The Importance of Active Directory Auditing in Ensuring IT Security
In today’s digital age, where data breaches and cyber attacks are becoming increasingly prevalent, the need for robust IT security measures is more critical than ever. One essential aspect of maintaining a secure IT environment is through active directory auditing.
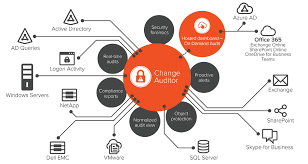
Active Directory is a crucial component of many organisations’ IT infrastructure, serving as a centralised database that stores information about users, computers, and resources within a network. It manages access control and permissions, making it a prime target for malicious actors seeking to exploit vulnerabilities.
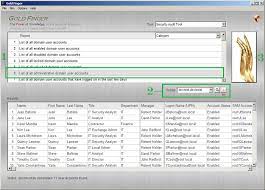
By implementing active directory auditing, organisations can proactively monitor and track all activities within their Active Directory environment. This includes user logins, file access, group policy changes, and more. By keeping a detailed record of these actions, administrators can quickly detect suspicious behaviour and potential security threats.
One of the key benefits of active directory auditing is its role in compliance management. Many industries are subject to strict regulations regarding data protection and privacy. By conducting regular audits of Active Directory activities, organisations can ensure they are meeting regulatory requirements and avoid costly penalties for non-compliance.
Furthermore, active directory auditing helps enhance overall IT security by providing valuable insights into potential weaknesses in the system. By analysing audit logs and reports, administrators can identify areas that require additional security measures or policy adjustments to mitigate risks effectively.
In conclusion, active directory auditing is an essential practice for any organisation looking to maintain a secure IT environment. By monitoring user activities, tracking changes, and ensuring compliance with regulations, organisations can significantly reduce the risk of data breaches and cyber attacks. Investing in robust auditing tools and practices is an investment in the long-term security and stability of your IT infrastructure.
Essential Tips for Effective Active Directory Auditing: Enhancing Security and Oversight
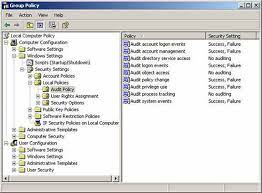
- Enable auditing on Active Directory to track changes and access.
- Regularly review audit logs for any suspicious activities.
- Limit the number of users with administrative privileges.
- Implement strong password policies for all users.
- Use multi-factor authentication for added security.
- Monitor account lockouts and failed login attempts.
- Educate employees on best practices for AD security.
- Keep AD servers updated with the latest security patches.
- Consider using third-party tools for enhanced auditing capabilities.
Enable auditing on Active Directory to track changes and access.
Enabling auditing on Active Directory is a crucial step in bolstering your organisation’s IT security posture. By activating auditing features, you can effectively track and monitor changes made to user accounts, permissions, group policies, and other critical elements within the Active Directory environment. This proactive approach not only helps in detecting unauthorised access attempts but also provides valuable insights into user activities, allowing administrators to swiftly respond to any suspicious behaviour and maintain the integrity of the network.
Regularly review audit logs for any suspicious activities.
It is crucial to regularly review audit logs for any suspicious activities as part of effective Active Directory auditing practices. By consistently monitoring user actions, file accesses, and system changes recorded in the audit logs, administrators can quickly identify anomalies or potential security threats. Timely detection of suspicious activities allows for prompt investigation and remediation, helping to bolster the overall security posture of the IT environment. Regular reviews of audit logs play a vital role in maintaining a proactive approach to cybersecurity and ensuring the integrity of the Active Directory system.
Limit the number of users with administrative privileges.
Limiting the number of users with administrative privileges is a crucial tip in active directory auditing to enhance IT security. By restricting access to only those who truly require elevated permissions, organisations can significantly reduce the risk of insider threats and unauthorised system changes. This practice not only minimises the potential for accidental misconfigurations but also makes it easier to track and monitor the activities of privileged users effectively. By implementing strict controls over administrative access, organisations can bolster their overall security posture and mitigate the likelihood of cyber attacks targeting critical systems and data.
Implement strong password policies for all users.
Implementing strong password policies for all users is a fundamental step in enhancing the security of your Active Directory environment. By requiring users to create complex passwords that include a mix of letters, numbers, and special characters, you can significantly reduce the risk of unauthorised access to sensitive data. Regularly updating passwords and enforcing password expiration policies further strengthens your defences against potential security breaches. Strong password practices not only protect individual user accounts but also contribute to the overall security posture of your organisation’s IT infrastructure.
Use multi-factor authentication for added security.
Implementing multi-factor authentication (MFA) is a highly recommended tip for enhancing the security of Active Directory auditing. By requiring users to provide multiple forms of verification before accessing the system, such as a password and a unique code sent to their mobile device, MFA adds an extra layer of protection against unauthorised access. This additional security measure significantly reduces the risk of compromised credentials and strengthens the overall integrity of the Active Directory environment.
Monitor account lockouts and failed login attempts.
Monitoring account lockouts and failed login attempts is a crucial aspect of active directory auditing. By keeping a close eye on these events, administrators can quickly identify potential security threats such as brute force attacks or unauthorised access attempts. Tracking account lockouts and failed logins allows for prompt investigation and remediation, helping to prevent security breaches and safeguard the integrity of the Active Directory environment. This proactive approach to monitoring user authentication activities enhances overall IT security and ensures that any suspicious behaviour is promptly addressed.
Educate employees on best practices for AD security.
Educating employees on best practices for Active Directory (AD) security is a crucial step in enhancing overall IT security within an organisation. By raising awareness about the importance of strong password management, avoiding phishing scams, and adhering to access control policies, employees can become active participants in safeguarding the integrity of the AD environment. Regular training sessions and reminders on security protocols can empower staff to recognise potential threats and take proactive measures to protect sensitive data stored in Active Directory. Ultimately, a well-informed workforce plays a vital role in fortifying the organisation’s defences against cyber threats and ensuring compliance with security standards.
Keep AD servers updated with the latest security patches.
To enhance the security of your Active Directory environment, it is crucial to keep AD servers updated with the latest security patches. Regularly applying security patches helps to address known vulnerabilities and protect against potential cyber threats. By staying up-to-date with software updates, organisations can strengthen their defences and minimise the risk of security breaches. Prioritising the timely installation of security patches is a proactive measure that contributes significantly to maintaining a secure and resilient Active Directory infrastructure.
Consider using third-party tools for enhanced auditing capabilities.
When it comes to active directory auditing, organisations should consider utilising third-party tools to enhance their auditing capabilities. Third-party tools often offer advanced features and functionalities that go beyond what native auditing tools provide. These tools can provide real-time monitoring, detailed reporting, customisable alerts, and integration with other security systems, allowing organisations to have a more comprehensive view of their Active Directory environment. By leveraging third-party tools, organisations can strengthen their security posture, improve compliance management, and proactively identify and mitigate potential security threats.