The Importance of Cryptography in Network Security
Cryptography plays a crucial role in ensuring the security and integrity of data transmitted over networks. In today’s interconnected world, where sensitive information is constantly being exchanged between devices and systems, robust cryptographic techniques are essential to protect this data from malicious actors.
Network security relies heavily on cryptography to provide confidentiality, integrity, authentication, and non-repudiation. By encrypting data using algorithms and keys, cryptography ensures that only authorised parties can access the information while preventing eavesdroppers from intercepting or tampering with the data.
One of the fundamental principles of cryptography is the use of encryption to convert plaintext data into ciphertext, making it unreadable without the corresponding decryption key. This process ensures that even if an attacker gains access to the encrypted data, they cannot decipher it without the proper key.
Furthermore, cryptographic protocols such as SSL/TLS are commonly used to secure communication over the internet. These protocols establish secure connections between clients and servers, encrypting data transmissions to prevent interception or modification by attackers.
Public key cryptography is another essential component of network security. It enables secure key exchange between parties without requiring them to share a secret key beforehand. This method is widely used in digital signatures and secure communication channels to verify identities and ensure message authenticity.
As cyber threats continue to evolve, cryptography remains a critical tool in safeguarding sensitive information across networks. By implementing strong encryption algorithms and secure protocols, organisations can mitigate risks and protect their data from unauthorised access or manipulation.
In conclusion, cryptography serves as a cornerstone of network security by providing mechanisms to secure data transmission, authenticate users, and maintain privacy in an increasingly interconnected digital landscape. With ongoing advancements in cryptographic techniques and technologies, organisations can stay ahead of cyber threats and uphold the confidentiality and integrity of their communications.
Core Principles of Cryptography in Networking Explained
The Triad of Cryptographic Types: A Guide to Understanding Cryptography
4. The Quadruple Foundations of Cryptography
- What is cryptography and network security?
- What are the principles of cryptography and network?
- What are the three types of cryptography?
- What are the 4 principles of cryptography?
What is cryptography and network security?
Cryptography and network security encompass the practices and technologies designed to protect data transmitted over networks from unauthorised access or manipulation. Cryptography involves the use of mathematical algorithms to encrypt data, ensuring that only intended recipients can decipher the information with the correct decryption key. Network security, on the other hand, focuses on implementing various measures to safeguard networks and their components from cyber threats, such as hackers and malware. Together, cryptography and network security form a crucial defence mechanism in safeguarding sensitive information and maintaining the integrity of digital communications in today’s interconnected world.
What are the principles of cryptography and network?
Understanding the principles of cryptography and network security is essential for ensuring the confidentiality, integrity, and authenticity of data transmitted over networks. Cryptography relies on key principles such as encryption, which transforms plaintext data into unreadable ciphertext using algorithms and keys. This process prevents unauthorised access to sensitive information by ensuring that only authorised parties possess the decryption key. In network security, cryptographic protocols play a vital role in establishing secure communication channels to protect data from interception or tampering. By adhering to these fundamental principles, organisations can enhance their cybersecurity posture and safeguard their digital assets against evolving threats in the interconnected world of technology.
What are the three types of cryptography?
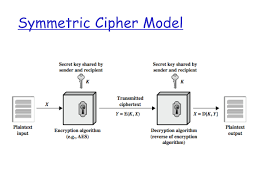
In the realm of cryptography and network security, there are three primary types of cryptographic techniques: symmetric key cryptography, asymmetric key cryptography, and hashing algorithms. Symmetric key cryptography involves using a single shared key for both encryption and decryption processes, making it efficient for securing data transmission within a closed system. Asymmetric key cryptography, on the other hand, utilises a pair of public and private keys for encryption and decryption, enabling secure communication between parties without the need to exchange secret keys beforehand. Hashing algorithms play a crucial role in data integrity by generating fixed-length hash values that uniquely represent input data, allowing for verification of data integrity and detecting tampering attempts. Each type of cryptography serves distinct purposes in safeguarding information and ensuring secure communication across networks.
What are the 4 principles of cryptography?
In the realm of cryptography and network security, understanding the four fundamental principles of cryptography is essential for ensuring the confidentiality and integrity of data transmissions. These principles include confidentiality, which involves encrypting data to prevent unauthorised access; integrity, which ensures that data remains unchanged during transmission; authentication, which verifies the identity of parties involved in communication; and non-repudiation, which prevents parties from denying their actions or transactions. By adhering to these core principles, cryptographic systems can effectively protect sensitive information and establish secure communication channels in digital environments.