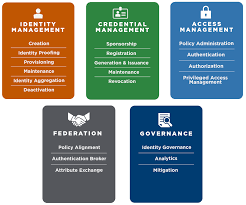
The Rise of Cloud Identity Management Solutions
In today’s digital age, businesses are increasingly turning to cloud-based solutions to streamline their operations and enhance security. One area that has seen significant growth is cloud identity management. Cloud identity management solutions offer a centralised approach to managing user identities, access rights, and security policies across an organisation’s cloud-based resources.
Benefits of Cloud Identity Management
Cloud identity management solutions provide several key benefits for modern businesses:
- Centralised Control: With cloud identity management, administrators can centrally manage user identities and access permissions across multiple cloud services and applications.
- Enhanced Security: By implementing strong authentication methods and access controls, cloud identity management helps prevent unauthorised access to sensitive data and resources.
- Scalability: Cloud identity management solutions can easily scale to accommodate the changing needs of a growing business without the need for extensive infrastructure upgrades.
- User Experience: Employees benefit from seamless access to the tools and resources they need, improving productivity and user satisfaction.
- Compliance: Cloud identity management helps businesses maintain compliance with data protection regulations by enforcing security policies and access controls.
Key Features of Cloud Identity Management Solutions
Some common features found in cloud identity management solutions include:
- Single Sign-On (SSO): Allows users to securely access multiple applications with a single set of credentials.
- Multi-Factor Authentication (MFA): Adds an extra layer of security by requiring users to provide multiple forms of verification before accessing resources.
- User Provisioning: Automates the process of creating, updating, and deleting user accounts across various systems.
- Password Management: Enables users to securely store and manage their passwords while enforcing password policies.
- Audit Trails: Provides detailed logs of user activities for compliance monitoring and security incident investigation.
The Future of Cloud Identity Management
As businesses continue to embrace cloud technologies, the demand for robust cloud identity management solutions is expected to grow. Advancements in artificial intelligence, machine learning, and biometric authentication are likely to further enhance the security and usability of these solutions. Organisations that prioritise implementing effective cloud identity management strategies will be better positioned to protect their data assets while enabling seamless collaboration and innovation in the digital realm.
Top 5 Tips for Enhancing Cloud Identity Management Solutions
- Implement multi-factor authentication for added security.
- Regularly review and update user access permissions to ensure least privilege.
- Integrate with single sign-on (SSO) solutions for seamless user experience.
- Utilise identity governance tools to monitor and manage user identities effectively.
- Ensure compliance with data protection regulations when managing cloud identities.
Implement multi-factor authentication for added security.
To enhance the security of your cloud identity management solution, it is advisable to implement multi-factor authentication. By requiring users to provide multiple forms of verification before accessing sensitive data and resources, such as a password combined with a unique code sent to their mobile device, you add an extra layer of protection against unauthorised access. Multi-factor authentication significantly reduces the risk of data breaches and strengthens overall security posture, making it an essential feature for safeguarding your organisation’s digital assets in the cloud.
Regularly review and update user access permissions to ensure least privilege.
Regularly reviewing and updating user access permissions is a crucial practice in cloud identity management solutions to uphold the principle of least privilege. By ensuring that users have only the necessary access rights to perform their job functions, organisations can minimise the risk of unauthorised data breaches and insider threats. Keeping access permissions up to date not only enhances security but also promotes efficient resource allocation and compliance with regulatory requirements. Regular audits of user permissions help maintain a robust security posture in the ever-evolving landscape of cloud-based environments.
Integrate with single sign-on (SSO) solutions for seamless user experience.
Integrating cloud identity management solutions with single sign-on (SSO) capabilities is a valuable tip for businesses seeking to enhance user experience and streamline access to cloud resources. By implementing SSO, users can securely log in once and gain access to multiple applications without the need to enter credentials repeatedly. This seamless authentication process not only improves user convenience but also strengthens security by reducing the risk of password fatigue and potential vulnerabilities associated with managing multiple login credentials. Embracing SSO as part of cloud identity management strategies can significantly boost productivity and satisfaction among employees while maintaining a high level of data protection across the organisation’s digital ecosystem.
Utilise identity governance tools to monitor and manage user identities effectively.
To maximise the efficiency and security of cloud identity management solutions, it is crucial to leverage identity governance tools that enable comprehensive monitoring and management of user identities. These tools provide organisations with the ability to enforce access controls, track user activities, and ensure compliance with security policies. By utilising identity governance tools, businesses can proactively identify and mitigate risks related to user access, streamline user provisioning processes, and maintain a clear audit trail of all identity-related actions. This proactive approach not only enhances security but also helps in optimising operational processes within the cloud environment.
Ensure compliance with data protection regulations when managing cloud identities.
It is crucial to ensure compliance with data protection regulations when managing cloud identities. By adhering to data protection laws and regulations, businesses can safeguard sensitive information stored in the cloud and mitigate the risk of data breaches. Implementing robust security measures, access controls, and encryption protocols not only helps protect user identities but also demonstrates a commitment to maintaining privacy and security standards. Compliance with data protection regulations in cloud identity management is essential for building trust with customers and stakeholders while minimising legal risks associated with non-compliance.