamless access across multiple services. This example showcases how IAM systems like AAD play a crucial role in ensuring secure and efficient identity management in modern IT environments.
What is identity access management system?
An Identity and Access Management (IAM) system is a comprehensive framework that organisations use to manage and control user identities and their access to various systems and applications within the IT infrastructure. It involves a set of policies, processes, and technologies that govern user authentication, authorisation, provisioning, deprovisioning, and access governance. In essence, an IAM system serves as the gatekeeper that ensures only authenticated users have the appropriate level of access to critical resources while maintaining security, compliance, and operational efficiency across the organisation.